FirstBlood-#1013 — Default credentials on login page
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-08, lumbridge7 Level 4
reported:
Hello firstblood team!
Summary
Many web applications and hardware devices have default passwords for the built-in administrative account. Although in some cases these can be randomly generated, they are often static, meaning that they can be easily guessed or obtained by an attacker.
Additionally, when new users are created on the applications, these may have predefined passwords set. These could either be generated automatically by the application, or manually created by staff. In both cases, if they are not generated in a secure manner, the passwords may be possible for an attacker to guess or to brute force with a credentials wordlist such as https://github.com/danielmiessler/SecLists/tree/master/Passwords/Default-Credentials.
Steps to reproduce
- go to https://0a71d31af52a-lumbridge7.a.firstbloodhackers.com/login.php
- log in with the credentials admin:admin
- get access to the doctor dashboard
POC
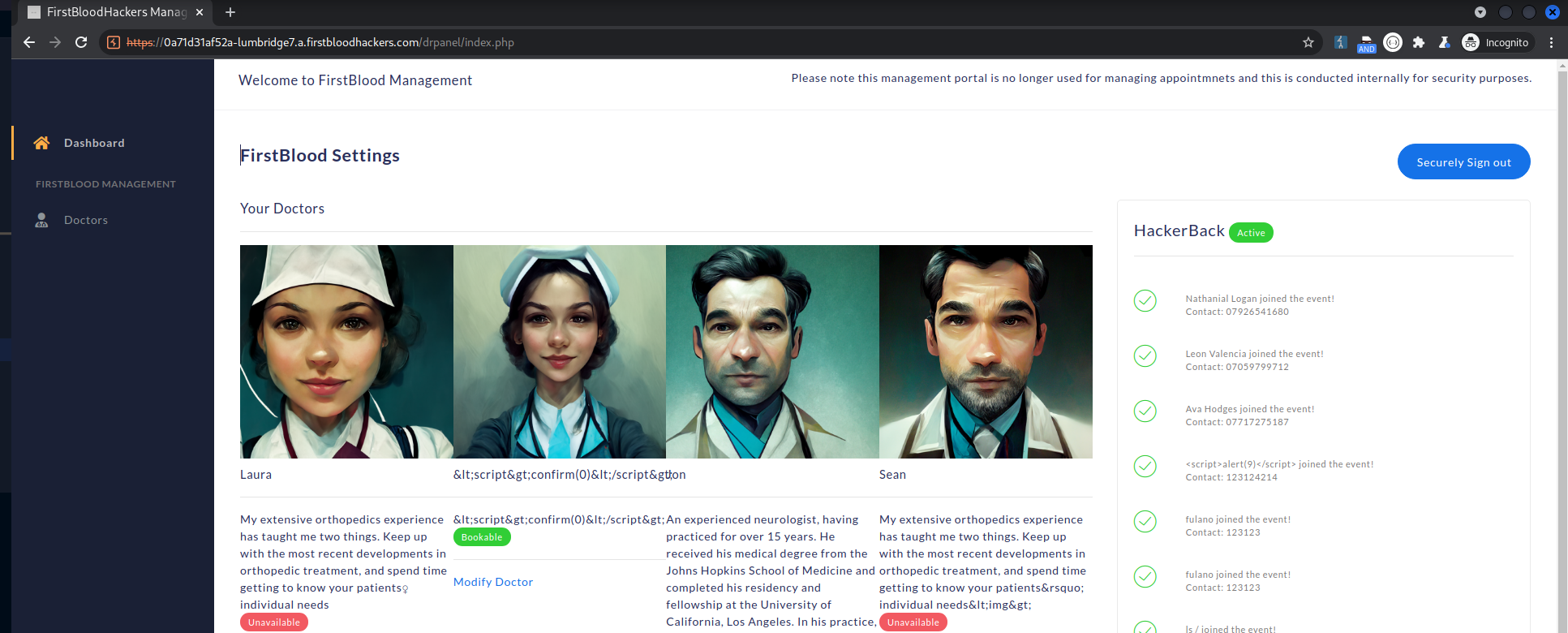
Impact
Anyone is able to access the doctor dashboard with administrative privileges by guessing or burteforcing the credentials and the drId.
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /login.php
Parameter: null
Payload: null
FirstBlood ID: 48
Vulnerability Type: Auth issues
The /drpanel/login.php endpoint contains weak credentials which allows users to access the admin panel (admin:admin)
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 