Purchase Membership
"It is very awesome indeed, allowed me to experience with a target that is similar to real ones, allowed me to interact with this awesome community around it, and built my confidence."
"I don't do a lot of CTF etc... due to the lack of realism but on this platform, the bugs are quite varied AND in a realistic environment, that's exactly what I'm looking for. I think this site is a good sequel for those who start on PortSwigger WebSecurity and / or TryHackMe."
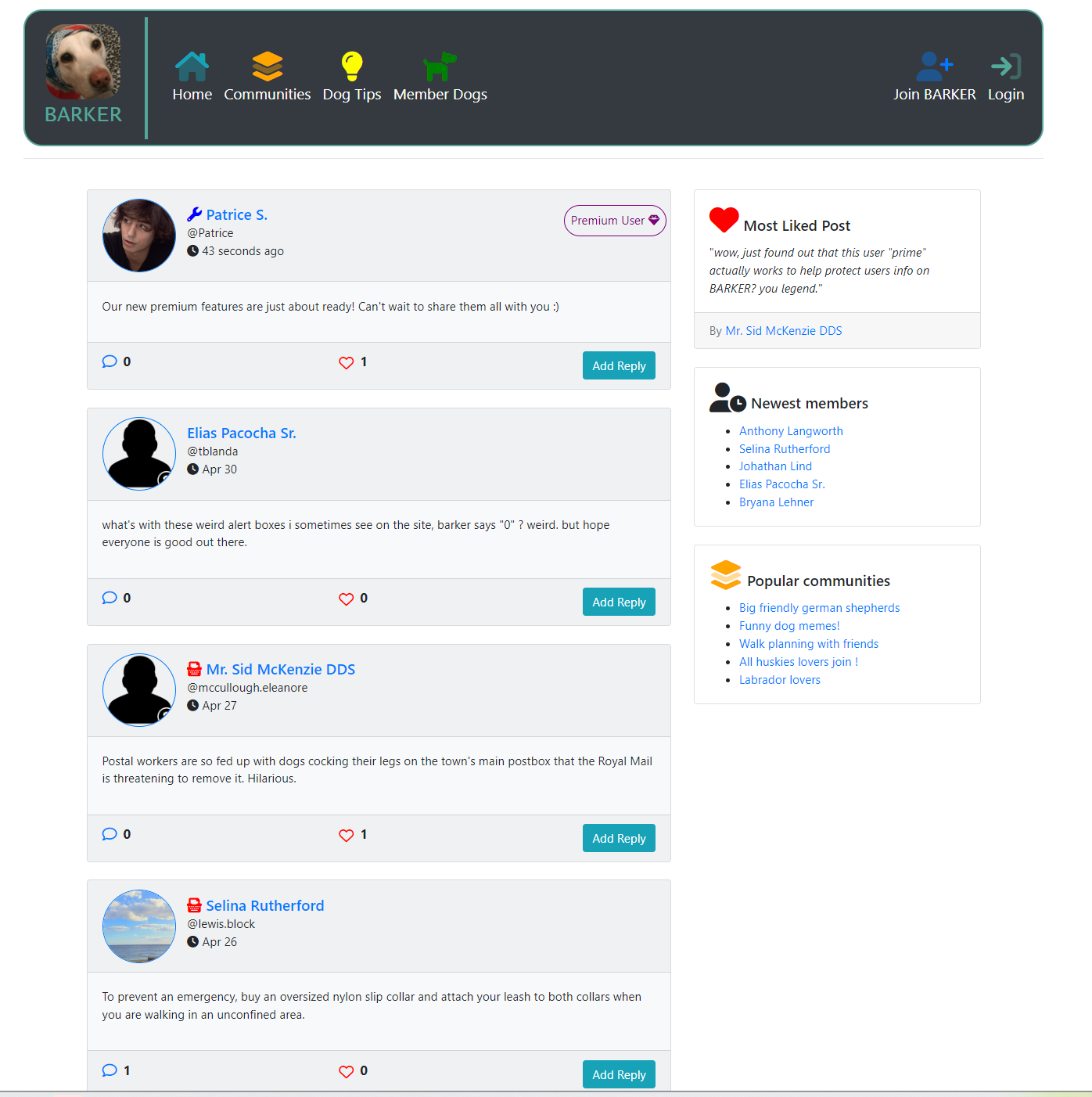

Practise hacking against a fully functioning web application named BARKER which contains over 100+ realistic findings you're likely to also find on bug bounty programs. Our bugs are designed from real world findings and our training platform is designed to help you gain the confidence to begin bug bounties.
BARKER is designed to put your web application knowledge & skills to the test as you're blindly hunting for functionality and features and testing them based on your knowledge around various vulnerability types, just like you would on a bug bounty program target!
Spend time learning how the various features work and then begin uncovering vulnerabilities hidden within, true hacker style! With over 100 vulnerabilities to discover, how many can you find?
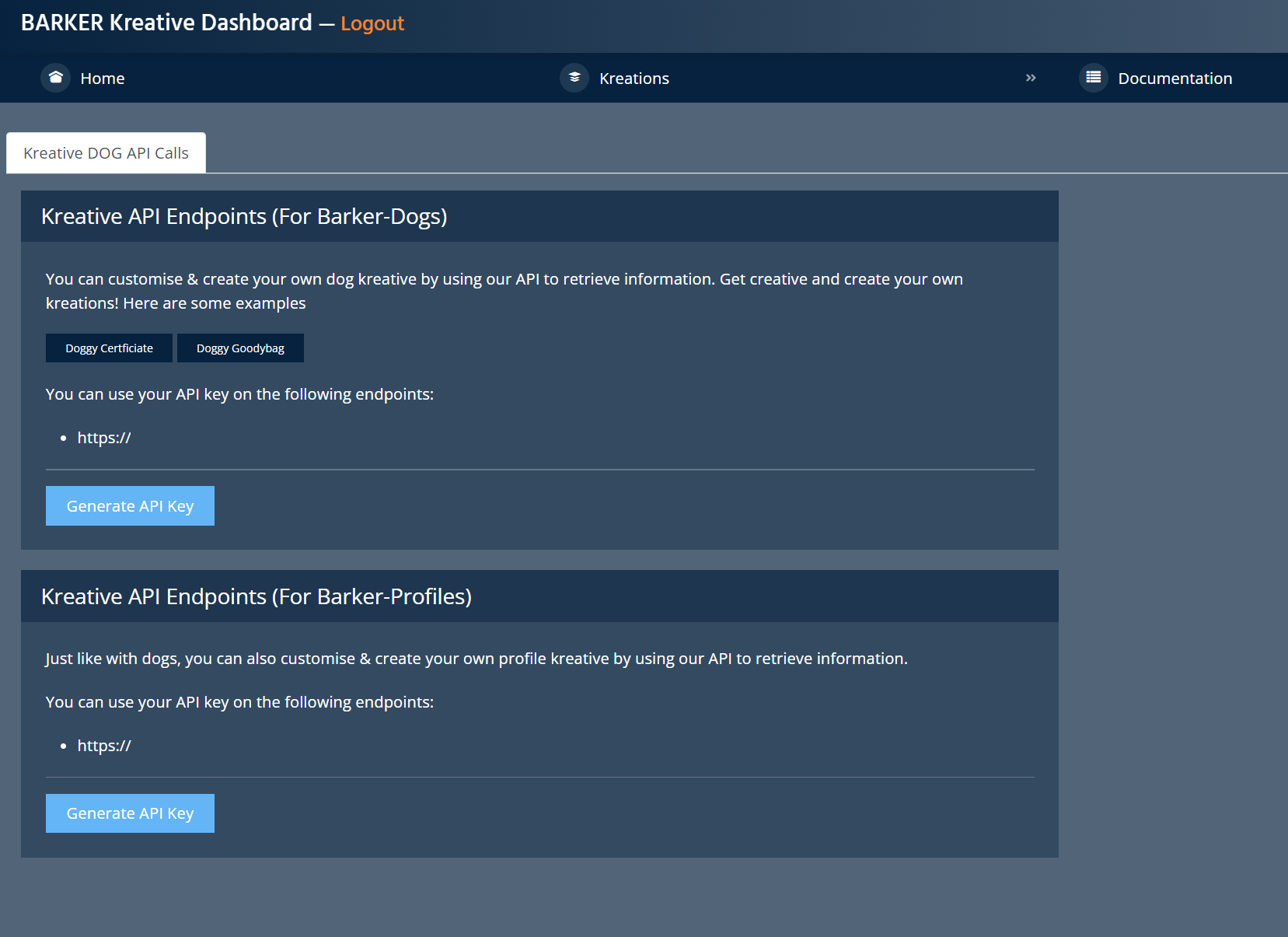
No flags to find here! Instead of being told for example, "Find XSS and try bypass the filter!", you start with zero knowledge on how BARKER functions/works, you just know there are vulnerabilities to find. Your task is to test how the various features work and what they may be vulnerable to. These are real features that function just like a real website would: create an account, login, reset your password, edit your profile, post content, upload photos, create groups & more!
After discovering an issue you are then required to write a report exactly like you would on a real bug bounty platform, and your report will then be manually triaged. We are the only bug bounty training platform to offer a realistic experience with report writing and triage which enables us to get to know you along your journey.
"I love Barker because usually I don't spend enough time in apps and I missed a lot of vulnerabilities. Barker has helped me to think differently and to try something new every day."
 Membership checklist
Membership checklist
Our membership training is 100% hands on and all information needed to aid you with this can be found on our website for free. Before joining you should:
 Your questions answered
Your questions answered
As mentioned to the right, understanding how to use a web proxy tool such as Burp Suite or Fiddler is required. You should be able to confidently monitor HTTPS requests and be able to interact with them and changing data. For example sending a request on Burp suite to the repeater to test further on a certain parameter.
As well as this, knowledge on common web application vulnerabilities will be required before attempting BARKER. Our entire website contains information relating to various vulnerability types, as well as zseano's methodology, and we highly recommend you utilise all of this when testing on BARKER to help you.
Whilst there is a mobile website for BARKER you DO NOT need to know mobile testing as there is no mobile app and it is just a web application.
..a bug bounty hunter! This means applying what you learn on our web applications on real bug bounty programs in the hope for a bounty!
We have three web applications available, BARKER , KREATIVE (apart of BARKER) and FirstBlood. They work just like a real website would in the sense you can register, login, post content etc, and zseano's methodology is all about testing a main web application. The two together combined should be enough to help jump start your bug bounty journey and understand the mindset behind discovering vulnerabilities, as well as constructing an approach and adopting the mindset.
You can find the Top 10 OWASP vulnerabilities across our web applications such as:
You will also discover Insecure direct object reference, XXE, Authorisation Issues, Cross Origin Sharing and Server misconfigurations. There's over 100+ unique vulnerabilities to discover and you will most certaintly be occupied!
After discovering an issue you can then submit a report for triage. When creating a report it is recommended that you include information about what you have discovered such as the vulnerability type, vulnerable parameter, payload, and url affected, as well as information around the issue such as impact, but most importantly including a proof of concept. We should be able to easily replicate the issue described with a step by step process.
Triage can take up to 7 days however once triaged, if your report has been deemed valid then a unique BARKER-ID will be assigned. Multiple IDs can be assigned to one report. The more vulnerabilities you discover the higher the level you reach!
Bug chaining is completely optional. You can submit bugs singular, or you can chain multiple issues together in one report. For example for issues such as XSS you do not need to always chain it to prove the impact (such as showing you could do account takeover) however explaining the impact is recommended as it is best practise for when submitting on bug bounty programs. Sometimes not all XSS have the same impact (unauthenticated XSS for example).
With that said, you can chain something such as XSS to do an account takeover if you wish and create an epic report. Our web applications are your playground to practise what it's like to hunt for bugs and create a report for someone to triage/reproduce, as well as playing with various vulnerability types to see what they can do. Enjoy it, have fun! This entire experience is here for you to play and gain confidence with testing and creating reports!
Yes! Join a welcoming community of like-minded caring invididuals on Discord ready to help you with your hunt on our web applications. We have some extremely talented security researchers ready to help ease your queries or doubts and you can even team up to collaborate on our web applications together. As you reach Level 2 you will be invited to our #hacking-events channel where you can then also team up for our events.
BugBountyHunter membership isn't just about learning, you also join a family.
Please note when joining BugBountyHunter you will receive lifetime access to the discord.
"It is very awesome indeed, allowed me to experience with a target that is similar to real ones, allowed me to interact with this awesome community around it, and built my confidence."