Reaching 1000+ reps on H1 and how you can do it too!
Like any other beginner when I first wanted to get involved with bug bounties, I kept asking people how to get started. While people were happy to share their journey, I kept getting different advice all the time which resulted in this constant state of confusion, which made me think every time 'Should I do this first or that'. Some recommended me to get really good at programming, while some recommended getting into CTF’s first and a few others just recommended me to start hacking plain without doing much of the pre-requisite stuff. I got into this rabbit hole of trying to find the best resource out there and trying to make my path the "most efficient". The problem was I kept delaying and just kept searching for the right “course material” instead of just getting my hands dirty and start hacking right away.
After all of the advice that I’ve received, I thought it was time to put in some work. I wanted to create this article to share the exact steps that I’ve taken to achieve some sort of success in this highly competitive field of bug hunting. I wouldn’t say that I’m very successful, but I’ve been finding some high impactful bugs as of late on the HackerOne bug bounty platform. With a very good solid foundation, I must say that you can at the very least earn some really decent income doing bug bounties part-time.
Like I mentioned earlier, if you ask 10 experienced hunters how to find bugs, you’ll most probably get 10 very different answers. This article is just going to be covering the steps that I’ve taken that worked for me to actively find bugs on some of the promising bug bounty programs. I wouldn’t say it’s the best/efficient way. I’m sure you’ll find similar guides like this as well on people sharing their journey to their success in bug bounties. Depending on your learning style, my approach may or may not work for you but I’m sure at the very least you’ll learn a thing or two that should be helpful in crafting your own path.
This article does assume that you’ve used a web intercepting proxy tool like Burp Suite, as well as some basic knowledge on web application vulnerabilities. If not, I'd recommend going through some resources out below that explains some of the web app vulns.
https://medium.com/@jen_strong/the-request-response-cycle-of-the-web-1b7e206e9047 https://www.bugbountyhunter.com/vulnerability/?type=xss https://www.bugbountyhunter.com/vulnerability/?type=csrf https://www.bugbountyhunter.com/vulnerability/?type=open_redirect https://www.bugbountyhunter.com/vulnerability/?type=ssrf https://www.bugbountyhunter.com/vulnerability/?type=sql https://www.bugbountyhunter.com/vulnerability/?type=command_injection https://www.bugbountyhunter.com/vulnerability/?type=idor https://www.bugbountyhunter.com/vulnerability/?type=xxe
While I've understood some of the basic web app vulns out there and why they existed, finding them out in the wild wasn't very easy. I decided to take a look at some of the public programs. Proxying through burp and I can see a lot of requests thrown at me that I was very easily overwhelmed. I decided it was time to take a step back.
With CTF's, I started with HTB, and honestly, the reason was @ippsec. His videos on youtube are worth gold! Although HTB Boxes aren't all going to directly help with bug bounties, there are some interesting exploitation methods you can learn from HTB boxes with the help of ippsec videos,
Ippsec hosts his website called ippsec.rocks where you can easily search for videos, a method I used to use to get some practice for certain bug types was by doing the boxes that contained those bug types, for example, SQL Injection:
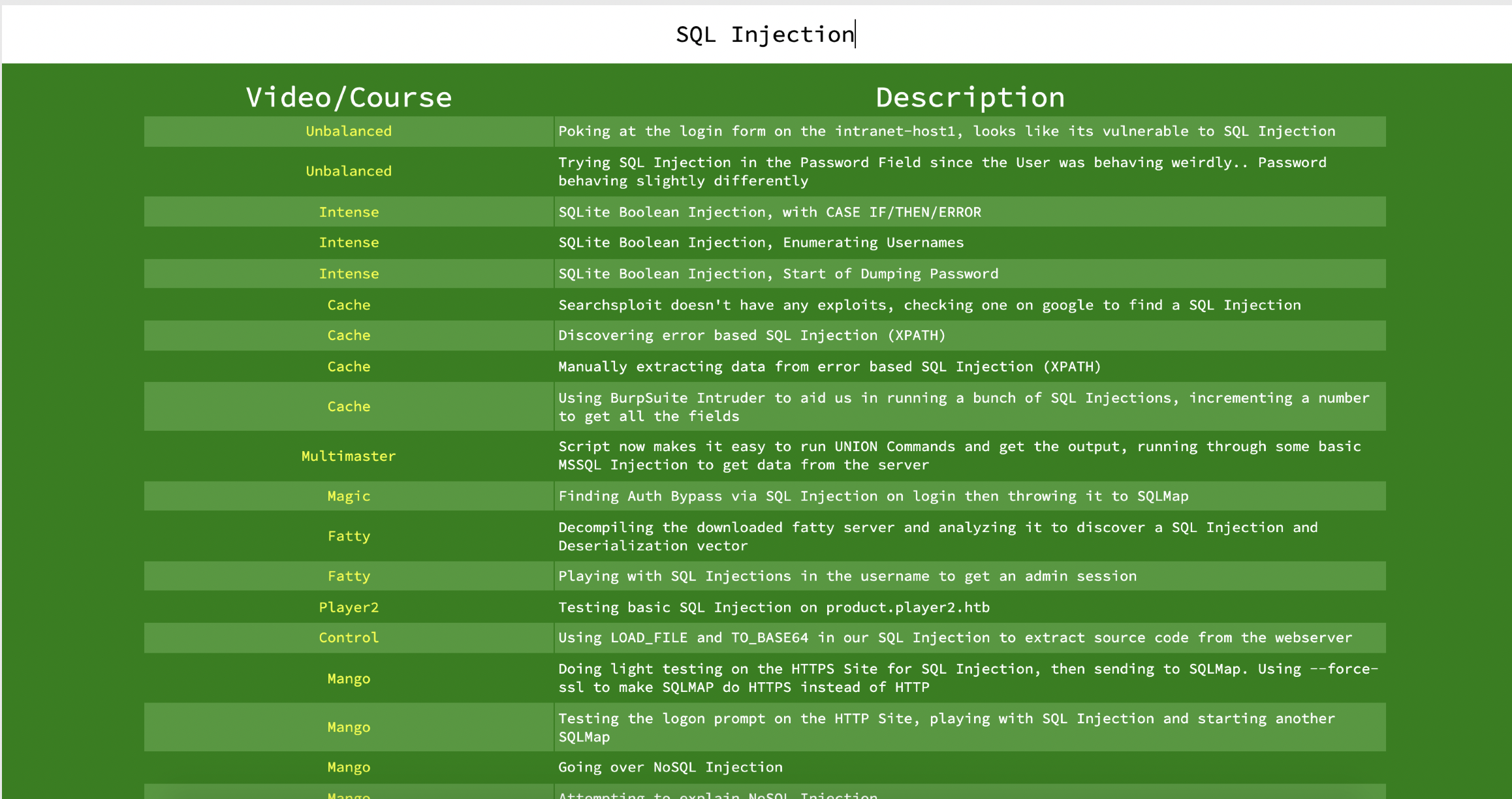
That's a lot of boxes to test your skills in the discovery & exploitation part of SQLi. My approach was to attempt the box and watch the walkthrough if I get stuck. The walkthroughs are very well explained as you get to understand the thought process behind how the payload is created and how to possibly automate them.
Doing that alone, netted me a bug to exploit SQLi on an actual bug bounty program!
Similarly, you can use this to learn some other techniques like SQL Truncation that's less tested. Although not every bug-type will have a lot of walkthroughs, for eg: GraphQL, the idea is to use a combination of all these resources to get the best out of them.
Another important point: Always document and keep notes on all the techniques that you’ve learned and start writing down your own methodology and the way how you approach a particular feature/bug type. This can immensely help build your own checklist when you’re analyzing a real-world target.
My next suggestion would be to watch all zseano's training video's posted on youtube. They're hours long and packed with great info!
Some of the videos will walk you through the old FastFastFoodHacking challenge. Once you've seen the videos, then I'd recommend giving Zseano's playground a try:
https://www.bugbountyhunter.com/playground
They're packed with 20 vulns for you to test your skills!
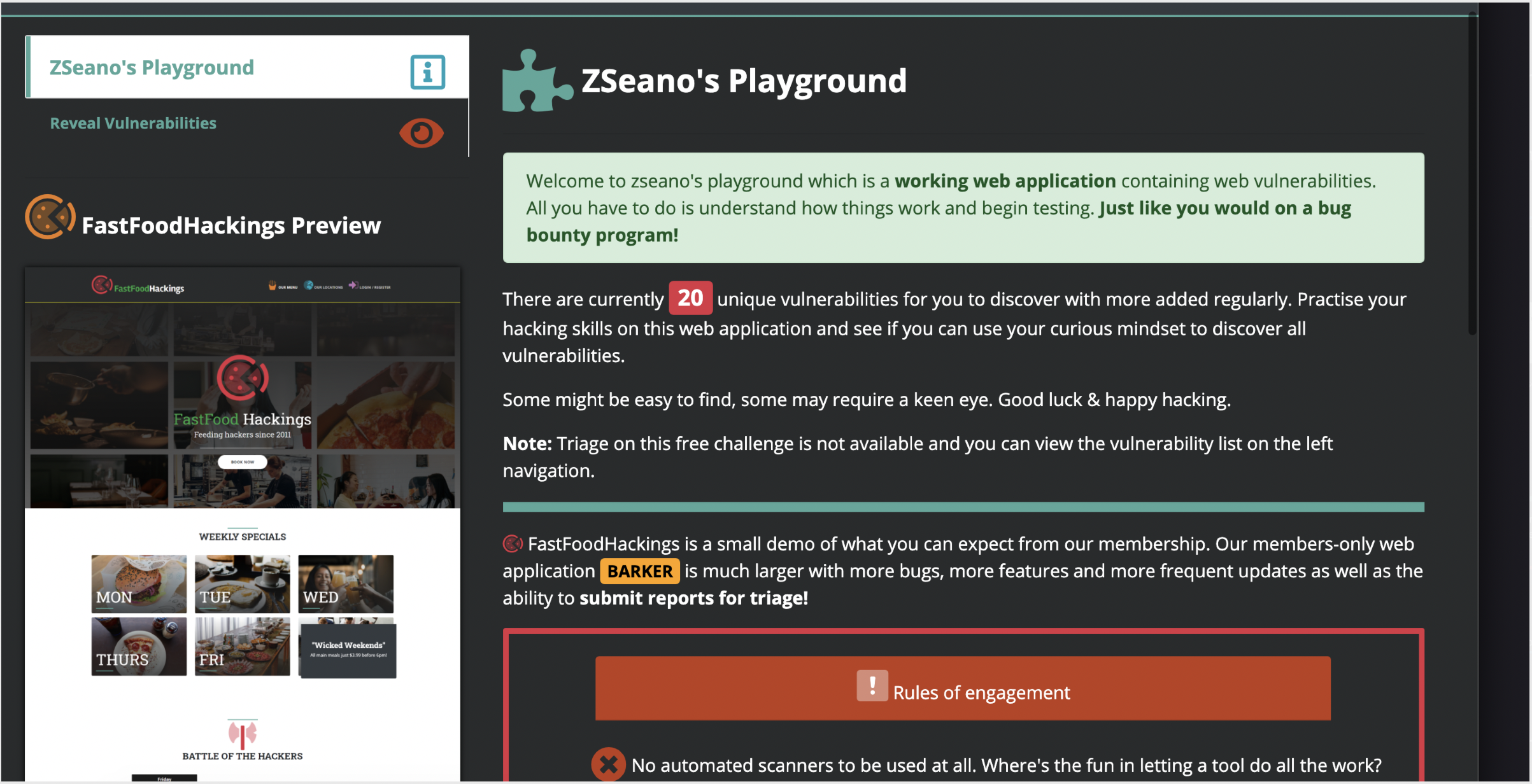
The videos will also walk you through XSS payload building methodology and bypasses, you can then test your skills by doing some challenges on: https://www.bugbountyhunter.com/training/
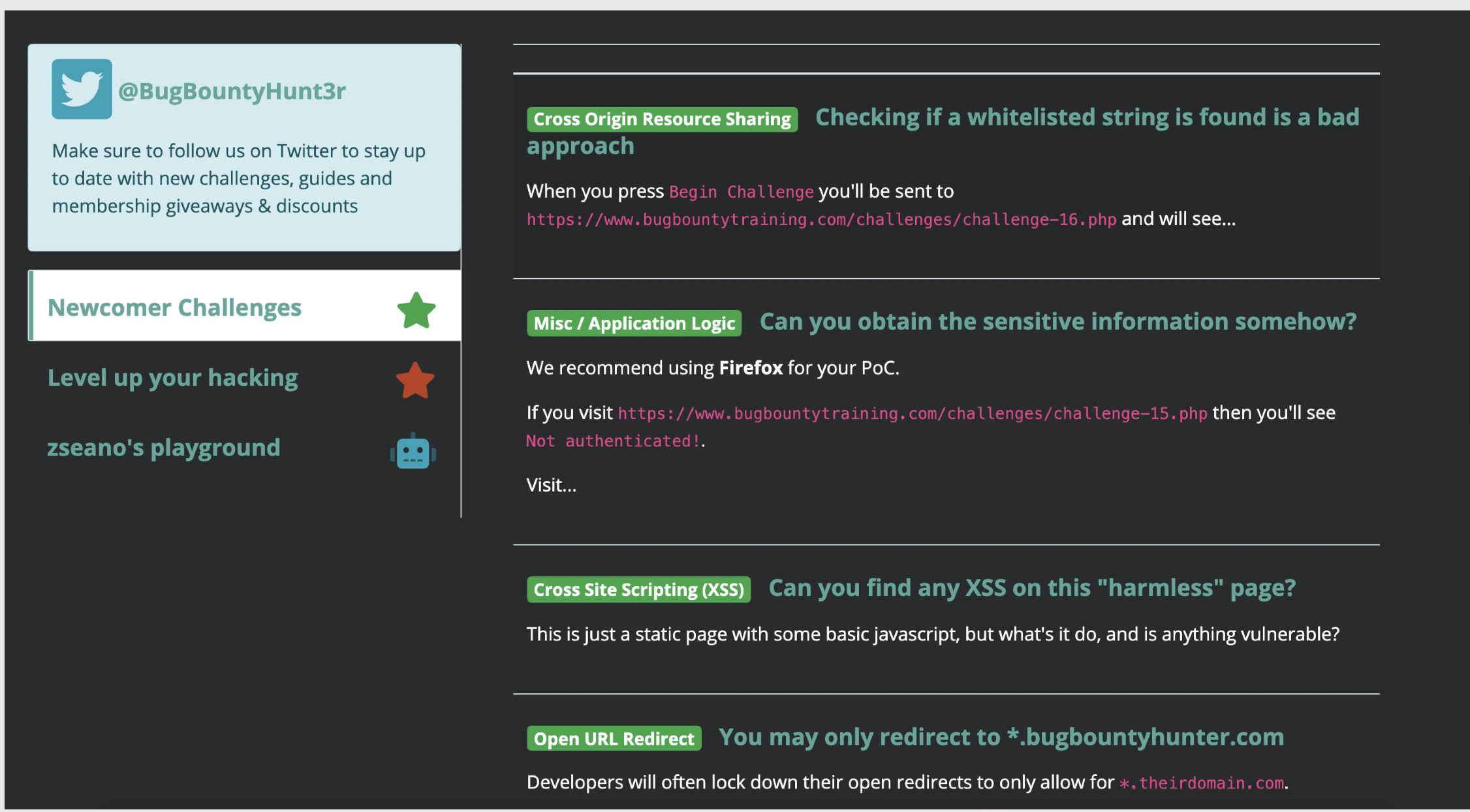
At this point, you should be having some decent skills to start hunting. I'd recommend picking a target and spent an hour every day just testing the functionalities of the website. Noting down, all the functionalities, URLs, and parameters. For more reading on how I take notes, check out this article: https://www.bugbountyhunter.com/guides/?type=notetaking
Your confidence should be a lot better now, depending on the schedule you may have, you might wanna split your time accordingly for learning & hacking. At first, you'd have a lot of your time spent on labs, challenges, and whatnot. But as your confidence increases, slowly you’d want to invest more and more time on hacking targets.
Now that you've learned some techniques on your own, you should've written your thoughts/methodology on how to test certain vulnerabilities. I'd then recommend reading Zseano's methodology (https://www.bugbountyhunter.com/methodology/zseanos-methodology.pdf) thoroughly. Now compare with your own methodology that you've written earlier and update them accordingly as and when you learn about new techniques. I highly recommend creating your own checklist as that is one way to be ahead of the competition.
If you can spare a bit of cash or once you’ve received your first bounty, I highly recommend taking the membership: https://www.bugbountyhunter.com/membership - This is one of the best investments you can make. You are deeply challenged to find vulnerabilities that aren’t very obvious as there are numerous times that you’re going to think that there are no bugs left but in reality, there could be 50 or more vulns that you’ve missed. It has a great growing community, people to ask for help for, and more importantly frequent Hackevents.
HackEvents are basically events where you’re given another target to find vulnerabilities and report during a time period for which you get paid bounties. It tests your skills really well as it mimics an actual bug bounty program. A great chance to make your membership fee back just by participating in hackEvents. To understand more about hackevents, check this out: https://www.bugbountyhunter.com/hackevents/
The process now is to rinse & repeat where you divide the time to learn & hack. As you keep doing it, with enough patience and perseverance, you’ll uncover more techniques and find great bugs on bb programs.
Another thing to keep in mind is to never forget mobile apps, I’d really recommend following this resource and class by @reyammer - https://mobisec.reyammer.io:- it has some interesting challenges for you to play with including videos & slides
InjuredAndroid by @b3nac also contains some real world bugs that you can use it to practice. https://github.com/B3nac/InjuredAndroid
@iamsarvagyaa has compiled a list of Android Security on - https://github.com/iamsarvagyaa/AndroidSecNotes
This contains CTF Write-ups, static code analysis write-ups to HackerOne Reports relating to Android Security, huge props to @iamsavagyaa for compiling the list.
To give you some motivation, following the same approach and resources in this thread, I was able to find some really impactful bugs lately and get into the top 90 day leaderboard.
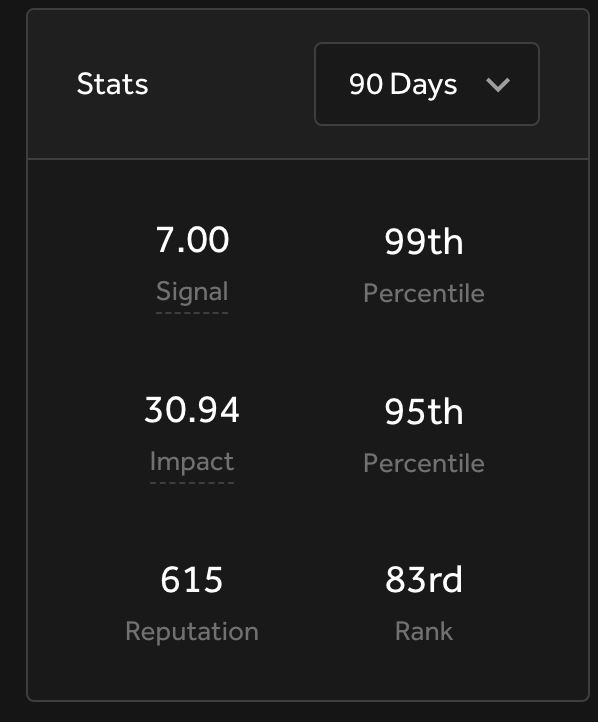
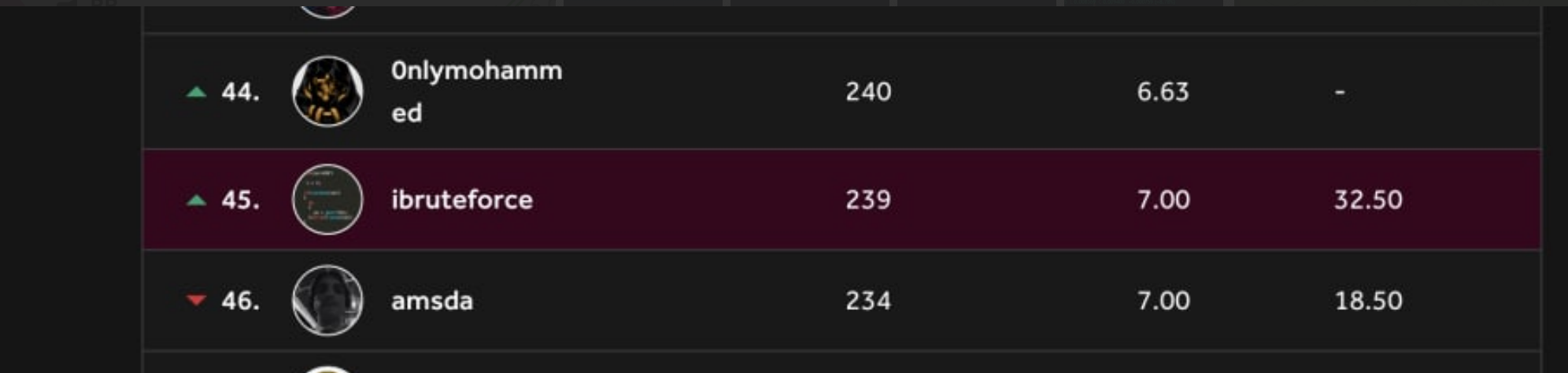
To conclude, I know that’s a lot of resources to take in. Please do not try to do this all at once or at the same time. Also, after one point where you feel comfortable after some basic challenges, you’ll need to manage your time hacking on programs and learning whether that is through articles, challenges, or platforms. With enough perseverance, I’m sure you can pull this off.

 Getting started
Getting started Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Test your knowledge
Test your knowledge Free Web Application Challenges
Free Web Application Challenges Guides for your hunts
Guides for your hunts  ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Useful Resources
Useful Resources  Disclosed HackerOne Reports
Disclosed HackerOne Reports  Our community
Our community Endorsed Members
Endorsed Members Hackevents
Hackevents  Member Articles
Member Articles 