FirstBlood-#113 — Account takeover of a doctor account is possible due to flawed logic in the registration process
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-10, bobbylin Level 4
reported:
Summary
An attacker can takeover the account of a doctor by registering with the same username and reusing the invitation code.
Steps
- Register a doctor account "jomar" and invitation code "F16CA47250E445888824A9E63AE445CE".
- You will see the password of "jomar".
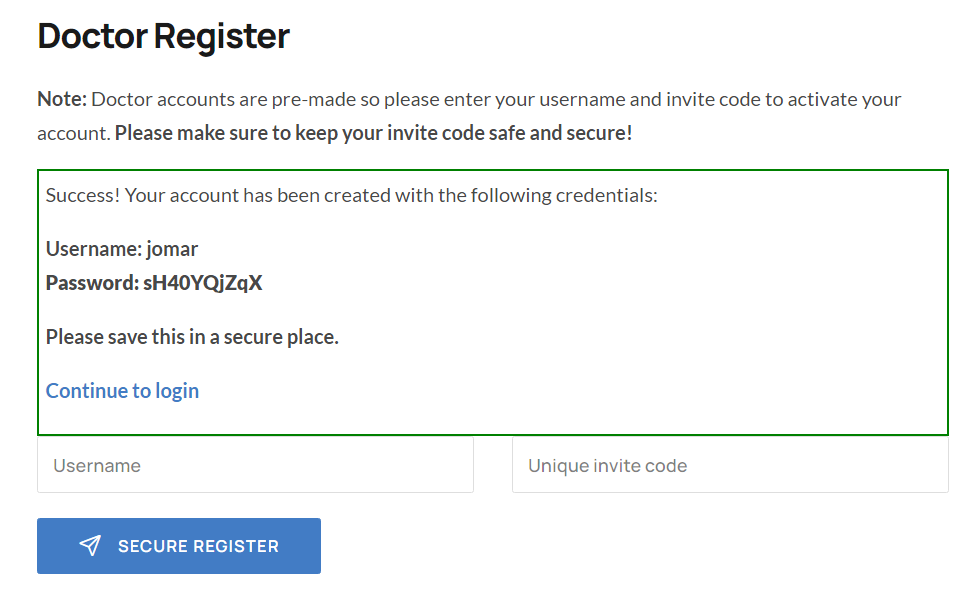
- On another browser, register again as "jomar" with the same invitation code "F16CA47250E445888824A9E63AE445CE".
- You will see that the password of 'jomar' have changed without authorization by the original user.
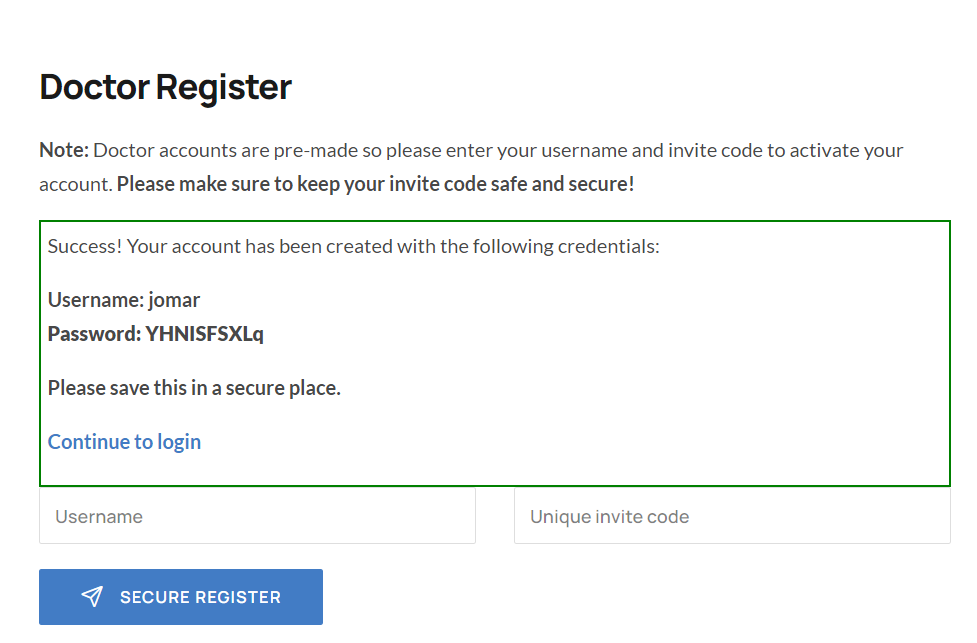
Impact
Attacker can takeover the account of another doctor.
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: register.php
Parameter: username
Payload: jomar
FirstBlood ID: 17
Vulnerability Type: Auth issues
Unintended: An account with the same username can be created which leads to the original account being deleted and replaced with the attackers
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
