FirstBlood-#1283 — Reflected XSS on /book-appointment.html endpoint in the `redirect url` parameter
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-09, mr_xhunt  Level 8
reported:
Level 8
reported:
Summary:
I found the endpoint /book-appointment.html used to redirect to /book-appointment.php, so I used the redirect_url parameter found already and with simple js payload got the xss
Steps to Reproduce:
- Visit the following link with the payload: https://7cac14721157-mrxhunt.a.firstbloodhackers.com/book-appointment.html?redirect_url=javascript:alert(document.cookie)
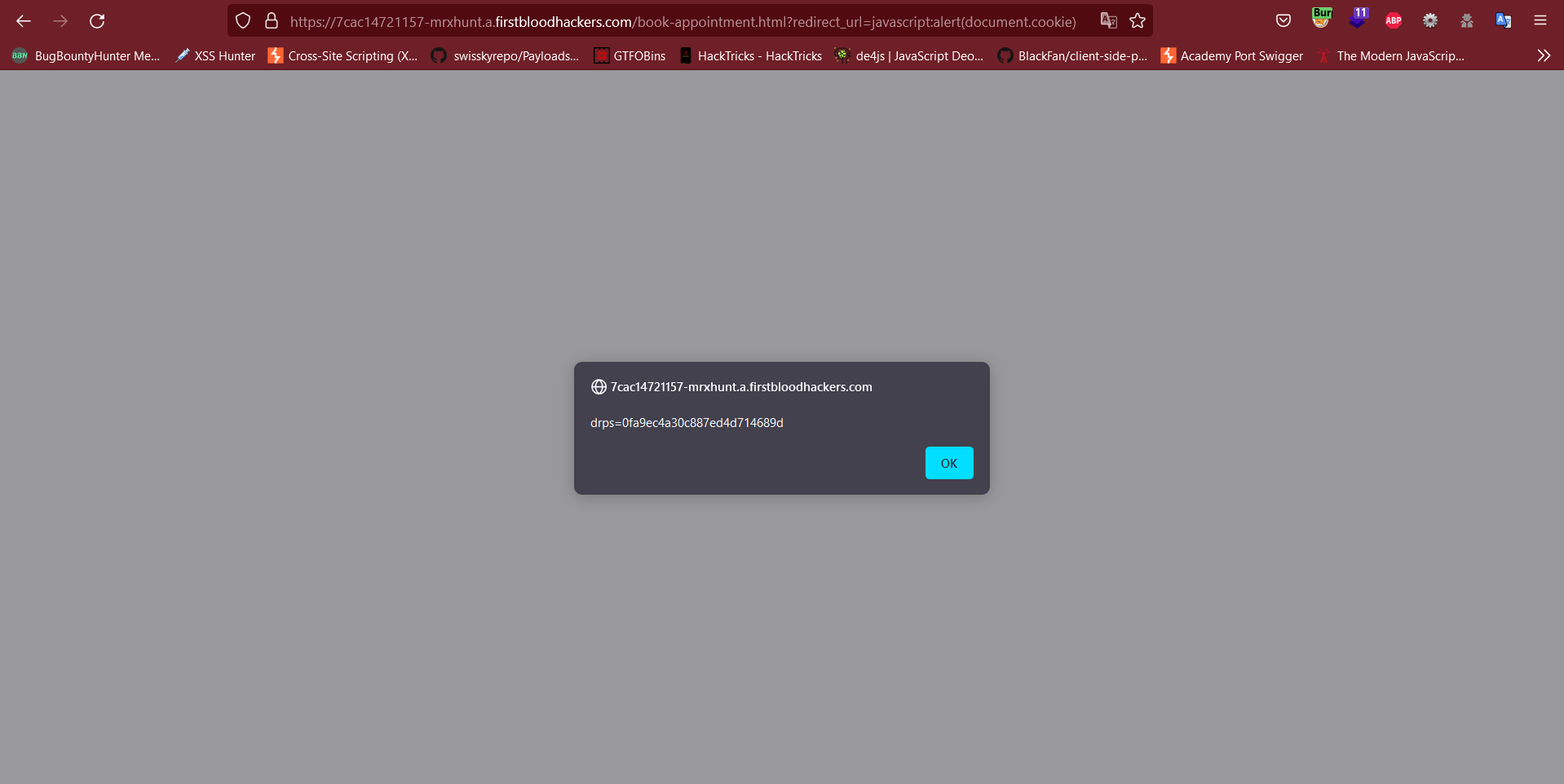
Impact:
The attacker can leak the users cookie and takeover their account.
Underlying Issue
The parameter redirect_url value is accepted without sanitization.
Remediation:
The parameter value must be sanitized before redirect.
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /book-appointment.html
Parameter: redirect_url
Payload: javascript:alert(document.cookie)
FirstBlood ID: 46
Vulnerability Type: Reflective XSS
The endpoint book-appointment.php was introduced to replace book-appointment.html, but code on book-appointment.html introduces an XSS vulnerability via the javascript: URI
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports  Level 8
Level 8