The BugBountyHunter website and membership platform will be closing in the next few days and our website plus membership platform, including all material such as BARKER, FirstBlood etc will become inaccessible. We will be sharing a blog post detailing what's to come in the future and will add a link here when available. Thanks for all your support over the years, i've truly enjoyed mentoring and helping others with their bug bounty journey. ~zseano
FirstBlood-#1772 — Stored XSS on ambulances.php
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-15, veshraj Level 4
reported:
I have discovered a XSS vulnerability affecting the endpoint 'api/ambulances' in the parameter 'select'. The payload requires no filter bypass and is a simple, <img src=x onerror=alert(1)>
You can see a working proof of concept here:
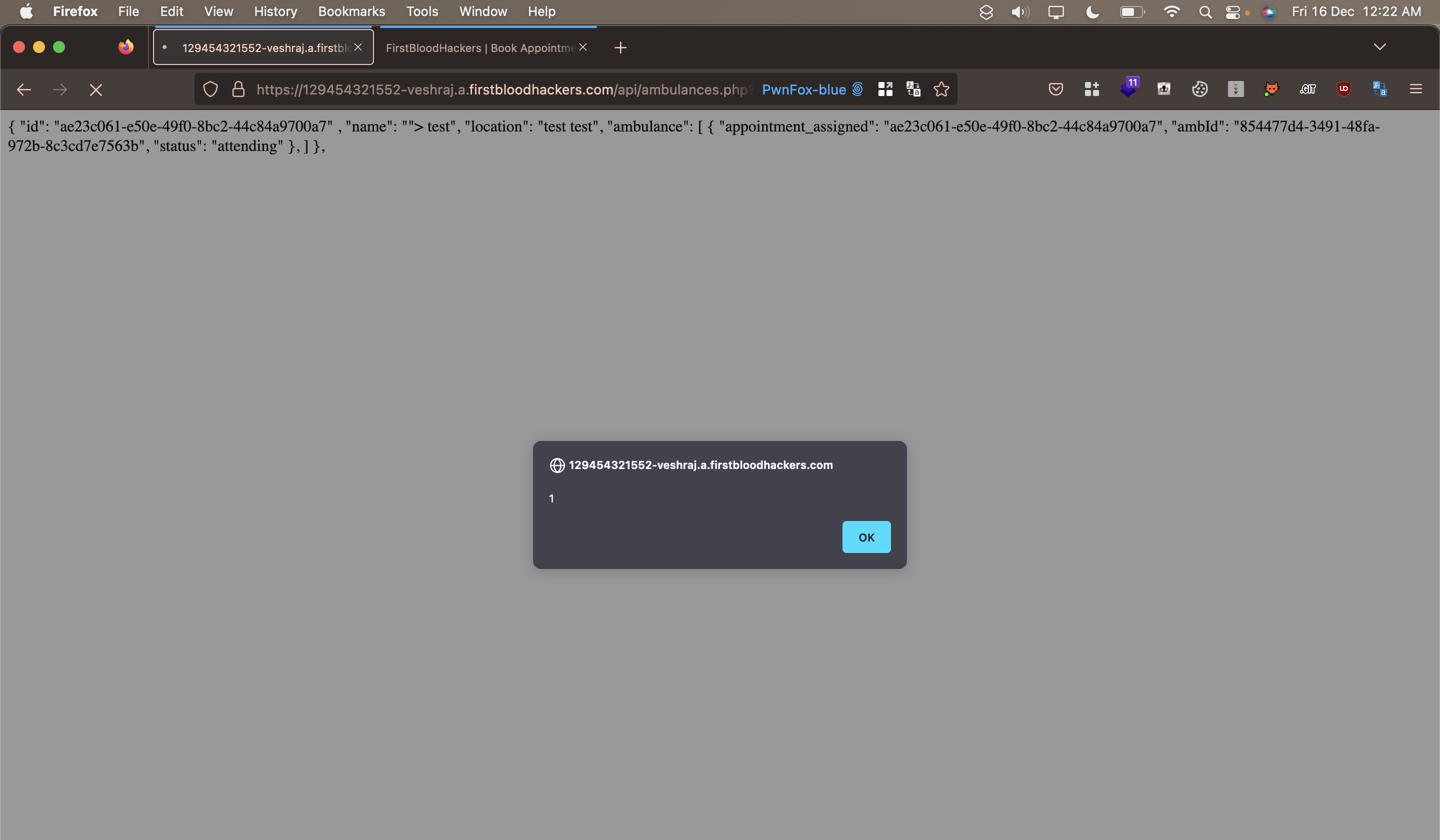
To reproduce:
-
Create an appointment via /book-appointment.php with xss payload on fname and ambulance parameter set to true. (note that there is front end validation on fname parameter which we can bypass by intercepting and changing the value from burp)
-
Now, after step 1, you will get unique AppointmentID which you can use on following URL with select parameter:
https://129454321552-veshraj.a.firstbloodhackers.com/api/ambulances.php?select=<AppointmentID>
You can see that it executes the XSS.
Payload used:"><img src=x onerror=alert(1)>
Impact:
As the session cookies are not protected by HTTPOnly, we can obtain these and achieve account takeover. As well as this, the CSRF token is stored in the DOM which enables us to easily perform actions on behalf of the user.
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /api/ambulances.php
Parameter: select
Payload: n/a
FirstBlood ID: 53
Vulnerability Type: Stored XSS
It is possible to achieve stored XSS on /api/ambulances.php?select={id} via the users first/last name. For this to work the parameter ambulance=1 must be set
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 