Description
Hello :)
As for the other reports this one is created in collaboration with Serizao.
I had initially not submitted this report because I thought it was the same root cause as report #46, but after a second check there is one thing that differs and so I created a new report.
However, if you look at the code of the page /yourappointments.php you can see this piece of javascript code:
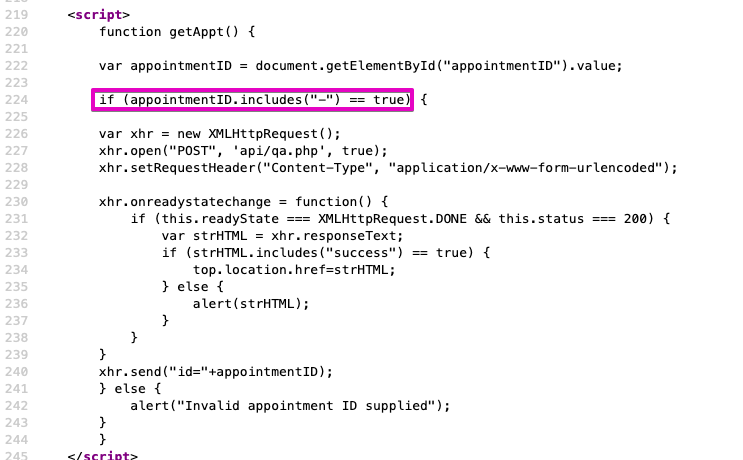
The circled part corresponds to a small client-side check to verify that the submitted ID contains a pull, it sort of verifies that it matches the expected format, i.e. something like XXX-XXX-XXX-XXX
However, if we play the request directly into burp suite, this check will not be performed and it is therefore possible to submit anything. At this point an XHR query will be performed and will display the response if it is valid otherwise "Invalid appoitment ID!"
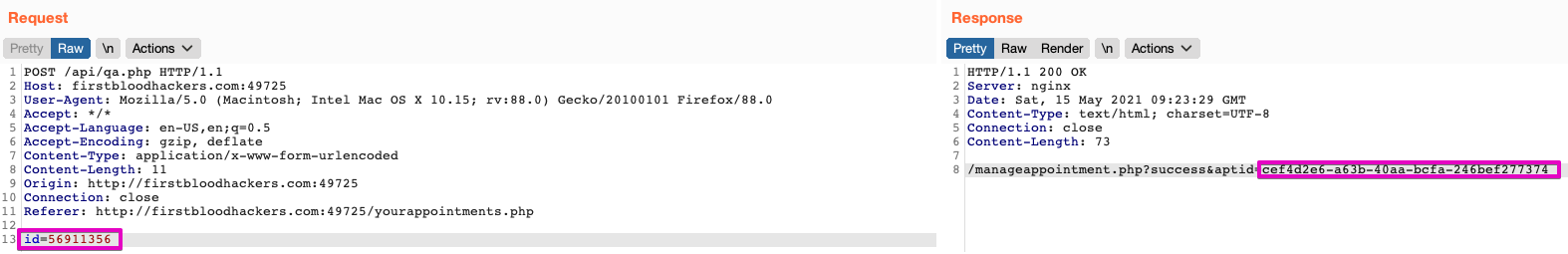
It is therefore also possible to submit here the reservation number with a simple ID which will be mapped to its complex equivalent.
For ex, the simple ID 56911356 correspond to the complexe ID cef4d2e6-a63b-40aa-bcfa-246bef277374.
Impact
- It is therefore possible to access another user's reservation by iterating on the ID and also to modify/cancel his reservation.
- With this bug, it is also possible to obtain the stored XSS through the message parameter on the admin panel via the reservation of another user (cf bug #208
Remediation
- Do not limit yourself to a client-side verification and also perform a server-side verification
- Try to use as much complex IDs (GUID) as possible as in the user part and do not map between a "simple" ID and a "complex" ID
- If possible add a second factor to validate that the reservation belongs to the user (such as validating the date of birth)
- Set up a system of request limit or captcha (recaptchav3 for example) in order to limit abusive requests
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
