How I found this Vulnerability
A doctor can login into his account and logout as well.

While logging out and intercepting the request, I saw a parameter called ref in the url.
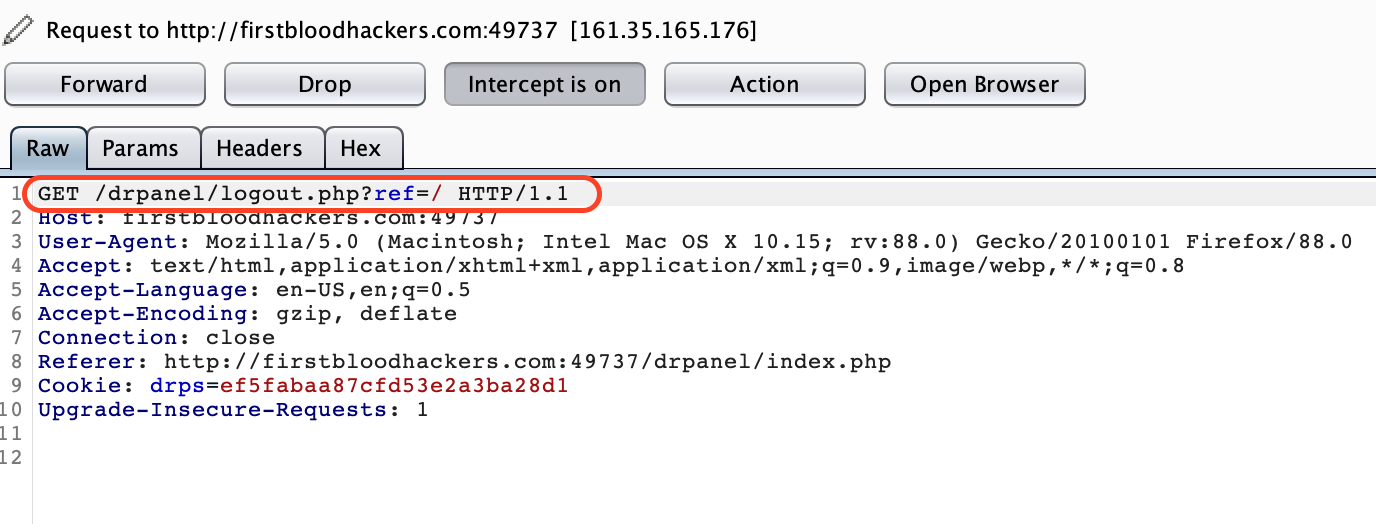
Then I thought, what if I used the same parameter on login page as well.
Here comes the interesting part.
I quickly browsed to login page and added ref parameter with a value sanjay and the following is what amazed me.

I saw a hyperlink getting added on the page, quickly checked sourcecode and this is what I saw.
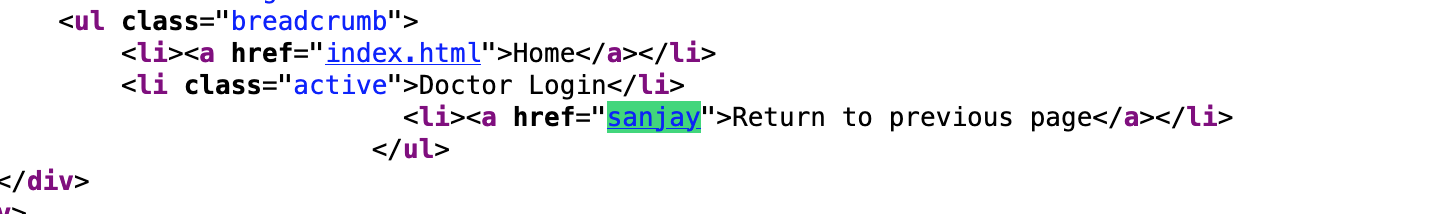
So, my ref value reflected in href attribute.
Next steps: How I built my payload
Attempt 1 : Come out of tags
I tried coming out of that tag so I can build my own tag with a payload. No luck 😔.

Attemp 2: Inject javascript:confirm'1' as the value of href
I injected payload letter by letter to check if there is any filter.
Inject - j

Similarly I appendeda and v

Next I appended a to jav and boom! java got filtered to empty string.

I learnt from its behavior that all java strings are being converted to empty strings.That too its recursive.
By recursive I mean, even if you give jajavava , the following happens.
jajavava -> ja{empty string}va -> java -> empty string.
So, I had to think of some other way, I cannot put java together.
Then I got this idea, what if I use tab parameter %09 between jav and a.
I tried.

and it worked.
Note: Tab parameters like %09 gets resolved without tab while the browser parses HTML i.e jav{tab}a gets resolved to java while page loads.So, we successfully injected java.
Now I appended my remaining payload.Aithout any issues it got reflected.

Now, lets go back to login page and test our Payload.

Boom XSS!
Hope you enjoyed my writeup.
Impact
Run malicious javascript and steal user creds.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 









