FirstBlood-#341 — Referer header reflection leads to Reflective XSS
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-25, kinako Level 5
reported:
Dear FirstBlood security team, I found a vulnerability on your service.
I hope this report will help you.
Summary
The endpoint /login.php has Return to previous page element.
This href attribute in a tag reflects Referer header's value, it causes Reflective XSS.
Vulnerability Description(PoC)
First of all, to set a malicious value in Referer header access to such a URL like https://1ed9de2f9883-kinako.a.firstbloodhackers.com/doctors.php?ref='/onmouseover="alert(document.cookie)"/a='
Note: if you have a problem in URL encoded letters, you can use proxy tool to capture the request to reproduce.
Next, go to /login.php and move your mouse cursor on Return to previous page.
Then, you can see popup alert.
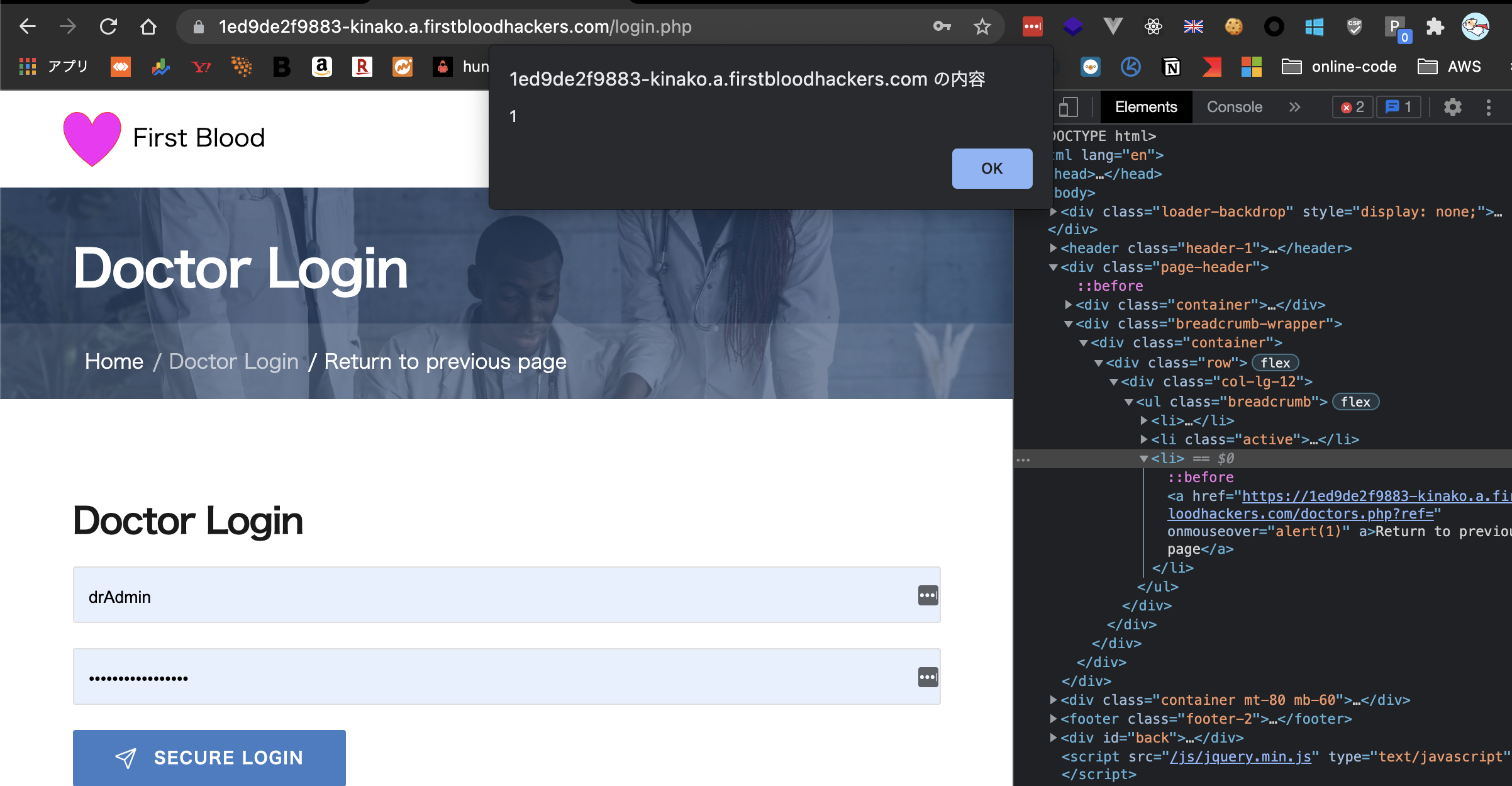
Note
Impact
- FirstBlood v2 still doesn't have a
HttpOnly flag in Cookie so malicious attackers can steal victim's cookie if Reflective XSS is executed correctly.
- Phishing
Regards,
kinako
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /login.php
Parameter: Referer header
Payload: Referer: https://1ed9de2f9883-kinako.a.firstbloodhackers.com/doctors.php?ref='/onmouseover="alert(1)"/a='
FirstBlood ID: 19
Vulnerability Type: Reflective XSS
The parameter ?ref= on login.php was fixed and instead the use of $_SERVER['HTTP_REFERER']; was used. Patrice tested in Chrome and Firefox and saw it was secure, but some users still use Internet Explorer 10 (governments for example!) and the Referer header is vulnerable to reflective XSS.
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
Nice find, thanks for providing a working PoC and mentioning it only works on IE. Some users reported that the referrer was vulnerable but the payload provided wouldn't work, and no mention of browser. So great work with clear repo steps. Perfect!
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
 Report Feedback
Report Feedback