The BugBountyHunter website and membership platform will be closing in the next few days and our website plus membership platform, including all material such as BARKER, FirstBlood etc will become inaccessible. We will be sharing a blog post detailing what's to come in the future and will add a link here when available. Thanks for all your support over the years, i've truly enjoyed mentoring and helping others with their bug bounty journey. ~zseano
FirstBlood-#468 — [COLLAB with isitbug] Open redirect bypass on logout
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-25, shreky Level 4
reported:
Summary
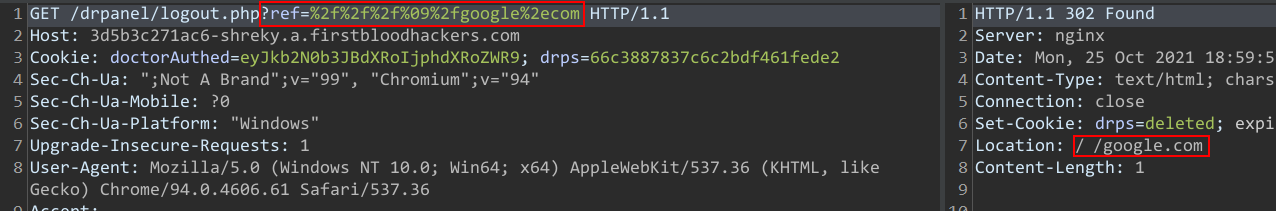
On the logout function (as a doctor) ,parameter ref has been reinforced with some additional filters compared to the previous version of FirstBlood,however me and isitbug(he got the payload working) found a bypass for it.
Steps to reproduce
- Login as a doctor/admin at /login.php
- Access /drpanel/logout.php?ref=
%2f%2f%2f%09%2fgoogle%2ecom
- You'll get redirected to google.com
Impact
Open redirect vulnerability affecting doctors and admins.
Request PoC -->
This report has been publicly disclosed for everyone to view
P4 Low
Endpoint: /drpanel/logout.php
Parameter: ref
Payload: %2f%2f%2f%09%2fgoogle%2ecom
FirstBlood ID: 18
Vulnerability Type: Open Redirect
The open redirect bug on logout.php was fixed but the code still failed to filter out certain characters such as %09 and thus the endpoint is still vulnerable to open redirect. This vulnerability only affects chrome.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 