FirstBlood-#712 — Vaccination-management login panel can be bypassed using sql injection in password paramerter for username=admin.
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-27, vishal Level 2 reported:
Discription: vaccination-management login panel can be bypassed using sql injection in password paramerter for username=admin.
Steps to Reproduce:
-
visit /vaccination-manager/login.php (login.php is not listed anywhere in source code of web page it was just tried)

-
Now Give username =admin and Password = ' or ''=' ( user and password I got using diff technique like : first i tried blank(usrname&password), sql on both field but it didn't worked. So i prefer to provide diffrent diffrent common username. I noticed for userneme admin name diffrent error message appear.
So I was almost certain that admin is valid user but yet password need to entered . Again I tried diff diff common password but It didn't work as well . One more time I tried SQL injection with username admin and IT worked. )

-
All done you will be Welcomed on login panel as admin.
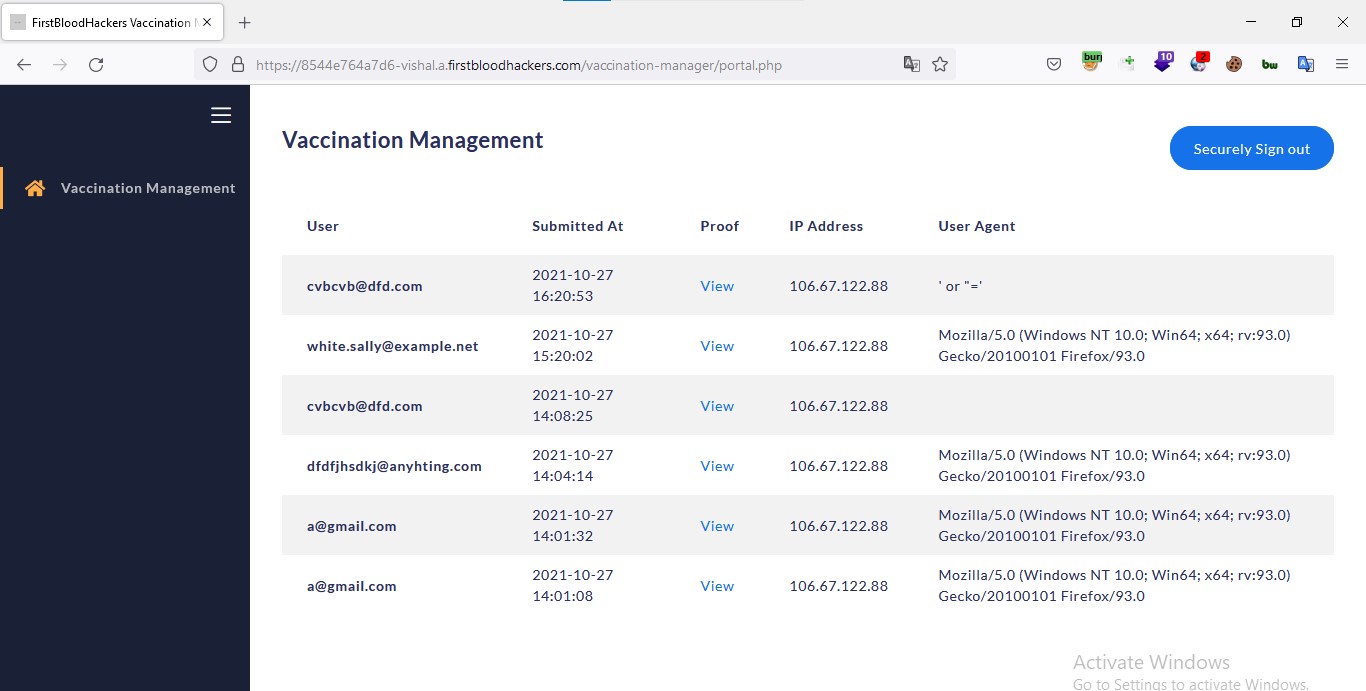
Impact: As it can be seen admin can access vaccination proff , ip address of user & email id It's private information of user's which is very sensitive . All this information will be in hand of attacker in no time if it's not fixed soon.
Lastly if unwillingly i just missed something
Just let me know - Vishal
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /vaccination-manager/login.php
Parameter: password
Payload: ' or ''='
FirstBlood ID: 30
Vulnerability Type: SQL Injection
There is an SQL injection on the vaccination management portal login page which results in the user being able to login as the administrator.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

