Description
To see one's appointment information and to modify/delete it, a complex UUID (which is given to a patient when they place an appointment) is required.
A patient can enter their UUID at /yourappointments.php endpoint. I was able to actually Use numeric Ids, instead of UUIDs on that endpoint. In response I got the UUID of that particular patient's appointment. Then using that UUID I was able to cancel the patient's appointment.
The only thing that may make this bug a lower priority is the fact that attacker had to bruteforce the Id (but that is doable considering the fact that it is numeric Id and I also noticed that they are almost sequential, having gap of 100-200)
Steps to reproduce
- First, make an appointment so that you have a valid UUID for yourself.
- Go to the
/yourappointments.php endpoint and enter your own UUID. Intercept this request using burp.
- Send this request to intruder and bruteforce the
id parameter in the POST body with numeric values.
- Once you hit the correct Id, you will get an endpoint (with UUID).
- Go to that endpoint, you will see the information of patient, and now you can also cancel the appointment by pressing the cancel appointment button.
Note that to actually reproduce this faster, start you bruteforcing from the ID 56910219 as this was the first Id that I found. All other Id ( for existing patients and for new appointments) start after that ID.
How I was able to find those IDs?
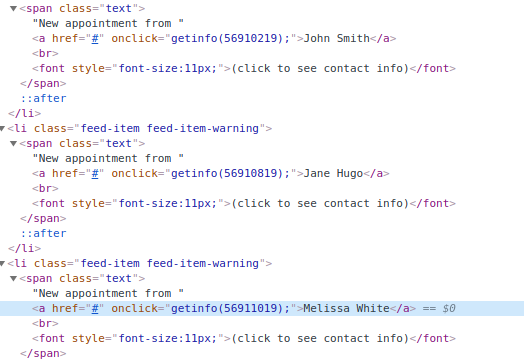
Well as I was provided the admin creds, In the admin panel I realised that instead of UUIDs, simple numeric IDs are being used. With this information, I tried those numeric IDs on the /yourappointments.php endpoint and was able to get the result back, Here is the screen shot from the admin panel showing IDs of appointments:
Impact
This bug is not only leaking the PII of a patient, but also will lead to the cancellation of the appointment, all without the victim's interaction. Such Information is highly sensitive and is affecting the confidentiality & integrity of patient's data.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 