FirstBlood-#77 — PII disclosure using GET request
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-09, thefawsec Level 2 reported:
Description
An administrator can enter the name of a patient (or just a few characters as they will return all matching results) and get the informtaion about them. I was able to get that information without being logged in as administrator by simply changing the POST method to GET.
POC
- Simply visit the following endpoint:
/drpanel/drapi/qp.php?name=sea.
- You will get all patients having the input characters (
sea) in their name.
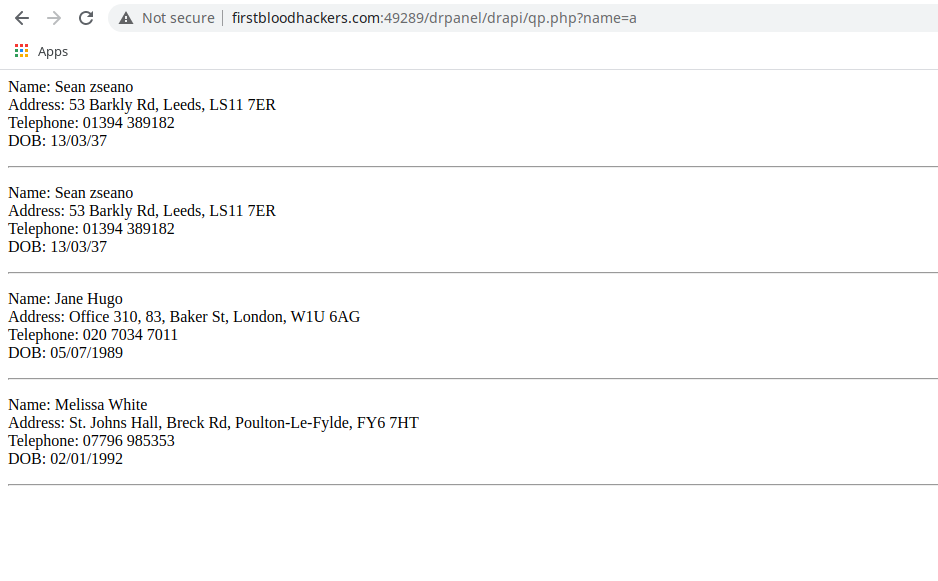
How I was able to find that?
- Using provided
Admin creds, I loged in and searched for a user.
- Intercepted this request in burp.
- The request was POST and there was a cookie header having admin's cookie. I deleted the cookie, but the request failed.
- Out of curosity, changed the request from
POST to GET and deleted the cookie again.
- Successfully got the PII of patients!
Impact
Leaking PII of patients is breach of confidentiality. This information leaked can be used against the patients in many ways. The firstblood hospital ensures the security of personal information of patients. So this is totally against the hospitals policy and claims!
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: drpanel/drapi/qp.php
Parameter: name
Payload: NAME-OF-PATIENT
FirstBlood ID: 12
Vulnerability Type: Auth issues
If the request method is changed from POST to GET, then the endpoint /drapi/qp.php becomes available to ANY user due to an application logic error
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 