Dear Sean,
I was able to identify SQLi vulnerability in Vaccine Management portal which allow any unauthenticated person to gain the access.
First I have noticed that vaccination-manager endpoint has it's own login page. While I try to uncover the login information I noticed that it make two different error messages.
One error message was generated when I entered a none existence user.
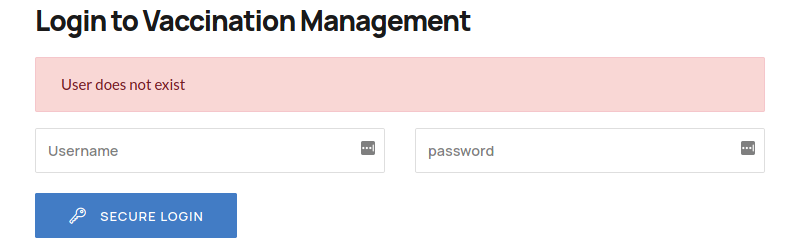
And Other error generate for valid user , but with incorrect password.
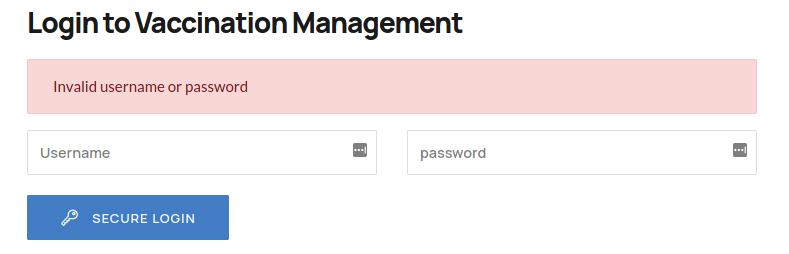
This allowed me to guess the admin is a valid user for this portal. Then I tried to identify the possible password for this user. This effort let me to notice a SQL error when entered a single quotation in the password field.
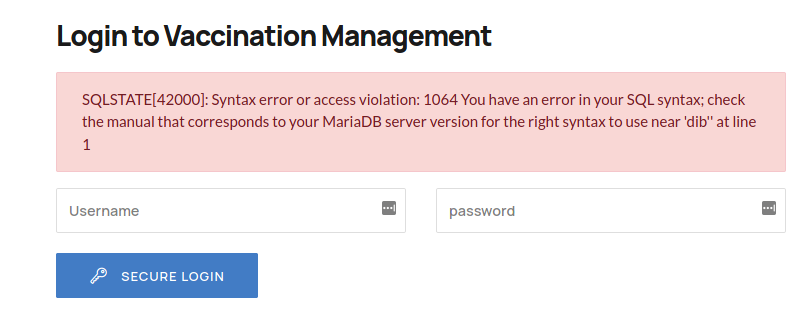
This led to believe that this endpoint is vulnerable to SQLI.
I used simple SQLi login bypass with ' OR 1=1 --[space] and it was success.
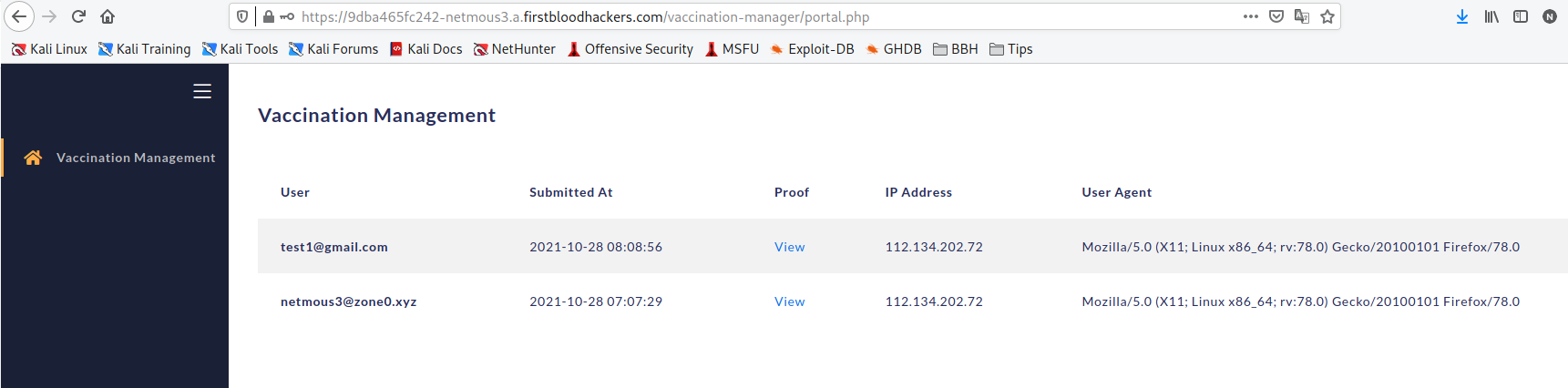
Impact:
Unauthenticated persons allowed to access the patients healthcare reports. In this case, attacker allowed to view patients vaccine proof documents along with his email id and IP address that he used to upload the data.
Remediation: (As in OWASP)
Primary Defenses:
Option 1: Use of Prepared Statements (with Parameterized Queries)
Option 2: Use of Stored Procedures
Option 3: Allow-list Input Validation
Option 4: Escaping All User Supplied Input
Additional Defenses:
Also: Enforcing Least Privilege
Also: Performing Allow-list Input Validation as a Secondary Defense
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


